Authored by Yashvi Shah and Vignesh Dhatchanamoorthy
McAfee Labs has discovered a highly unusual method of malware delivery, referred to by researchers as the “Clickfix” infection chain. The attack chain begins with users being lured to visit seemingly legitimate but compromised websites. Upon visiting, victims are redirected to domains hosting fake popup windows that instruct them to paste a script into a PowerShell terminal.
The “ClickFix” infection chain represents a sophisticated form of social engineering, leveraging the appearance of authenticity to manipulate users into executing malicious scripts. These compromised websites are often carefully crafted to look genuine, increasing the likelihood of user compliance. Once the script is pasted and executed in the PowerShell terminal, it allows the malware to infiltrate the victim’s system, potentially leading to data theft, system compromise, or further propagation of the malware.
We have observed malware families such as Lumma Stealer and DarkGate leveraging this technique. Here is the heatmap showing the distribution of users affected by the “Clickfix” technique:
Figure 1:Prevalence for the last three months
Darkgate ingesting via “ClickFix”
DarkGate is a sophisticated malware known for its ability to steal sensitive information, provide remote access, and establish persistent backdoors in compromised systems. It employs advanced evasion tactics and can spread within networks, making it a significant cybersecurity threat.
McAfee Labs obtained a phishing email from the spamtrap, having an HTML attachment.
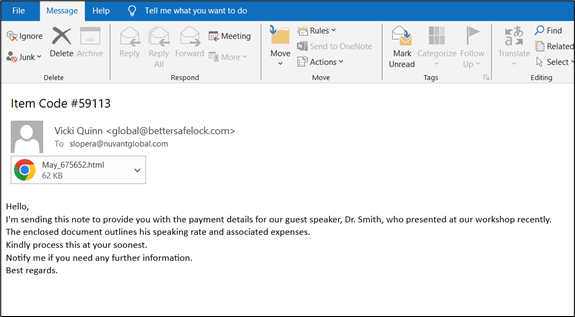
Figure 2: Email with Attachment
The HTML file masquerades as a Word document, displaying an error prompt to deceive users. This tactic is used to trick users into taking actions that could lead to the download and execution of malicious software.
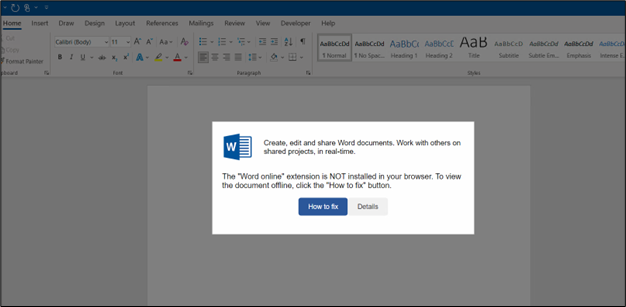
Figure 3: Displays extension problem issue
As shown, the sample displays a message stating, “The ‘Word Online’ extension is NOT installed in your browser. To view the document offline, click the ‘How to fix’ button.”
Before clicking on this button, let’s examine the underlying code. Upon examining the code, it was discovered that there were several base64-encoded content blocks present. Of particular significance was one found within the
tag, which played a crucial role in this scenario.<br />
<center><img loading="lazy" decoding="async" loading="lazy" class="aligncenter wp-image-196665 size-full" src="https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture4.png" alt="" width="782" height="191" srcset="https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture4.png 782w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture4-300x73.png 300w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture4-768x188.png 768w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture4-205x50.png 205w" sizes="auto, (max-width: 782px) 100vw, 782px"/></center></p>
<p style="text-align: center;">Figure 4: HTML contains Base64-encoded content in the title tag</p>
<p>Decoding this we get,</p>
<p><center><img loading="lazy" decoding="async" loading="lazy" class="aligncenter wp-image-196680 size-full" src="https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture5-1.png" alt="" width="599" height="380" srcset="https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture5-1.png 599w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture5-1-300x190.png 300w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture5-1-203x129.png 203w" sizes="auto, (max-width: 599px) 100vw, 599px"/></center></p>
<p style="text-align: center;">Figure 5: After decoding the code</p>
<p>The decoded command demands PowerShell to carry out malicious activities on a system. It starts by downloading an HTA (HTML Application) file from the URL <em>https://www.rockcreekdds.com/wp-content/1[.]hta</em> and saves it locally as <em>C:userspublicIx.hta</em>.</p>
<p>The script then executes this HTA file using the start-process command, which initiates harmful actions on the system. Additionally, the script includes a command (Set-Clipboard -Value ‘ ‘) to clear the contents of the clipboard. After completing its tasks, the script terminates the PowerShell session with exit.</p>
<p>Upon further inspection of the HTML page, we found a javascript at the end of the code.</p>
<p><center><img loading="lazy" decoding="async" loading="lazy" class="aligncenter wp-image-196695 size-full" src="https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture6-1.png" alt="" width="782" height="289" srcset="https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture6-1.png 782w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture6-1-300x111.png 300w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture6-1-768x284.png 768w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture6-1-205x76.png 205w" sizes="auto, (max-width: 782px) 100vw, 782px"/></center></p>
<p style="text-align: center;">Figure 6: Decoding function snippet</p>
<p>This JavaScript snippet decodes and displays a payload, manages modal interactions for user feedback, and provides functionality for copying content to the clipboard upon user action.</p>
<p>In a nutshell, clicking on the “How to fix” button triggers the execution of JavaScript code that copies the PowerShell script directly onto the clipboard. This script, as previously discussed, includes commands to download and execute an HTA file from a remote server.</p>
<p>Let’s delve into it practically:</p>
<p><center><img loading="lazy" decoding="async" loading="lazy" class="aligncenter wp-image-196710 size-full" src="https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture7-1.png" alt="" width="626" height="348" srcset="https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture7-1.png 626w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture7-1-300x167.png 300w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture7-1-205x114.png 205w" sizes="auto, (max-width: 626px) 100vw, 626px"/></center></p>
<p style="text-align: center;">Figure 7: Clipboard contains malicious command</p>
<p>The attackers’ additional instruction to press Windows+R (which opens the Run dialog) and then press CTRL+V (which pastes the contents from the clipboard) suggests a social engineering tactic to further convince the user to execute the PowerShell script. This sequence of actions is intended to initiate the downloaded script (likely stored in the clipboard) without the user fully understanding its potentially malicious nature.</p>
<p>Once the user does this, the HTA file gets downloaded.</p>
<p><center><img loading="lazy" decoding="async" loading="lazy" class="aligncenter wp-image-196725 size-full" src="https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture8.png" alt="" width="782" height="447" srcset="https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture8.png 782w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture8-300x171.png 300w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture8-768x439.png 768w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture8-205x117.png 205w" sizes="auto, (max-width: 782px) 100vw, 782px"/></center></p>
<p style="text-align: center;">Figure 8: HTA code snippet</p>
<p>The above file attempts to connect to the marked domain and execute a PowerShell file from this malicious source. Given below is the malicious script that is stored remotely and executed.</p>
<p><center><img loading="lazy" decoding="async" loading="lazy" class="aligncenter wp-image-196740 size-full" src="https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture9.png" alt="" width="782" height="125" srcset="https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture9.png 782w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture9-300x48.png 300w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture9-768x123.png 768w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture9-205x33.png 205w" sizes="auto, (max-width: 782px) 100vw, 782px"/></center></p>
<p style="text-align: center;">Figure 9: Powershell code snippet</p>
<p>As this PowerShell script is executed implicitly without any user interaction, a folder is created in the C drive where an AutoIt executable and script are dropped and executed automatically.</p>
<p><center><img loading="lazy" decoding="async" loading="lazy" class="aligncenter wp-image-196755 size-full" src="https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture10.png" alt="" width="626" height="139" srcset="https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture10.png 626w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture10-300x67.png 300w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture10-205x46.png 205w" sizes="auto, (max-width: 626px) 100vw, 626px"/></center></p>
<p style="text-align: center;">Figure 10: Downloaded zip contains AutoIT script</p>
<p>Following this, DarkGate begins its malicious activity and starts communicating with its command and control (C2) server.</p>
<p>A similar Clickfix social engineering technique was found to be dropping Lumma Stealer.</p>
<h2><strong>Lumma Stealer ingesting via “ClickFix”</strong></h2>
<p>McAfee Labs discovered a website displaying an error message indicating that the browser is encountering issues displaying the webpage. The site provides steps to fix the problem, which are designed to deceive users into executing malicious actions.</p>
<p><center><img loading="lazy" decoding="async" loading="lazy" class="aligncenter wp-image-196785 size-full" src="https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture11.png" alt="" width="626" height="361" srcset="https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture11.png 626w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture11-300x173.png 300w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture11-205x118.png 205w" sizes="auto, (max-width: 626px) 100vw, 626px"/></center></p>
<p style="text-align: center;">Figure 11: Showing error on accessing the webpage</p>
<p>It directs the target user to perform the following steps:</p>
<ol>
<li>Click on the “Copy Fix” button.</li>
<li>Right-click on the Windows icon.</li>
<li>Open Windows PowerShell (Admin).</li>
<li>Right-click within the open terminal window.</li>
<li>Wait for the update to complete.</li>
</ol>
<p>Let’s analyze the code that gets copied when clicking the “Copy Fix” button.</p>
<p><center><img loading="lazy" decoding="async" loading="lazy" class="aligncenter wp-image-196800 size-full" src="https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture12-1.png" alt="" width="626" height="252" srcset="https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture12-1.png 626w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture12-1-300x121.png 300w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture12-1-205x83.png 205w" sizes="auto, (max-width: 626px) 100vw, 626px"/></center></p>
<p style="text-align: center;">Figure 12: Base64-encoded content</p>
<p>As we can see, the code includes base64-encoded content. Decoding this content, we get the following script:</p>
<p><center><img loading="lazy" decoding="async" loading="lazy" class="aligncenter wp-image-196815 size-full" src="https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture13.png" alt="" width="626" height="289" srcset="https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture13.png 626w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture13-300x138.png 300w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture13-205x95.png 205w" sizes="auto, (max-width: 626px) 100vw, 626px"/></center></p>
<p style="text-align: center;">Figure 13: After decoding the Base64 content</p>
<p>This PowerShell script flushes the DNS cache and then decodes a base64-encoded command to fetch and execute a script from a remote URL <em>https://weoleycastletaxis.co.uk/chao/baby/cow[.]html</em>, masquerading the request with a specific User-Agent header. The fetched script is then executed, and the screen is cleared to hide the actions. Subsequently, it decodes another base64 string to execute a command that sets the clipboard content to a space character. The script is likely designed for malicious purposes, such as downloading and executing remote code covertly while attempting to hide its activity from the user.</p>
<p>Upon execution, the following process tree flashes:</p>
<p><center><img loading="lazy" decoding="async" loading="lazy" class="aligncenter wp-image-196830 size-full" src="https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture14.png" alt="" width="626" height="79" srcset="https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture14.png 626w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture14-300x38.png 300w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture14-205x26.png 205w" sizes="auto, (max-width: 626px) 100vw, 626px"/></center></p>
<p style="text-align: center;">Figure 14: Process Tree</p>
<p>As we know it is downloading the malware from the given URL, a new folder is created in a Temp folder and a zip is downloaded:</p>
<p><center><img loading="lazy" decoding="async" loading="lazy" class="aligncenter wp-image-196845 size-full" src="https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture15.png" alt="" width="626" height="217" srcset="https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture15.png 626w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture15-300x104.png 300w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture15-205x71.png 205w" sizes="auto, (max-width: 626px) 100vw, 626px"/></center></p>
<p style="text-align: center;">Figure 15: Network activity</p>
<p>The malware is unzipped and dropped in the same folder:</p>
<p><center><img loading="lazy" decoding="async" loading="lazy" class="aligncenter wp-image-196860 size-full" src="https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture16.png" alt="" width="626" height="135" srcset="https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture16.png 626w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture16-300x65.png 300w, https://www.mcafee.com/blogs/wp-content/uploads/2024/07/Picture16-205x44.png 205w" sizes="auto, (max-width: 626px) 100vw, 626px"/></center></p>
<p style="text-align: center;">Figure 16: Dropped files</p>
<p>The malware starts communicating with its C2 server as soon as it gets dropped in the targeted system.</p>
<h2>Conclusion:</h2>
<p>In conclusion, the Clickfix social engineering technique showcases a highly effective and technical method for malware deployment. By embedding base64-encoded scripts within seemingly legitimate error prompts, attackers deceive users into performing a series of actions that result in the execution of malicious PowerShell commands. These commands typically download and execute payloads, such as HTA files, from remote servers, subsequently deploying malware like DarkGate and Lumma Stealer.</p>
<p>Once the malware is active on the system, it begins its malicious activities, including stealing users’ personal data and sending it to its command and control (C2) server. The script execution often includes steps to evade detection and maintain persistence, such as clearing clipboard contents and running processes in minimized windows. By disguising error messages and providing seemingly helpful instructions, attackers manipulate users into unknowingly executing harmful scripts that download and run various kinds of malware.</p>
<h2>Mitigations:</h2>
<p>At McAfee Labs, we are committed to helping organizations protect themselves against sophisticated cyber threats, such as the Clickfix social engineering technique. Here are our recommended mitigations and remediations:</p>
<ol>
<li>Conduct regular training sessions to educate users about social engineering tactics and phishing schemes.</li>
<li>Install and maintain updated antivirus and anti-malware software on all endpoints.</li>
<li>Implement robust email filtering to block phishing emails and malicious attachments.</li>
<li>Use web filtering solutions to prevent access to known malicious websites.</li>
<li>Deploy firewalls and intrusion detection/prevention systems (IDS/IPS) to monitor and block malicious network traffic.</li>
<li>Use network segmentation to limit the spread of malware within the organization.</li>
<li>Enforce the principle of least privilege (PoLP) to minimize user access to only necessary resources.</li>
<li>Implement security policies to monitor and restrict clipboard usage, especially in sensitive environments.</li>
<li>Implement multi-factor authentication (MFA) for accessing sensitive systems and data.</li>
<li>Ensure all operating systems, software, and applications are kept up to date with the latest security patches.</li>
<li>Continuously monitor and analyze system and network logs for signs of compromise.</li>
<li>Encrypt sensitive data both in transit and at rest to protect it from unauthorized access.</li>
<li>Regularly back up important data and store backups securely to ensure data recovery in case of a ransomware attack or data breach.</li>
</ol>
<h2>Indicators of Compromise (IoCs)</h2>
<table>
<tbody>
<tr>
<td width="101"><strong>File</strong></td>
<td width="523"><strong>SHA256</strong></td>
</tr>
<tr>
<td colspan="2" width="624"><strong>DarkGate</strong></td>
</tr>
<tr>
<td width="101"><strong>Email</strong></td>
<td width="523">c5545d28faee14ed94d650bda28124743e2d7dacdefc8bf4ec5fc76f61756df3</td>
</tr>
<tr>
<td width="101"><strong>Html</strong></td>
<td width="523">0db16db812cb9a43d5946911501ee8c0f1e3249fb6a5e45ae11cef0dddbe4889</td>
</tr>
<tr>
<td width="101"><strong>HTA</strong></td>
<td width="523">5c204217d48f2565990dfdf2269c26113bd14c204484d8f466fb873312da80cf</td>
</tr>
<tr>
<td width="101"><strong>PS</strong></td>
<td width="523">e9ad648589aa3e15ce61c6a3be4fc98429581be738792ed17a713b4980c9a4a2</td>
</tr>
<tr>
<td width="101"><strong>ZIP</strong></td>
<td width="523">8c382d51459b91b7f74b23fbad7dd2e8c818961561603c8f6614edc9bb1637d1</td>
</tr>
<tr>
<td width="101"><strong>AutoIT script</strong></td>
<td width="523">7d8a4aa184eb350f4be8706afb0d7527fca40c4667ab0491217b9e1e9d0f9c81</td>
</tr>
<tr>
<td colspan="2" width="624"><strong>Lumma Stealer</strong></td>
</tr>
<tr>
<td width="101"><strong>URL</strong></td>
<td width="523">tuchinehd[.]com</td>
</tr>
<tr>
<td width="101"><strong>PS</strong></td>
<td width="523">07594ba29d456e140a171cba12d8d9a2db8405755b81da063a425b1a8b50d073</td>
</tr>
<tr>
<td width="101"><strong>ZIP</strong></td>
<td width="523">6608aeae3695b739311a47c63358d0f9dbe5710bd0073042629f8d9c1df905a8</td>
</tr>
<tr>
<td width="101"><strong>EXE</strong></td>
<td width="523">e60d911f2ef120ed782449f1136c23ddf0c1c81f7479c5ce31ed6dcea6f6adf9</td>
</tr>
</tbody>
</table>
<p> </p>
<div class="card ad_text">
<div class="ad-content">
<img decoding="async" src="https://www.mcafee.com/blogs/wp-content/uploads/2024/06/mcafeeredlogo-1.png"/></p>
<div class="card-body">
<h6 class="card-title">
Introducing McAfee+ </h6>
<p>Identity theft protection and privacy for your digital life</p>
<p> <a href="https://www.mcafee.com/en-us/identity-theft/protection.html?path=blogs" target="_blank" rel="noopener"><button type="button" class="btn btn-danger border-radius">Download McAfee+ Now</button></a></p></div>
</p></div>
</p></div>
<p>




