- My cat loves this automatic wet food feeder, and it's on sale
- Certified and Unstoppable: Recertify with Rev Up
- Walmart's drone delivery spreads its wings to 100 more stores - is yours one?
- Meta Ray-Bans for 20% off is a great deal on one of my favorite products
- Control content chaos without compromising security
Cisco Talos report: Threat actors use known Excel vulnerability

Microsoft Office files, particularly Excel and Word files, have been targeted by some cybercriminals for a long time. Through different techniques, attackers have used embedded Visual Basic for Applications macros to infect computers with different kinds of malware for cybercrime and cyberespionage.
In most cases, users still needed to click their agreement when executing code inside those applications, but some social engineering tricks have enticed unsuspecting victims to click and allow the execution of the malicious macros themselves. Direct exploitation of vulnerabilities without any user interaction is also possible to launch malware.
SEE: Mobile device security policy (TechRepublic Premium)
Jump to:
.XLL malicious exploitation in the wild
As exposed in new research from Cisco Talos, threat actors might leverage event handling functions in Excel files in order to automatically launch .XLL files. The most common method to achieve this is to execute the malicious code when the Excel Add-In manager calls the xlAutoOpen or xlAutoClose functions.
Cisco Talos researchers have leveraged specific queries in VirusTotal to find malicious .XLL files and provide YARA rules to hunt for such files. They separated native .XLL samples built with the usual Microsoft .XLL SDK and samples generated using the ExcelDNA framework, as it is free and tends to be the one most used by threat actors (Figure A).
Figure A

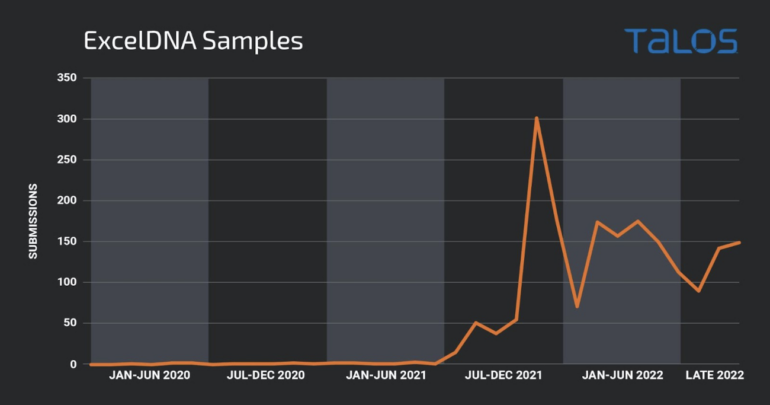
The charts above reveal that threat actors have been exploiting .XLL file vulnerabilities long before Microsoft started blocking documents containing VBA macros.
The Cisco Talos researchers established that no potentially malicious samples were submitted until July 2017. The first .XLL payload found on the VirusTotal platform launched calc.exe, which is a usual testing method for penetration testers and cybercriminals. The second sample, submitted in the same month, launched a Meterpreter reverse shell, which may be used for penetration testing or malicious intent.
After that activity, .XLL files appeared sporadically, but it did not increase until the end of 2021 when infamous malware families such as Dridex and FormBook began using it.
Which threat actors exploit .XLL files?
Several threat actors are now using .XLL files to infect computers.
APT10, also known as Red Apollo, menuPass, Stone Panda or Potassium, is a cyberespionage threat actor that has been operating since 2006 and is associated with the Chinese Ministry of State Security, according to the Department of Justice.
A file leveraging .XLL to inject a malware exclusive to APT10 dubbed Anel was found in December 2017 by the researchers.
TA410 is another threat actor who targets U.S. utilities and diplomatic organizations and is loosely linked to APT10. They employ a toolkit that also includes an .XLL stage discovered in 2020.
The DoNot team targeting Kashmiri nonprofit organizations and Pakistani government officials also seemed to use this method: An .XLL file containing two exports, the first one called pdteong and the second xlAutoOpen, make it a fully functional .XLL payload. The pdteong export name has been used exclusively by the DoNot team.
FIN7 is a cybercrime threat actor operating from Russia. In 2022, the threat actor started using .XLL files sent as attachment files in malicious email campaigns. When those files are executed, they act as downloaders for the next infection stage.
The major spike in the .XLL detections in VirusTotal, however, comes primarily from Dridex malware campaigns. These .XLL files are used as downloaders for the next infection stage, which is chosen from a large list of possible payloads accessible via the Discord software application.
The second most common payload is FormBook, an information stealer available as a service for a cheap price online. It uses email campaigns to spread the .XLL downloader, which fetches the next infection stage — the FormBook malware itself.
A recent AgentTesla and Lokibot campaign targeting Hungary exploited .XLL files via email. The email pretended to come from Hungarian police departments (Figure B).
Figure B
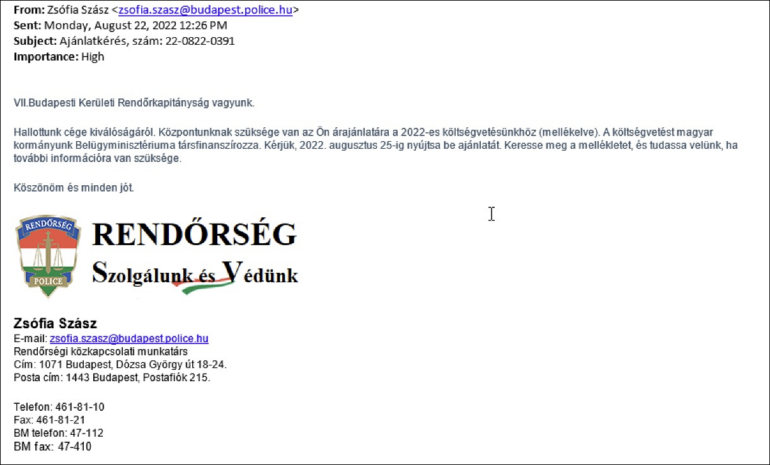
The text has been translated by Cisco Talos:
“We are the VII Budapest District Police Department.
We have heard about the excellence of your company. Our center needs your quote for our 2022 budget (attached). The budget is co-financed by the Ministry of the Interior of our Hungarian government. Please submit your offer by Aug. 25, 2022. Please find the attachment and let us know if you need more information.”
In addition, the Ducktail malware, an information stealer malware run by a Vietnam-operating threat actor, makes use of .XLL. The threat actor used a file named “Details of Project Marketing Plan and Facebook Google Ads Results Report.xll” to infect its targets with the Ducktail malware.
Default Microsoft Office behavior changes for the good
To help fight infections via the use of VBA macros, Microsoft decided to change the default behavior of its Office products to block macros in files downloaded from the internet.
Office Add-Ins are pieces of executable code that can be added to Office applications to improve functionalities or enhance the application’s appearance. Office Add-Ins might contain VBA code or modules embedding compiled functionalities in .NET bytecode. This could be in the form of COM servers or a Dynamic Link Library renamed with a specific file extension.
Add-Ins for the Microsoft Word application need to be in a location specified by a registry value, depending on the Office version. A file put in that folder with a file extension .WLL will be loaded into the Word process space.
For Microsoft Excel, any file with the .XLL extension that is clicked by the user will automatically attempt to run Excel as the opener for the .XLL file. In any case, the Excel software will trigger a display message about potential malware or security problems, but this is ineffective with general users, who tend to disregard such warnings.
.XLL add-ins are generally developed in the C/C++ programming language using the Microsoft Excel .XLL Software Development Kit, but some frameworks such as Add-In Express and Excel-DNA allow the use of .NET languages like C# or VB.NET.
How to protect against the .XLL security threat
The use of .XLL files is not widespread in corporate environments; businesses that do not need it should block any attempt to execute .XLL files in their environment. If your company does allow the use of .XLL files, careful monitoring must be run at endpoints and servers in order to detect any suspicious activity and investigate it.
Email gateways should not accept .XLL files by default, and raise awareness for corporate users. If they see a warning message from Excel about running Add-Ins and do not know why it happens, they should not allow the execution and call their IT/security department.
This security awareness and training policy and IT email security alert templates from TechRepublic Premium are great resources to help prevent a cybersecurity disaster from striking.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.

