- I replaced my iPad with this cheap Android 15 tablet, and it surprisingly held up
- Why this Bose portable speaker is my top recommendation for most people (and it's on sale)
- Are VPN-ready routers the best home Wi-Fi upgrade? My buying advice after testing one
- This Lenovo ThinkPad ditches its traditional design for one that would make my MacBook jealous
- This portable laptop accessory solved my biggest problem with working from home
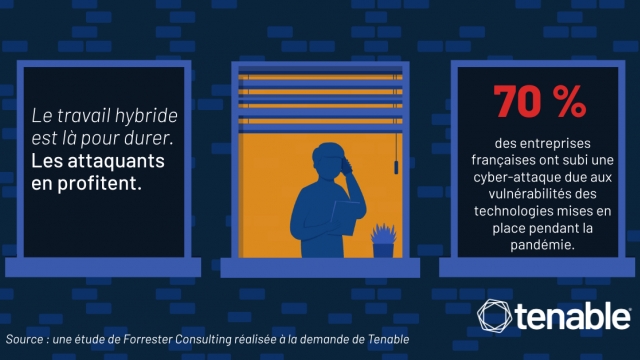
Seventy-One Percent of Indian Organizations Attribute Damaging Cyberattacks to Vulnerabilities in Technology Put in Place During Pandemic
Tenable®, Inc, the Cyber Exposure company, published a global study that revealed 71% of organizations in India attribute recent business-impacting cyberattacks to vulnerabilities in technology put in place in response to the pandemic. The data is drawn from ‘Beyond Boundaries: The Future of Cybersecurity in the New World of Work,’ a commissioned study of more than 1,300 security leaders, business executives and remote employees worldwide, including 92 responses in India, conducted by Forrester Consulting on…
Read More