Australian Data Breach Costs are Rising — What Can IT Leaders Do?

There’s a good reason Australian organizations are more conscious than ever of the risk of a data breach in 2023. In recent years senior IT professionals, along with many everyday Australians, have witnessed a number of high profile incidents, including the shock hacking of large local telecommunications provider Optus and leading health insurer Medibank.
Businesses are also more aware of the cost. According to IBM’s Cost of a Data Breach Report 2023, the average cost of a data breach in Australia has grown by 32% in five years to AU $4.03 million (US $2.57 million). This is being led by the financial services sector, with an average breach cost of AU $5.56 million (US $3.55 million), followed by the tech and education sectors at AU $5.06 million (US $3.23 million) and AU $4.61 million (US $2.94 million) respectively.
As the risk of data breach incidents rise, IT leaders are in a position to minimize the cost of a data breach by implementing DevSecOps, utilizing AI and automation, prioritizing incident response planning and testing, streamlining data breach discovery and taking out adequate cybersecurity insurance for when the worst happens.
Jump to:
What does the Australian data breach landscape look like in 2023?
Massive data breaches have been a feature of news headlines in Australia in recent years.
In September 2022, the hack of local telecommunications provider Optus saw cybercriminals steal the personal data, including identity documents, of 9.8 million Australians in an incident that many claimed woke Australia up to the threat of cybercrime. The incident, which impacted a large portion of the population, resulted in Optus being the subject of a class action lawsuit and Optus being labeled the least trusted brand in Australia by market research firm Roy Morgan.
This was followed in the same year by an equally high-profile attack on large local health insurer Medibank. This attack resulted in hackers putting the details of 9.7 million current and former Medibank customers on the dark web. Other recent breaches include an attack on financial services firm Latitude Financial in March 2023 — the largest data breach in Australia’s history — which exposed the personal information of 14 million past and present customers.
SEE: Discover more about how data breaches are affecting the healthcare industry.
The Office of the Australian Information Commissioner’s September 2023 report on Australia’s Notifiable Data Breach scheme found there were 409 data breach notifications from January to June 2023. This was down 16% on the previous six months, despite the period including Australia’s biggest data breach and the most data breaches recorded in a month (100 notifications in March). Most breaches (70%) were malicious or criminal attacks. Human error resulted in 107 notifications, 46% of which were caused by an email being sent to the wrong person.
As the National Data Breach scheme does not capture foreign organizations operating in Australia, the actual impact of breaches on Australian customers could be much larger.
How much have data breach costs been rising in Australia?
Australia has experienced a 32% spike in data breach costs over five years to AU $4.03 million (US $2.57 million). IBM’s 2023 research report, conducted by Ponemon Institute, found detection and escalation costs have reached AU $1.68 million (US $1.07 million) — the highest portion of local breach costs — indicating a shift towards more complex breach investigations.
Data that was breached was most often stored across multiple types of environments (32%), followed by private cloud (28%) and on-premises (21%). The two most common attack types were phishing scams (over 22%) and stolen or compromised credentials (over 17%).
Although mega breaches like Optus, Medibank and Latitude Financial are relatively rare, they are much more expensive than average data breach costs. The IBM report found that, globally, the cost of a mega breach of between one million and 10 million records cost organizations around US $36 million, while a breach of between 10 million to 20 million records could leave organizations with a total breach cost of up to US $166 million.
Overall, Australia is the 13th country or region in the world when ranked by data breach costs. IBM found the global average cost of a data breach has reached an all-time high of US $4.45 million. The average cost increased by 15.3% from US $3.86 million in 2020, with the U.S. experiencing the highest average data breach cost of $9.48 million, followed by the Middle East (US $8.07 million) and Canada (US $5.13 million). The average cost per record involved in a data breach has risen from US $146 in 2020 to US $165 today.
What costs can you expect to incur due to a data breach?
The total immediate and longer tail costs of a data breach are difficult to estimate. IBM uses an activity-based costing approach that breaks down costs along the four common stages of the data breach life cycle, based on extensive research on real data breaches. These stages include detection and escalation, notification, post-breach response and lost business.
- Detection and escalation: These costs include investigative activities, assessment and audit services, crisis management and communications to executives and boards.
- Notification activities: Determination of regulatory requirements, communication with regulators, engagement of experts and communications are the costs in this phase.
- Post-breach response: Help desks, credit monitoring and identity protection services, issuing new accounts or credit cards, legal expenses, product discounts and fines.
- Lost business: These costs include attempting to minimize loss of customers, the cost of acquiring new ones, ongoing reputational damage and diminished goodwill.
Following the Optus and Medibank data breaches in 2022, Australia introduced a new Privacy Act amendment that could make data breaches more expensive in the future. The Privacy Legislation Amendment (Enforcement and Other Measures) Bill, which was targeted at organizations that fail to take adequate care of their customer data, raised the maximum penalties for serious or repeated privacy breaches from AU $2.22 million to AU $50 million.
How can Australian companies minimize data breach costs?
The decisions IT and business leaders make, as well as the strategies they deploy around their data and security, can heavily influence the cost they pay if a data breach does occur (Figure A).
Figure A
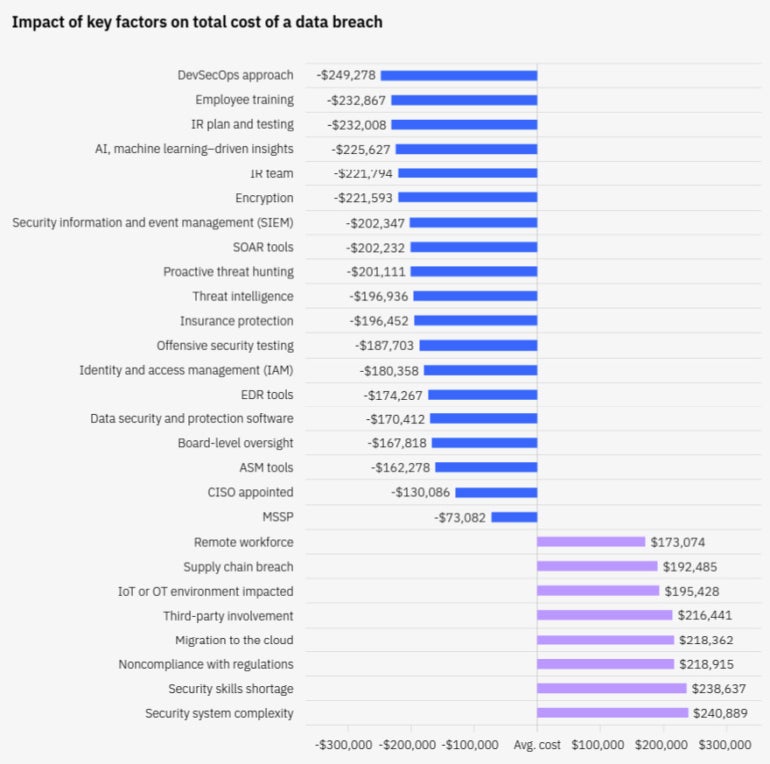
Having the right cybersecurity skills in your organization — or tapping external partners for this expertise — can also help reduce data breach costs. IBM’s report identifies a number of factors present in organizations that are likely to reduce the cost of a breach. On the other hand, not implementing them can lead to higher breach costs.
Accelerate DevSecOps adoption
A high level of DevSecOps adoption resulted in the largest cost savings during data breaches around the world. Because it places an emphasis on security testing as part of the software development process, organizations with high DevSecOps adoption saved US $1.68 million compared to those with low or no adoption.
Aim for a shorter breach life cycle
Organizations that want to minimize costs should aim to keep breach life cycles short, as the time to resolve an incident is integral to financial impact. Breaches with identification and containment times under 200 days cost organizations US $3.93 million, while those over 200 days cost US $4.95 million — a difference of 23%.
SEE: How to avoid a data breach by protecting data in transit.
Deploy security AI and automation
AI and automation had the biggest impact on the speed of breach identification and containment. IBM found Australian organizations that did not utilize security AI and automation in combating cyber threats experienced breaches costing on average AU $2.14 million more than those that deployed these technologies extensively.
Prioritize incident response planning
Cost savings were achieved by organizations with higher levels of IR planning and testing. Organizations with high levels of IR planning and testing saved US $1.49 million compared to those with low levels. The IBM report found that IR planning and testing was a highly effective tactic for containing the cost of a data breach.
Call in law enforcement
Excluding law enforcement from a ransomware incident in particular can lead to a higher eventual cost from the data breach. IBM’s results found that, while 63% of respondents said they involved law enforcement in a ransomware incident, the 37% that didn’t paid 9.6% more and experienced a 33-day longer breach life cycle.
Consider investing in cyber insurance
While not a substitute for cybersecurity maturity and preparedness, cyber insurance can help businesses directly cover the cost of data breach incidents, including forensic investigations, data restoration, customer notification and rectification as well as indemnification of penalties imposed by government regulators. That said, the Insurance Council of Australia said only 35%–70% of larger businesses had standalone cyber insurance in 2022.
Taking a proactive approach to data breach cost reduction
An interesting finding from IBM’s Cost of a Data Breach Report 2023 was that, among organizations that suffered a data breach around the world, only 51% were planning to increase cybersecurity investments as a result. In fact, a likely outcome is that the costs of a data breach will end up being passed on to an organization’s customers: 57% of respondents said data breaches led to a subsequent increase in the pricing of their business offerings.
The most obvious way for Australian IT leaders to minimize data breach costs, including to their brand and reputation, is to prevent a breach from ever occurring. There’s no doubt organizations with a mature cybersecurity posture are the most likely to prevent attacks — or discover them quickly. However, even mature organizations have no excuse to relax; only a third of attacks IBM investigated were identified by an organization’s internal teams and tools.

