- The free iPhone 16e deal at Visible is still available. Here's how to claim yours
- I compared the two best Android phones right now - and it was pretty dang close
- Forget Chrome: Why Firefox's new vertical tabs are such a productivity game-changer
- This midrange OnePlus phone was a steal at full price - now it's on sale
- I wore a low-cost, OTC continuous glucose monitor for two weeks - what I learned
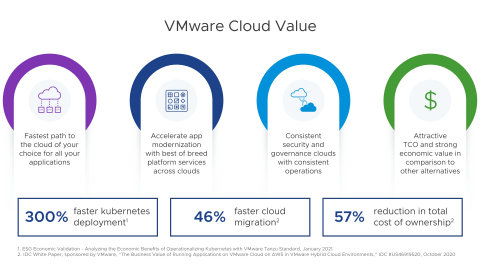
VMware Helps Customers Move to the Cloud With Flexibility and Speed
News Detail With VMware Cloud, customers modernize apps with better economics and less risk Company unveils tech previews at VMworld 2021 to showcase the future of VMware Cloud PALO ALTO, Calif.–(BUSINESS WIRE)– Organizations today are driven by the urgency to go fast and digitize. Multi-cloud is now the model for digital businesses seeking to achieve rapid transformation. VMware enables digital … Tue, 05 Oct 2021 00:00:00 With VMware Cloud, customers modernize apps with better economics…
Read More