- The Quantum Sky Is Falling! Understanding the Quantum Threat to Network Security
- Microsoft Patches a Whopping Seven Zero-Days in March
- La BBC impulsa una división de IA, innovación y crecimiento para llegar a nuevos públicos
- Cybersecurity Can’t Wait: Modern Enterprises Must Adapt
- 칼럼 | 직원이 더 쉽게 일하는 시대··· 앱 사용성을 다시 생각할 이유
Changes to How Docker Handles Personal Authentication Tokens | Docker

A personal access token (PAT) is a replacement for a password that can have specific scopes for repository access. Docker is improving the visibility of Docker Desktop and Hub users’ personal access tokens. Specifically, we are changing how tokens are handled across sessions between the two tools. Read on to learn more about this security improvement.
What is changing with PATs and Docker?
To authenticate with Docker Hub, the Docker CLI uses PATs. To gain authenticated access to Hub from Docker CLI after a successful login from Docker Desktop, an API creates PATs on behalf of a Desktop user. These tokens were created after a user had successfully authenticated to Docker Hub through the login flow they have active for their organization (and thus had the required bearer tokens).
Within Docker Hub, if you navigate to your profile, select Edit > Security, you can see all of your access tokens, including ones created by Docker Desktop for the CLI on your behalf with Docker Hub (Figure 1).
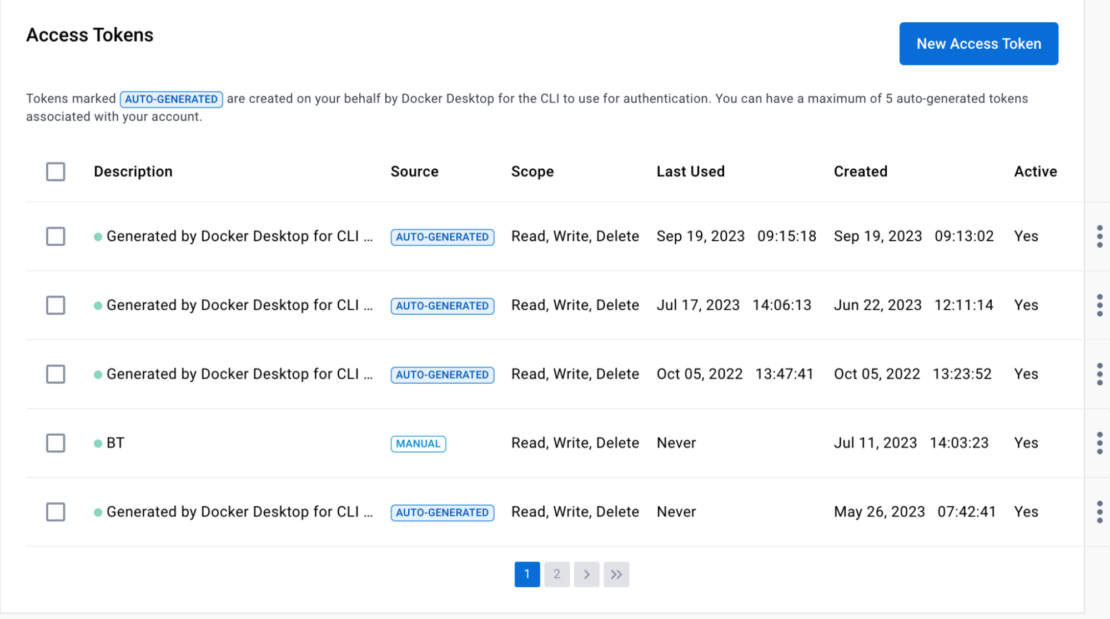
Docker has improved the visibility of these auto-generated tokens, and now all PATs are displayed inside a user’s profile for their active access tokens.
Users will be able to see if the tokens are auto-generated or if they were manually created. Users can also deactivate or delete these auto-generated session tokens just as they can with other PATs.
For security reasons, Docker encourages users to check their active tokens regularly. These auto-generated tokens will only maintain the five most recently used tokens. Any tokens outside those five auto-generated tokens will be deleted (Figure 2).
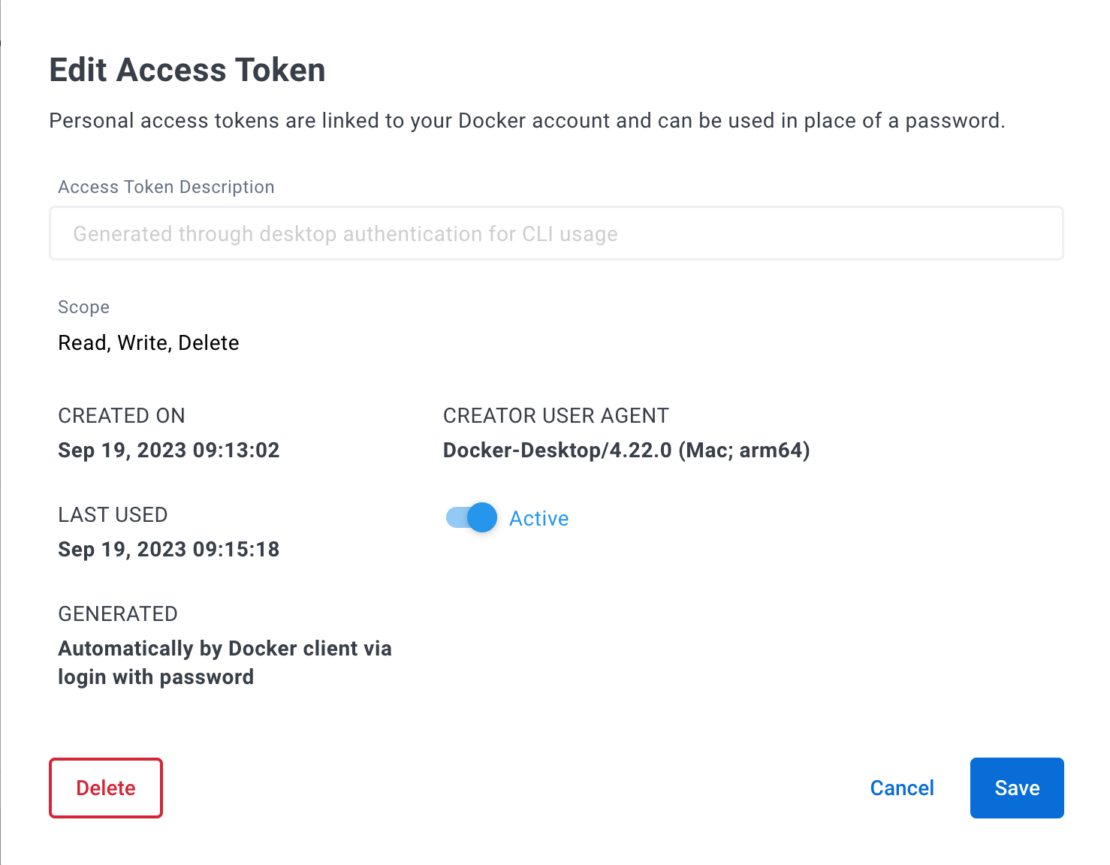
Note that using Docker Single Sign-On (SSO) functionality, requiring multi-factor authentication (MFA), and enforcing sign-in for Docker Desktop significantly reduces the risk of an account becoming compromised where any of a user’s personal access tokens could be exploited.
Appropriate monitoring around your software development lifecycle (SDLC) is essential, as all images should be scanned for malware and viruses as part of secure code analysis and on an ongoing basis.
Conclusion
Docker Hub, Docker Desktop, and the Docker CLI will continue to behave how users expect.
We encourage you to use the latest Docker Desktop and Docker CLI versions to get the newest features and security releases.
We also encourage you to use your new visibility into these PATs for Docker CLI and include all of your PATs in the regular security review for your organization and Docker accounts.
As always, we encourage security best practices for Docker users and will continue strengthening Docker’s tooling as we update and add new features.

