How to Delete Old Accounts Containing Personal Information | McAfee Blog
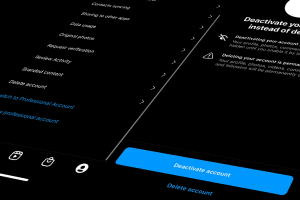
Your digital footprint grows with every internet account you make. While your old Tumblr account may be fun for reminiscing, dormant accounts are actually one of the most significant sources of user data on the internet. These accounts can be used by data brokers or third parties to access your personal information. To improve your data security, it’s good practice to remove public-facing information by deleting unused accounts. Simply put, having less personal data stored…
Read More