- I recommend the Pixel 9 to most people looking to upgrade - especially while it's $250 off
- Google's viral research assistant just got its own app - here's how it can help you
- Sony will give you a free 55-inch 4K TV right now - but this is the last day to qualify
- I've used virtually every Linux distro, but this one has a fresh perspective
- The 7 gadgets I never travel without (and why they make such a big difference)
Bose Reveals Ransomware Attack Impacting Staff
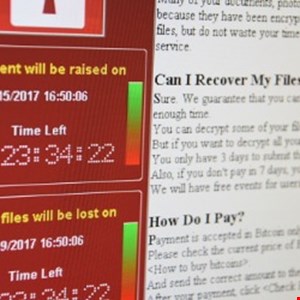
Bose has told regulators that a sophisticated ransomware attack back in March led to unauthorized access of personal information on current and former employees.
The US audio tech giant told the New Hampshire Office of the Attorney General that it first detected the ransomware back on March 7 2021. However, nearly two months later, on April 29, it found that human resources files were accessed.
“The personal information contained in these files include name, Social Security Number, and compensation-related information,” it continued.
“The forensics evidence at our disposal demonstrates that the threat actor interacted with a limited set of folders within these files. However, we do not have evidence to confirm that the data contained in these files was successfully exfiltrated, but we are also unable to confirm that it was not.”
The firm said it had engaged third-party experts to scour the dark web for this data, to check if it is being actively used by cyber-criminals, and is also working with the FBI.
“Bose has not received any indication through May 19, 2021 its monitoring activities or from impacted employees that the data discussed herein has been unlawfully disseminated, sold, or otherwise disclosed,” it added.
Only a small number of staff were affected and the firm is not thought to have paid the ransom.
However, it disclosed to the regulator a long list of remedial actions taken by its security team to mitigate the risk of a worse attack in the future.
This included: enhanced anti-malware, logging and monitoring; blocking of malicious IPs linked to the threat actor; changing passwords for all end users; and changing access keys for all service accounts.
Robert Golloday, EMEA and APAC director at Illusive, praised Bose for its transparency.
“Kudos for not paying a ransom and for having the appropriate backups in place. With that said, the time to put in controls for early detection and prevention of lateral movement is before these attacks occur, not after,” he added.
“It’s another unfortunate example of an ever-widening criminal enterprise.”

