- How healthy is your home? Ultrahuman's newest device will tell you
- Google just spilled its airfare secrets: here's the cheapest day to book your next flight
- #Infosec2025: Top Six Cyber Trends CISOs Need to Know
- Stop chasing AI for AI’s sake
- I tested Hisense's flagship Mini LED TV, and it left me with no OLED envy (especially at $700 off)
Blurred WFH lines create cybersecurity challenges for companies

A new HP Wolf Security study focuses on shifting cybersecurity threats in the age of remote working as employees use work devices for personal entertainment.
Image: GettyImages/Kelvin Murray
The COVID-19 pandemic led to companies around the globe
transitioning workers to remote work
, introducing new challenges to companies and employees alike.
One of the biggest of these was cybersecurity
and keeping company secrets safe with employees no longer protected by corporate firewalls.
On Wednesday, HP released its “Blurred Lines and Blindspots” study through its newly introduced HP Wolf Security integrated portfolio of hardware, software and services designed for the new normal. The global IT and remote work study illustrates cybersecurity risks in the age of virtual collaboration where the home can also double as the office as more people work from home. KuppingerCole analyzed the report and found that globally in 2020, endpoints connected to the internet were experiencing 1.5 attacks per minute.
SEE: Security threats on the horizon: What IT pros need to know (free PDF) (TechRepublic)
“As the lines between work and home have blurred, security risks have soared and everyday actions such as opening an attachment can have serious consequences,” said Joanna Burkey, chief information security officer at HP, in a press release. “Without all of the pre-pandemic sources of visibility of devices, and how they are being used and by who, IT and security teams are working with clouded vision.”
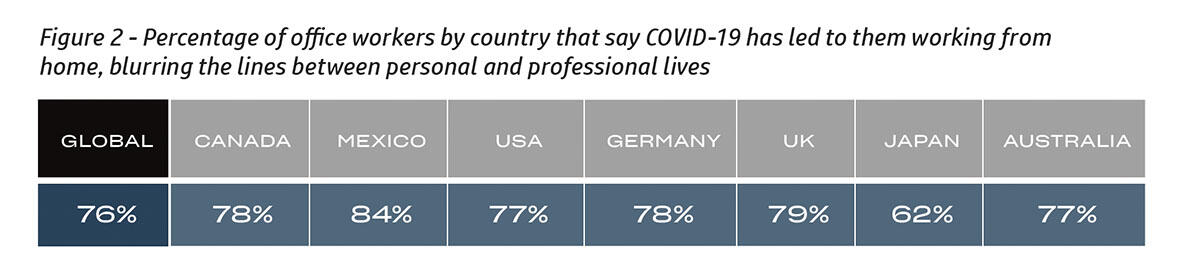
Image: HP Wolf Security
More than three-quarters of office workers (76%) said the lines between their personal and professional lives have been blurred during the coronavirus pandemic. The report said this blurring of personal and professional space has “in effect” merged “work and home into a single environment.”
Various security risks at play
This merging of worlds presents a number of cybersecurity risks; especially with the introduction of work devices into the private home.
Half of office workers said they view these company devices as “their own personal device” and a similar number (46%) said they use work devices for “life admin.” Compared to pre-pandemic behavior, one-third of office workers (33%) said they “download more from the internet” and this number jumps to 60% for people between the ages of 18 and 24.
About one-quarter of office workers said they play games on their work devices more compared to pre-pandemic behavior and this number jumps 16% among parents with children between the ages of 5 and 16. About one-third of office workers (36%) said they stream online services on their work devices.
SEE: Juggling remote work with kids’ education is a mammoth task. Here’s how employers can help (free PDF) (TechRepublic)
During the coronavirus pandemic, many schools and universities have adopted remote learning curricula. For many, the home has pulled double-duty as a remote office as well as a virtual classroom. Over the last year, nearly six in 10 office workers (57%) with children between the ages of 5 and 16 said they use work devices for homework and virtual learning more often.
Fourfold increase in cybercriminal activity
In 2020, the FBI reported a fourfold increase in cybercriminal activity during the early months of the coronavirus pandemic. The report pointed out that the World Economic Forum said that between February and April 2020 there was a 238% increase in global cyberattack volume. Much of this could have been due to employees no longer being protected behind a company firewall.
In a press release, HP Wolf Security said that cybercriminals are “taking advantage of these shifting patterns to tailor their phishing campaigns.” Over the last 12 months, more than half of ITDMs surveyed (54%) had “seen evidence of a higher number of phishing attacks” and nearly half (45%) said they’d seen “evidence of compromised printers being used as an attack point.” The vast majority of ITDMs (91%) feel as though “endpoint security has become as important as network security” and said they now allocate more of their time on endpoint security compared to two years ago.
Nearly nine in 10 ITDMs (88%) said they were concerned that workers downloading non-IT-approved software for their workday increased the risk of a cybersecurity breach.
“More than half (51%) of ITDMs have seen evidence in their company of compromised personal PCs being used to access company and customer data in the past year. This is a huge risk that could lead to exposed company data, reputational damage, non-compliance and loss of customer trust,” said Ian Pratt, global head of security for personal systems at HP.
Zero Trust as a solution
According to the study, a new approach is needed to build a distributed, hybrid workforce. The attack surface is larger than ever with digital and data transformation. IT and security teams are trying to protect their organizations, but there are a lot of battles to fight.
The most secure option is the
Zero Trust principle
, which meant to trust nothing, to only give access to resources based on context. This means user, device, location and security posture. It involves devices and elements on the endpoint itself, such as firmware, application security, integrity of the OS and the account or user accessing data, according to the study.
Methodology
The study is based on findings from a YouGov online survey from March 17-25, 2021 of 8,443 adults in the U.S., the UK, Mexico, Germany, Australia, Canada and Japan who used to be office workers, and worked from home the same amount or more than before the pandemic. It is also based on findings from a Toluna survey of 1,100 IT decision makers in the UK, the U.S., Canada, Mexico, Germany, Australia and Japan. The survey was conducted online between March 19 and April 6, 2021.
The study also is based on “The 2020 Cybersecurity Threat Landscape for Remote Workers as a Result of the COVID-19 Pandemic” report from KuppingerCole in March 2020. The report was used for context and analysis of the changing work landscape in 2020 due to the pandemic. Threat data captured within HP customer Sure Click virtual-machines, and analysis from the HP Threat Intelligence team was also used.


