- #Infosec2025: Channel Bridges Security Skills Gap
- Need to relax? These sound apps do the trick for me - here's how
- Educating Tomorrow's Tech Workforce: A New Map for AI-Era Skills
- A year after testing, these Nothing earbuds are still my favorite I've used
- The Gen AI reset: why CIOs need to reinvent the digital workplace
Attacks against cloud users surged in 2020

Cloud-based user accounts were hit by almost 3.1 million external cyberattacks throughout the year, according to McAfee.
Image: iStock/Melpomenem
The shift to remote work in 2020 forced organizations and employees to become even more dependent on the cloud. But that shift also caught the attention of cybercriminals who were glad to exploit such a dependency. In a report published Tuesday, McAfee looks at cloud-based attacks and malware that took advantage of the new work environment.
SEE: Shadow IT policy (TechRepublic Premium)
For its McAfee Labs Threats Report: April 2021 report, the security provider focused on cyber incidents and malware that occurred during the third and fourth quarters of 2020.
In its analysis, McAfee found almost 3.1 million external attacks on cloud user accounts throughout 2020. Though these types of attacks hit a high during the second quarter, they remained steady in most countries and increased in some over the third and fourth quarters.
Among the 10 countries analyzed in the report, Thailand experienced the highest number of cloud-based attacks last year with more than 600,000 just in the second quarter and around 500,000 in the third quarter and the same number in the fourth quarter. India was next on the list with more than 400,000 such attacks in the second quarter and around 375,000 in the third quarter and again in the fourth quarter. The U.S. was among the least-targeted nations on the list.
The information on cloud-based attacks was based on data from more than 30 million McAfee customers and encompassed all the major industries, including financial services, healthcare, education, retail, technology, manufacturing, energy, real estate and transportation.
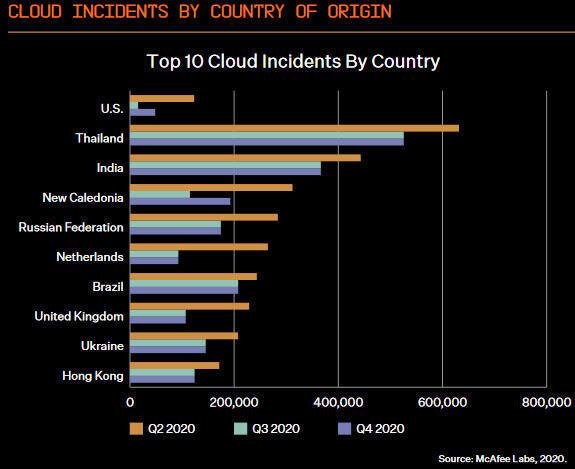
Image: McAfee
Naturally, the coronavirus pandemic played a significant role in cyberthreats during the second half of 2020. Attackers continued to deploy coronavirus-themed phishing campaigns and other attacks, happily targeting workers coping with pandemic restrictions amid the potential vulnerabilities of remote work. For the second quarter, McAfee found a 605% increase in these types of threats, followed by a gain of 240% in the third quarter and 114% in the fourth quarter.
“The world—and enterprises—adjusted amidst pandemic restrictions and sustained remote work challenges, while security threats continued to evolve in complexity and increase in volume,” McAfee fellow and chief scientist Raj Samani said in a press release. “Though a large percentage of employees grew more proficient and productive in working remotely, enterprises endured more opportunistic COVID-19 related campaigns among a new cast of bad-actor schemes.”
SEE: How to manage passwords: Best practices and security tips (free PDF) (TechRepublic)
Other threats increased during the second half of 2020. Ransomware attacks observed by McAfee grew by 69% from the third to the fourth quarter as REvil, Thanos, Ryuk, RansomeXX and Maze proved themselves as the top ransomware families.
Mobile malware rose by 118% in the fourth quarter. The HiddenAds, Clicker, MoqHao, HiddenApp, Dropper and FakeApp strains were the most prominent malware families. MacOS malware jumped by 420% in the third quarter but then declined around the end of the year. PowerShell threats grew by 208% in the fourth quarter as McAfee caught several attacks that tried to inject malicious code into legitimate running processes.
In total, McAfee found an average of 588 threats per minute during the third quarter, a number that rose to 648 threats per minute in the final quarter.
“As your enterprise meets new challenges in 2021, it remains imperative that workforces—both onsite and remote—be alert to potential threats emerging from seemingly routine communications,” the report said. “Remind and test your workforce’s resistance against clicking unverified links and engaging external email attachments. As this report confirms, ransomware and malware targeting vulnerabilities in work-related apps and work processes were active in the last half of 2020 and remain dangerous threats capable of taking over networks and data, while costing millions in assets and recovery costs.”


