- Key Cybersecurity Considerations for 2025
- Make the Most of Your Holiday Cybersecurity Awareness Efforts
- Stock your Kindle for summer: Get up to 93% off popular reads during Amazon's Book Sale
- I replaced my TV with a 4K UST projector - and the visual upgrade was worth it
- This Amazon Fire TV soundbar gave me room-filling audio without breaking the bank
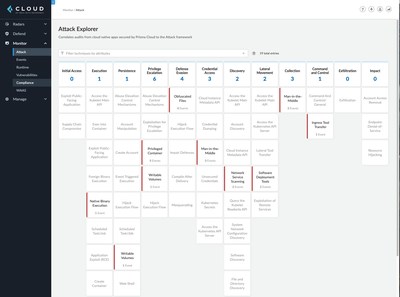
Prisma Cloud can now automatically protect cloud workloads and containers
Palo Alto Networks’ cloud-native security suite is getting a bundle of new features to automate VM security and add malware protection to CI/CD workflows, among others. Image: Palo Alto Networks Palo Alto Networks has announced a series of updates coming to its Prisma Cloud platform that the company said automatically protects cloud-hosted virtual machines and can “increase automation and detection, simplify compliance checks and deepen visibility into malware threats for containers and hosts.” Prisma Cloud…
Read More