- I recommend the Pixel 9 to most people looking to upgrade - especially while it's $250 off
- Google's viral research assistant just got its own app - here's how it can help you
- Sony will give you a free 55-inch 4K TV right now - but this is the last day to qualify
- I've used virtually every Linux distro, but this one has a fresh perspective
- The 7 gadgets I never travel without (and why they make such a big difference)
Bronze Optis: Innovative Technologies at Black Hat

By Olivia Gallucci, Cybersecurity Reporter, Cyber Defense Magazine
I interviewed approximately sixty industry leaders from over forty companies who attended Black Hat. Although this article series—The Optis—can be read as a traditional Black Hat recap, I specifically highlight twenty-one companies that stand out and whose growth I recommend watching.
Rochester Institute of Technology’s Cybersecurity Club, RITSEC, inspired the metrics I used to analyze and rank companies. Specifically, I adopted RITSEC’s motto, “Security Through Community,” while examining each company’s ability to promote social good, inclusion, and innovation inside and outside of the company. Furthermore, I referenced materials—public demos, open-source code, and publications—to determine the accuracy of the company’s claims and the span of its communal reach, public contributions, and social good.
Given Cyber Defense Magazine’s awarding of unicorns (“a private company with a valuation of over $1 billion”) and that Olympic sailing occurred during Black Hat, I created a conceptual framework—The Opti Series—to highlight innovative and socially conscious companies at Black Hat USA 2021 (UserGuiding). The Opti Series contains three articles: bronze, silver, and gold. You can learn about the judging criteria I used for the Opti Series here or scroll to the end of this article.
Axis Security
Dor Knafo, Co-Founder and CEO of Axis Security
Gil Azrielant, Co-Founder and CTO of Axis Security
Axis Security offers a secure access service edge, protecting originations by analyzing application-layer traffic. Clients use its software and cloud platform in tandem to monitor company networks. Its software handles client services and resource access by instructing the client when access is unexpected or discouraged.
Axis Security built its technology in-house to streamline policy and vendor relationships. Its solutions include secure partner access for third parties, merging and acquisitions, cloud migration, and enabling remote work environments. Axis Security’s most innovative technology is its cloud-based VPN replacement, Application Access Cloud. The platform provides its clients an easy and safe connection to any device without ever touching the clients’ apps or networks.
Axis Security exemplifies global citizenship by leveraging open-source works and contributing to open-source communities. One of the open-source projects Axis Security uses and contributes to is WireGuard, an open-source virtual private network.
Learn more: Dark Reading News Desk talks to Axis Security
CyberSaint
Padraic O’Reilly, Co-Founder and CPO of CyberSaint
CyberSaint is a software as a service company securing critical infrastructure and other highly regulated industries. Their goal is to understand customers’ cybersecurity risk profiles to prevent future attacks.
CyberSaint created the CyberStrong Platform, an automated solution that continuously analyses real-time telemetry to perform compliance and risk assessments across standards such as NIST, CIS20, NERC-CIP, and many others. CyberStrong allows clients to make better business decisions by ranking their risk and compliance posture internally, geographically, and industry-wide. Its creativity draws from its ability to take regulatory regiments used in governance risk and compliance and implement those standards across their risk management program in a way that enables cybersecurity resilience. It does this through its patented natural language processing (NLP) technologies, intuitive user interface, and executive reports.
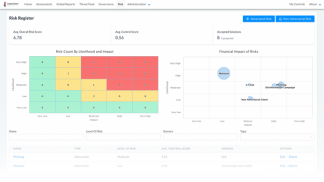
CyberSaint’s Risk Register. Used with the permission of CyberSaint.
CyberSaint analyzes all types of data sources—feeds, proprietary and open-source intelligence, and threat information—with their NLP to optimize hardening systems. CyberSaint uses its NLP technology to leverage telemetry from applications, creating static mappings to controls by implementing the application and dynamic mappings to controls based on data feeds. This NLP also is used to automate crosswalks, using a customers’ existing control scores to fulfill requirements across any set of frameworks or standards within seconds in an “assess once, use many” fashion. Furthermore, CyberStrong helps clients understand their overall cyber risk and compliance posture, strategy, and security.
CyberSaints contributions to the community include the Making Space in Cybersecurity pledge, pro bono consulting to Massachusetts-based non-profits, and gifting no-cost annual licenses to our healthcare customers amid the COVID-19 crisis.
Mimecast
Jeremy Ventura, Senior Security Strategist at Mimecast
Founded in 2003, Mimecast is a leading email security company. Mimecast combined patented, in-house solutions with external vendor data to create a super solution to detect malicious emails. Its email security solution stops malicious emails from entering or leaving client networks. Additionally, its email security solution is customizable to fit client needs, culture, and threats.
Mimecast is headquartered in the United Kingdom and employs over 1800 security professionals globally. Furthermore, Mimecast is rapidly growing, expecting to hire approximately six hundred employees by the end of the fiscal year 2022.
Mimecast publicly releases its annual state of email security report, which uses survey results from its forty thousand customers and C-level executive interviews. One of Mimecast’s most intriguing findings was that (⅔) of organizations admitted they had an email security incident that led to a ransomware attack and that 52 percent of those organizations paid the ransom.
Future reading: Mimecast’s 2021 The State of Email Security Report.
Nuspire
Jyothish (JV) Varma, VP of Product Management at Nuspire
Nuspire is a managed security services provider (MSSP) founded in 1999. Like most MSSPs, Nuspire provides detection, prevention, and response services. However, Nuspire extends traditional remediation practices; it prevents future attacks via proactive and continual system tuning. Other notable procedures include Nuspire’s human-only technical support and fast onboarding.
Nuspire’s platform was built in-house, using open-source components. Although Nuspire does not deliver open-source software to its clients, it collaborates with open and closed-source vendors to provide clients with a holistic intelligence landscape.
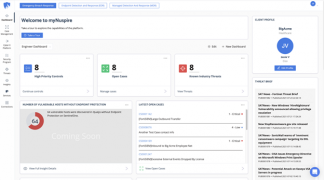
Used with the permission of Nuspire.
Unlike many MSSPs, Nuspire offers clients the ability to automate responses inside multiple portals, allowing clients to use familiar technologies. Furthermore, Nuspire draws insights across platforms (i.e., SentinelOne, Carbon Black, and CrowdStrike) to ascertain the importance of vulnerabilities and intelligence. Nuspire will continue to add more vendor platforms, using market analytics and client feedback to determine which platforms they add next.
Watch Nuspire’s Black Hat webinar here or read about one of Nuspire’s publications at Black Hat: Nuspire Launches New Managed Endpoint Detection and Response (EDR) Service That Supports Leading EDR Technology Providers Including Carbon Black, SentinelOne, and Others.
ThreatX
Founded in 2014, ThreatX is a Web Application and API Protection security company that offers solutions at each layer of the Open Systems Interconnection model. ThreatX offers solutions across web applications and APIs: Web Application Firewalls (WAFs), API security, bot management, and DDoS protection.
ThreatX’s most innovative technology is its automated WAF. ThreatX acknowledged the constraints of non-automated WAFs (i.e., WAFs that use fine-grain rules) calculating false negatives and positives. Fay explained, “Web applications and APIs are under constant assault by highly sophisticated threat actors and techniques. The ThreatX WAAP combines dynamic web application and API security into a single platform, providing actionable insights to reduce vulnerabilities and prevent future attacks.” For example, ThreatX can quickly detect if an API or resource is exposed, which alerts clients of the issue at the time of occurrence. This timeliness alleviates accidental leakages and future breaches.
Read about ThreatX’s press release—ThreatX Announces API Catalog to Provide Enterprises a Clear View of Attack Surface—published at Black Hat.
Trustwave
Darren Van Booven, Lead Principal Consultant at Trustwave; former CISO of the United States House of Representatives
Trustwave is a global managed threat detection and response (MDR) and managed security services (MSS) company that protects SMBs and enterprises around the world from advanced cyber threats. The Trustwave Fusion Platform is a cloud-based XDR platform that serves as the foundation for the company’s managed security services, products, and other cybersecurity offerings. Trustwave particularly excels in protecting organizations operating across the cloud, databases, operational technologies, and the supply chain. It also has leading consulting and professional services, digital forensics, and incident response teams. With the surge in ransomware over the past year, Trustwave has seen a 2x demand for its ransomware preparedness services.
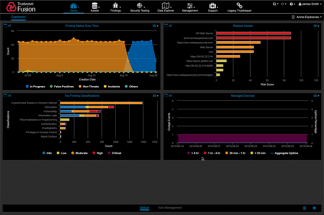
Used with the permission of Trustwave.
Trustwave SpiderLab is the company’s expert research group that produces industry-recognized threat intelligence and frequently publishes reports on newly discovered vulnerabilities. SpiderLab maintains ModSecurity, an open-source, cross-platform WAF engine for Apache, IIS, and Nginx. ModSecurity has a robust event-based programming language that protects a range of attacks against web applications and allows for HTTP traffic monitoring, logging, and real-time analysis.
Trustwave Government Solutions, the wholly-owned subsidiary of Trustwave Holdings, Inc., recently announced it has joined the Cybersecurity and Infrastructure Security Agency (CISA) Cyber Information Sharing and Collaboration Program (CISCP). The overall mission of CISCP is to build cybersecurity resiliency and to harden the defenses of the U.S. and its strategic partners through threat intelligence sharing. Trustwave is also an active contributor to the MITRE ATT&CK framework.
I cannot wait to see more developments out of Trustwave and its SpiderLabs research team. Trustwave’s commitment to offering truly global security and thoughtfulness in its security research contributions are something to emulate.
Further reading: Trustwave Launches First-of-Its-Kind Cyber Supply Chain Risk Assessment Solution for the Pacific Region and Trustwave Recognized as a Top 10 MSSP by Cyber Defense Magazine
ZeroFox
ZeroFox is a security company protecting client brands, reputations, and consumers. ZeroFox’s specialty is tracking impersonation attempts—from individual to nation-state adversaries—by analyzing data on the clear and dark web.
ZeroFox was the first company in the social media protection space and has built many technologies within its platform using NLP and artificial intelligence. ZeroFox recently acquired two security organizations: Cyveillance and Vigilante.
ZeroFox’s platform is customizable, timely, and scalable. Its clients receive direct access to its cloud-processing pipeline, where hundreds of customizable rules are pre-made, so clients can rely on ZeroFox’s expertise or build solutions around specific policies and threats. Furthermore, ZeroFox’s platform is able to test the effectiveness of specific threat mitigations by analyzing its clients’ responses to identical threats. Overall, ZeroFox is one of the most riveting companies at Black Hat, and its specialization in protection and intelligence outside the firewall, including on social media, deep and dark web, is something to follow.
Judging Criteria
Sailing is similar to cybersecurity in that social, technical, and economic barriers often prevent beginners from joining. However, some companies and leaders strive to alleviate these barriers.
For example, Clark Mills and Major Clifford McKay created the Optimist Dinghy (Opti) to ease financial and age barriers to sailing (The Optimist Dinghy 1947-2007, 2013). The Opti design was so successful that it became one of the most popular sailboats globally and has introduced millions to sailing.
Similar to Mills and McKay’s progress in sailing, the companies recognized by the Opti Series have significantly improved their community and industry. The Opti Series highlights cybersecurity companies’ innovation and ability to address social, technical, and economic barriers. Furthermore, the definition of an optimist, “a person who is inclined to be hopeful and to expect good outcomes,” represents the outlook of cybersecurity if these trends continue (Merriam-Webster, 2021).
Here are the judging criteria:
- Highly differentiated and innovative by offering a unique product, technology, or technique.
- Demonstrates company growth, ideally supported by numerical data like funding and sponsorship, acquisitions, and hiring trends.
- Active external enthusiasm and press.
- Practices embodied by “Security Through Community,” such as inclusion initiatives and a supportive company culture.
- Socially conscious contributions that are easily proved or demonstrated (i.e., open-source code, publications, blogs, events, and licensing choices).
Bronze companies fit into one or two categories, while silver companies demonstrated three or four; gold companies exemplified all five. All companies, however, epitomized their awarded categories enough to deserve substantial recognition for their efforts.
I was very flexible with my interviews, and I did my best to create a holistic picture of each companies’ values and technologies. I also cited evidence whenever possible through public numerical data, blog posts, reports, publications, and product demos. Read the full criteria here.
About the Author
 Olivia Gallucci is a Cybersecurity Reporter for Cyber Defense Magazine and the winner of CDM’s 2021 Women in Cybersecurity scholarship. She is studying Computing Security and Computer Science at Rochester Institute of Technology.
Olivia Gallucci is a Cybersecurity Reporter for Cyber Defense Magazine and the winner of CDM’s 2021 Women in Cybersecurity scholarship. She is studying Computing Security and Computer Science at Rochester Institute of Technology.
She is a Free and Open Source Software advocate and Linux enthusiast. Olivia can be reached online here at CDM and at https://oliviagallucci.com/ and @ivyhac and https://www.linkedin.com/in/olivia-gallucci/

