- If we want a passwordless future, let's get our passkey story straight
- This Week in Scams: $16.6 Billion Lost, Deepfakes Rise, and Google Email Scams Emerge | McAfee Blog
- Proof-of-concept bypass shows weakness in Linux security tools, claims Israeli vendor
- SAP NetWeaver customers urged to deploy patch for critical zero-day vulnerability
- Lenovo targets AI workloads with massive storage update
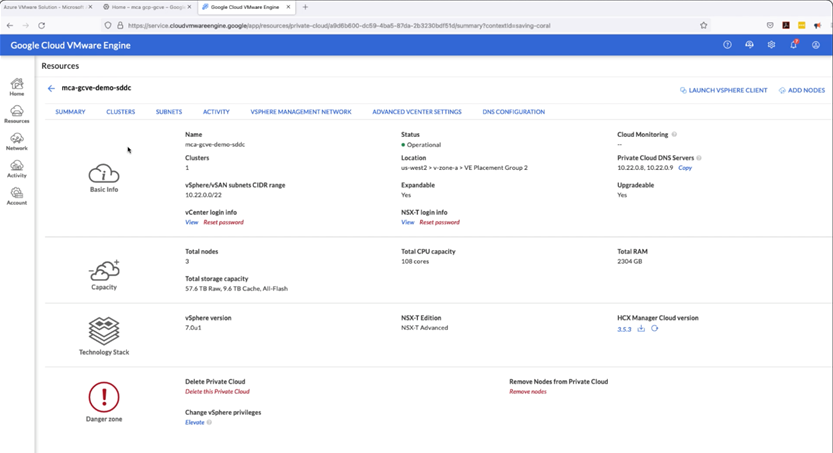
Deploying VMware Clouds in Multiple Clouds – Cloud Blog – VMware
As VMware forges partnership with our Public Cloud Provider Partners (also known as Hyperscale partners), our customers now have choice and flexibility to choose the appropriate Public Cloud Providers, in their preferred geographic region, to build, manage, automate, secure and operate their VMware based workloads. In this article, we’ll demonstrate how easy it is to deploy VMware Clouds (aka Software Defined Data Centers or Private Clouds) in Multiple Cloud Provider Partner environments. For the purpose…
Read More