- The Significance of Cybersecurity within AI Governance
- How to disable ACR on your TV (and stop companies from spying on you)
- I expected this cheap multitool to be a waste of money, but it's my new a toolbox essential
- Have The Last Word Against Ransomware with Immutable Backup
- Multi-channel Secure Communication
Check Point: Hackers Are Dropping USB Drives at Watering Holes

In its 2023 Mid-Year Cyber Security Report, Check Point Software spotlighted numerous exploits so far this year, including novel uses of artificial intelligence and an old-school attack vector: USB drives. Cybercriminals and nation-state actors see these devices as the best way to infect air gapped, segmented and protected networks, according to Check Point.
The report’s authors noted the Raspberry Robin worm was one of the common malware variants distributed through USB drives via “autorun.inf” files or clickable LNK files. Check Point also reported that state-aligned threat actors are even launching 10-year-old infections such as ANDROMEDA via USB drives.
China-related espionage threat actor Camaro Dragon, for example, used USB drives as a vector to infect organizations all over the world, according to the report’s authors. In addition, the security researchers pointed out that Russian-aligned group Gamaredon used USB drive-delivered Shuckworm to target Ukrainian military and associated individuals.
I spoke with Pete Nicoletti, global chief information security officer for the Americas at Check Point Software, about some other top-line findings from the report. Nicoletti, who has more than 30 years in the field, said AI is a game changer, and that out of Check Point Software’s 70-plus engines, AI and machine learning drives 40 of them. The following transcript of my interview with Nicoletti has been edited for length and clarity.
Jump to:
Found an orphan USB? Better to leave it be
Karl Greenberg: I was surprised by the report’s details around physical USB drivers as a viable attack vector. Really? Today?

Pete Nicoletti: As a former penetration tester, I thought the days of USB drivers… USB devices being used to hack were going to go away, but we’ve seen a big uptick in companies falling for a USB drive insertion. When I used to try to break into companies, we used a watering hole attack: You go to the bar where the employees go, you go to the office building or bathroom where the employees go, and you drop a couple of USBs (it used to be CDs, with labels saying “3rd quarter layoffs” and people would grab them). We are seeing the same thing happening with flash drives, and this is dramatic.
Karl Greenberg: Hackers are physically leaving USB drives around?
Pete Nicoletti: Yes, and this tactic is infecting organizations. Before COVID, we used to have better policies against using USBs in corporate-owned laptops, because that laptop would be inspected. Post COVID, it’s BYO device, and there are fewer corporate protections, so that’s partly why we’re seeing a spike. Also, we’re seeing an uptick in hacktivism with politically motivated groups launching attacks and artificial intelligence misuse such as using AI to craft emails. We just saw the release of an AI-based keystroke monitoring tool that has about 85% to 95% accuracy in understanding the keystroke just by sound.
Bad bots: AI for spam, spearphishing and malware
Karl Greenberg: How important are AI tools today for cybersecurity practitioners, and what do you see as key ways hackers are using it?
Pete Nicoletti: If you don’t have artificial intelligence to battle artificial intelligence, you’re going to be a statistic, because AI is lowering the bar for the attackers. Just for spam, as an example, there are a lot more (non-English speaking) people now who can create emails using really good English.
Basically, hackers are using AI in at least two ways: They are using AI to write snippets of code rather than full-blown ransomware programs for, say, a zero day for a given common vulnerability and exposure; they are using it, for example, to write a keyboard stroke collector. And they are using AI to automate spam creation using hacked data to generate content. These could, for example, be tied to hacked private information about a patient’s information that may have been part of a large breach; hackers are using such data to create personalized emails: “You were just in for such and such a procedure, and you owe an additional $200 on the bill.”
SEE: Check Point announces raft of 2023 AI features (TechRepublic)
AI for the defense: Finding spam, insurance reviews, penetration tests
Karl Greenberg: How do you prevent or defend against these forms of AI-powered, spearphishing campaigns?
Pete Nicoletti: All of our big carrier customers use Avanan, an AI-powered (email security) tool we acquired two years ago. With it, we are able to discover new kinds of challenging-to-find spam — and spam is still 89% the vector of choice for successful attacks.
SEE: Check Point’s Avanan spotlights how business email compromise attacks emulate legitimate web services to lure clicks (TechRepublic)
Karl Greenberg: Besides use for reducing analyst workloads, where else are you seeing AI being used more today?
Pete Nicoletti: We’re seeing people use ChatGPT and other large language models to review their cyber insurance programs. We’re seeing people use it to write up penetration tests to give them more relevance and a deeper understanding of certain issues. If you’re not using artificial intelligence, you’re not going to be competitive.
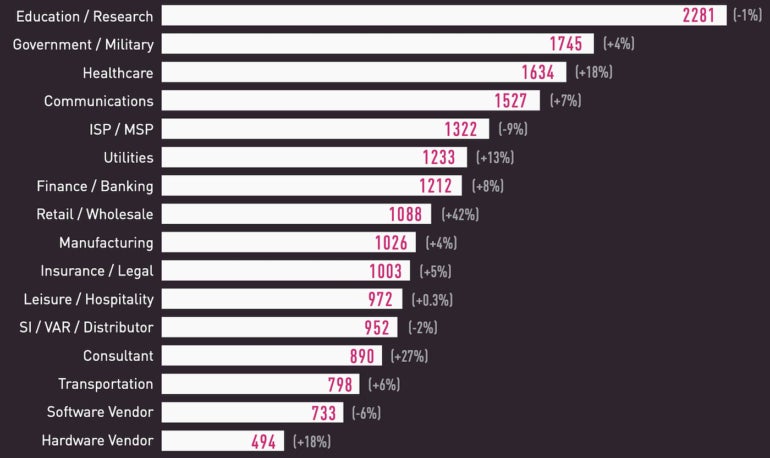
Education sector is the top target
Karl Greenberg: What are the other top-line findings from the first half of the year?
Pete Nicoletti: We’re seeing the education sector being the number one attack vertical; we’ve seen a huge spike in this.
Karl Greenberg: Why?
Pete Nicoletti: A couple of reasons, including schools transitioning to outsourced IT and using more online education tools. Also, educational institutions don’t have the budgets the commercial sector has. We have seen at least one university go out of business for the first time (Lincoln College in May 2022) because of ransomware demands. Globally, education and research are still the top targets for attacks (Figure A).
Figure A
Microsoft: A big house with many doors and “Windows”
Karl Greenberg: I noticed the number of vulnerabilities in commonly used corporate software is very high; Microsoft is number one. Why does Microsoft have so many CVEs?
Pete Nicoletti: Someone famously said they rob banks because that’s where the money is. If you’re a hacker, you want to target Microsoft because it’s so ubiquitous. It’s everywhere — an application developing company and an operating system. It’s used by everyone. So if you’re going to find a zero day, whether you’re a state-sponsored hacking group or just a 16-year-old in the basement wearing a hoodie, you’re going to be targeting Microsoft.
The other thing a lot of people don’t talk about: when you turn the knob as a company to push products out the door, because companies can take all the time in the world to develop something and test it, but companies want to release products now, not tomorrow. And when they turn the knob to be competitive and gain market share, this is the unspoken kind of risk of development that gets you in trouble.
Karl Greenberg: Which is why AI tools in DevOps are critical.
Pete Nicoletti: Companies with fast development shops are picking up these tools to increase security of their development pipeline, containers and Kubernetes, and it’s so much cheaper to fix in the development pipeline rather than in the test or production environment. So companies are finally figuring that out.
Sound and vision: The next AI threats
Karl Greenberg: What about other uses of AI for threats beyond text and code generation?
Pete Nicoletti: We have always been dealing with business email compromise; well, now it’s going to be voice compromise and video compromise. It’s absolutely coming. We’re going to start seeing a lot more photos converted to a video discussion. We’ve seen voice compromises already, and every bank that’s using voice confirmation and voice identification can be fooled now. So, if you have credit cards or banks that use this? Say goodbye. I wouldn’t enable that at all any more.

