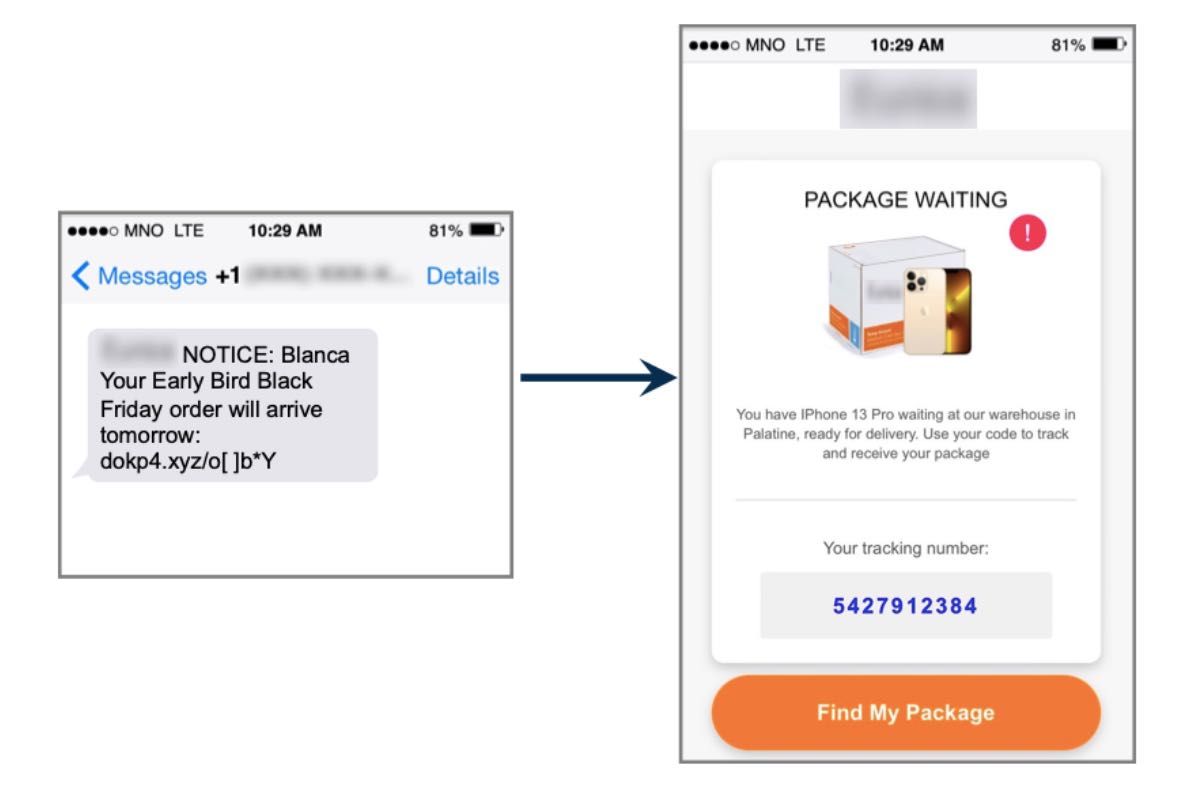
Smishing attacks see a sharp increase ahead of Black Friday
The amount of text phishing or smishing attacks have almost doubled when compared to last year’s holiday shopping season as cybercriminals are increasingly preying on Black Friday and Cyber Monday shoppers. According to Proofpoint, over two-thirds of all SMS messages sent worldwide are related in some form to either an order delivery or consumer retail brand. As consumers have become more familiar with interacting with businesses over text messages, cybercriminals have jumped at the opportunity…
Read More