VMware Product Release Tracker (vTracker)
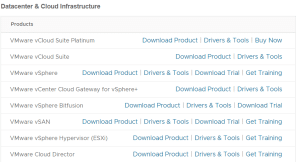
This page contains a list of products released by VMware. vTracker is automatically updated when new products are available to download (GA) at vmware.com. If you want to get notified about new VMware Products, subscribe to the RSS Feed. You can also use the JSON export to build your own tool. Feel free to comment when you have any feature requests. 2025-02-18VMware Tools 13.0.0 [Release Notes] 2025-02-13VMware Cloud Director Availability 4.7.3.1 [Release Notes] 2025-01-31VMware Cloud…
Read More