- 8 ways diversity and inclusion help teams perform better
- AI has grown beyond human knowledge, says Google's DeepMind unit
- Microsoft still has a massive Windows 10 problem - and there's no easy way out
- Midnight Blizzard Targets European Diplomats with Wine Tasting Lure
- AI 시대의 또 다른 과제 ‘데이터 자신감 격차’··· IT 리더가 관리해야 할 이유
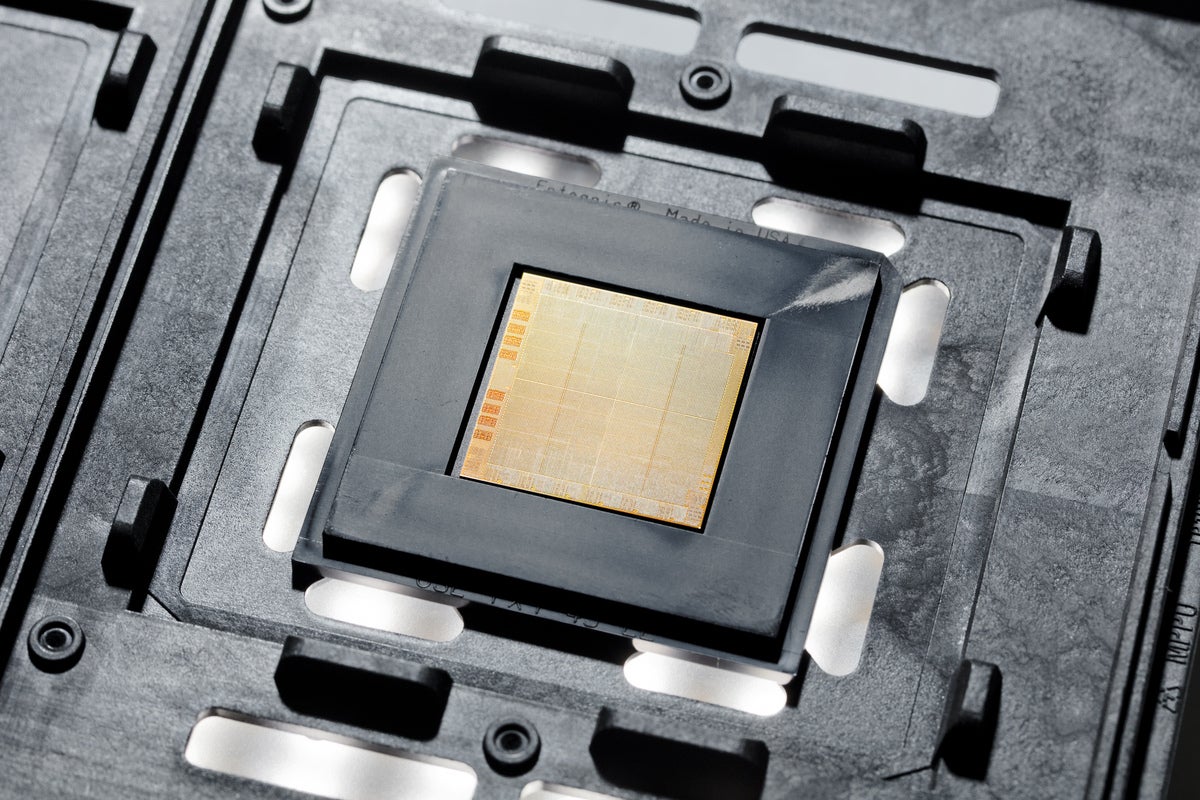
IBM intros new generation of IBM Power servers
IBM is keeping the faith for Unix just like it is for mainframes. It has announced a new Unix-based server, the IBM Power E1080, the first in a family that is based on the POWER10 processor. IBM announced the POWER10 processor last year. Designed on a 7nm process, it is expected to deliver up to a three-fold improvement in capacity and processor energy efficiency within the same power envelope as IBM POWER9. It features a…
Read More