- I tested a Pixel Tablet without any Google apps, and it's more private than even my iPad
- My search for the best MacBook docking station is over. This one can power it all
- This $500 Motorola proves you don't need to spend more on flagship phones
- Finally, budget wireless earbuds that I wouldn't mind putting my AirPods away for
- I replaced my Linux system with this $200 Windows mini PC - and it left me impressed
Chinese phishing actors consistently targeting EU diplomats

The China-aligned group tracked as TA416 (aka Mustang Panda) has been consistently targeting European diplomats since August 2020, with the most recent activity involving refreshed lures to coincide with the Russian invasion of Ukraine.
According to a new report by Proofpoint, TA416 spearheads cyber-espionage operations against the EU, consistently focusing on this long-term role without reaping opportunistic gains.
By keeping their tools and tactics essentially unchanged since 2020 and only refreshing their phishing themes and peripheral components, TA416 has made attribution simple for the analysts.
Timeline of activity
Starting in August 2020, the phishing actors impersonated EU-based organizations to target governments in the continent.

The malicious emails used a DropBox URL to deliver a variant of the PlugX malware, which was previously deployed in attacks against Australian organizations.
In November 2021, TA416 added hidden image trackers on emails to validate message openings and follow a more targeted approach in their campaign.
On January 17, 2022, Proofpoint noticed new delivery attempts involving ZIP files that were custom-named to match the target’s interests.
A change in tactic also occurred at this point, as the ZIP files weren’t fetched from a cloud hosting service but instead leveraged a dropper malware executable.
The four components downloaded this way were the PlugX malware, its loader, the DLL search order hijacker (process loader), and a PDF decoy file.
Finally, on February 28, 2022, the Chinese threat actors were spotted using a compromised diplomat’s address to target other top-ranking officials of NATO countries with lures involving the Russian invasion of Ukraine.
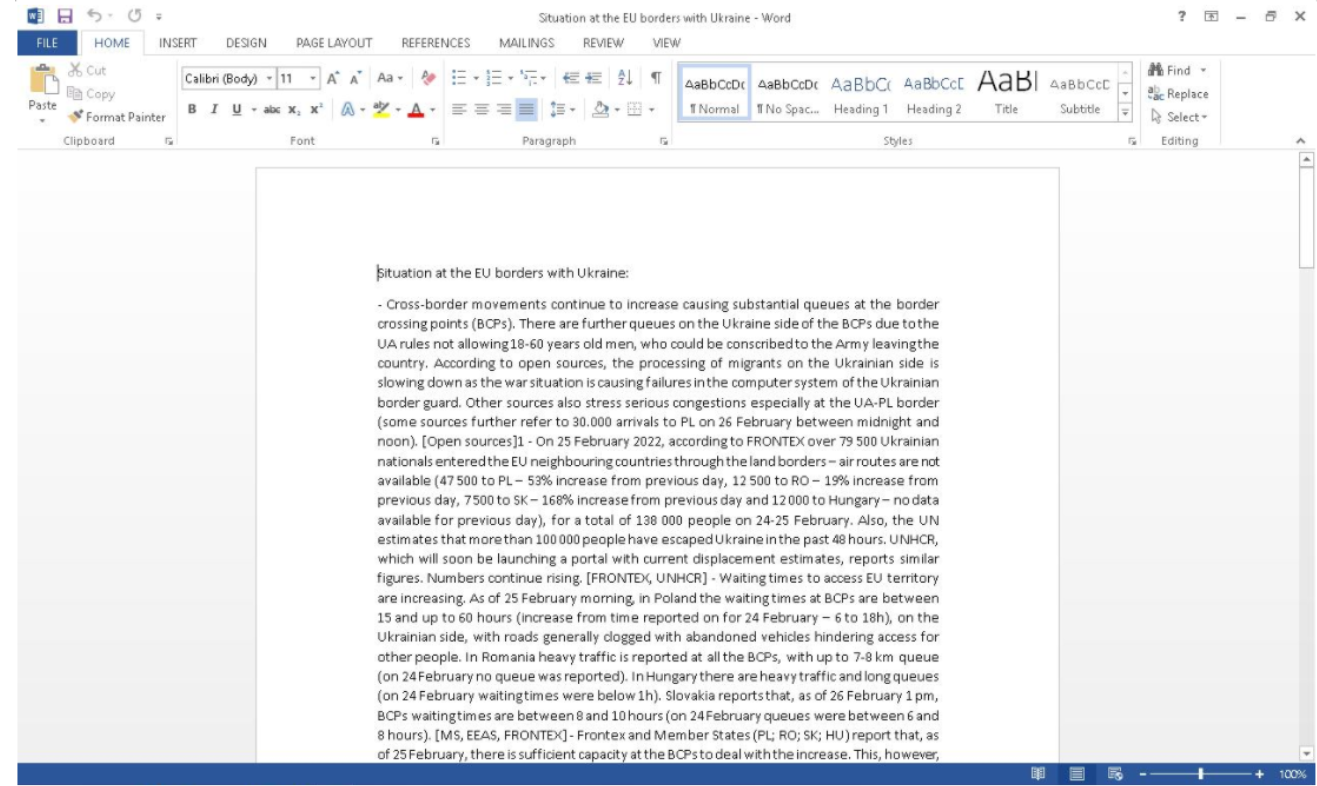
The compromised person worked in refugee and migrant services, an area that was recently targeted by Belarusian hackers as well.
Superficial changes
While the tactics, malware drop, installation, and loading methods remain constant across campaigns, Mustang Panda puts some effort into regularly changing the components used.
“The group uses different legitimate PE files to initiate side-loading, as well as a variety of PlugX DLL loaders including the PotPlayer and DocCon versions,” elaborates the Proofpoint report.
“TA416 also uses different variants of the final PlugX payload in which the communication routines are observed to be different when closely analyzed.”
However, too many elements form a common ground between 2020, 2021, and 2022 campaigns, as reflected in the following table.
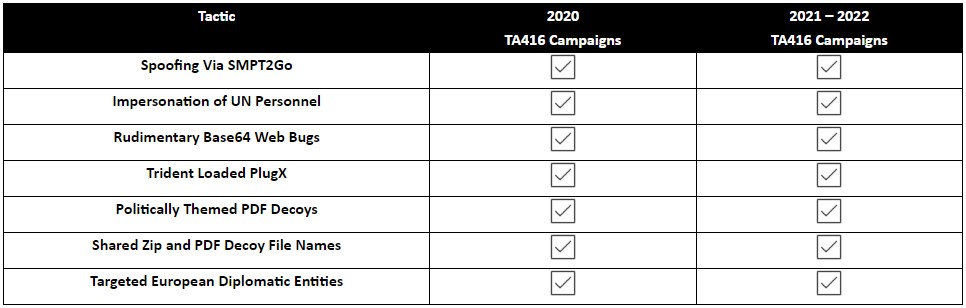
As Proofpoint’s report underlines in conclusion, these superficial variations will continue unabated, especially now that a fresh set of indicators of compromise has been published, so vigilance and good email security practices are advised to all potential targets.

