- Why I recommend this OnePlus phone over the S25 Ultra - especially at this new low price
- I replaced my laptop with Microsoft's 12-inch Surface Pro for weeks - here's my buying advice now
- This palm recognition smart lock doubles as a video doorbell (and has no monthly fees)
- Samsung is giving these Galaxy phones a big One UI upgrade - here's which models qualify
- 7 MagSafe accessories that I recommend every iPhone user should have
Connectivity and Cloud: A Chance for Zero Trust

By Sergej Epp, Chief Security Officer, EMEA
While Zero Trust is a term that is often misunderstood as well as misused, it is an approach that has real value in helping to reduce systematic cyber risk and improve resiliency. Organizations of all sizes understand that they require a resilient cybersecurity strategy that can support and enable the business even during a crisis, but when it comes to Zero Trust, most organizations struggle to understand it and figure out the right place to start. Moving to the cloud provides a new chance for Zero Trust architectures.
So what is and isn’t Zero Trust?
Some vendors will claim that Zero Trust is all about identity and access management. That is, how the business enables authorized users to access resources. While that’s a building block of Zero Trust, it’s only one component of what should be thought of as a larger strategy that takes into account all the risk surfaces the business operates in across identity, infrastructure, product, processes, and supply chain.
Every security professional will tell you that trust in technology architectures and networks has historically always been a bad idea. A trusted network connected to your data center network might be compromised, an endpoint hacked, a trusted user with the key to your kingdom turned to an insider, a trusted operating system process hijacked by a trojan, a trusted file being malicious, etc.
Consequently, Zero Trust provides a strategic approach to eliminate all implicit trust between technological entities. In simple words: it mandates to deploy not just bouncers at the entrance to your club but also within the club and in the garage and hire some bodyguards who are escorting your customers outside the club. Wait, is Zero Trust that simple? Is that just a call for more security? Let’s be honest, the key question for organizations has always been not if they should embrace Zero Trust, but why would it work this time, and where should they start considering the high cost and little willingness of change?
Zero Trust for black swans
From my experience, organizations that embraced Zero Trust successfully have focused their programs on risk management first. Working over a decade for a large financial services organization, I got to know risk management very well. Especially the fact that sometimes small events can cause damage to an entire organization or even industry. Such systematic events, aka black swans, became recently very common within our cybersecurity metaverse as well.
Ransomware and supply chain incidents are potentially the most visible symptoms of those risks we see in the news every day. Those risks are a good focus for your Zero Trust program. Looking at the root cause of such technological systematic risk, they come in a few different varieties or, in the worst case, a combination of all:
- Single point of failures. These include core infrastructure components that glue your technology stack together. An insecure or improperly architected Active Directory, WebSSO or DNS infrastructure can quickly turn into a nightmare.
- Outdated software monocultures. Operating systems, firmware, and software with high organizational adoption rates that are not being patched on a regular basis. A single vulnerability can result in catastrophic ransomware or sabotage risk.
- Flat networks effect. An organization without proper segmentation or network controls across IT (think of all your unmanaged devices), OT, and IoT. Easy game for every intruder or virus/ransomware.
Palo Alto Networks
Zero Trust pyramid
Traditional companies that inherit a combination of those systematic risks are typically kicking off their Zero Trust program based on two building blocks: harmonizing their identity and access management stack and harmonizing their connectivity landscape. This creates a foundation for additional Zero Trust building blocks addressing other systematic risks, such as firmware monocultures, applications, etc.
The role of a platform in Zero Trust
If I had to explain cybersecurity resilience, I’d go with the following: to create a resilient organization requires us to make security a system and not a component goal. For example, don’t put all your focus on testing the effectiveness of your sandbox control. Instead, prioritize how your sandbox is integrated with other security controls across your organizations. Or don’t spend millions on pentesting your most critical application if this application is connected in the same network to a million-dollar IoT device and runs some additional exposed services on the server.
In a decentralized and fragmented world, where workloads and identities live somewhere on the internet, such a systematic cybersecurity perspective becomes very difficult without harmonizing some core capabilities required to operate your security:
- A common identity and policy stack.
- A common understanding of actionable threats.
- A common protocol/control for enforcing your policy and threat information across your entire system.
A different way to explain this is to take Phil Venables’s approach in one of his recent blogs. He wrote, “One of the most successful techniques for enterprise security in many organizations is to create a universal baseline of controls that apply everywhere—and to then economically increase that baseline by reducing the unit cost of controls (existing and new).” In his blog, he refers to the automotive industry as an example, suggesting that commoditization of safety features from racing cars towards everybody’s family car can be replicated to cybersecurity. In fact, network security and connectivity is a great example.
The way network security worked in the past was that everything that was inside the organization was trusted, and everything outside was untrusted—security was applied only at the boundaries of the organization. That model doesn’t work anymore with remote workers, cloud, edge, and mobile access requirements. All those environments are connected directly to the internet today. However, they all lack even the most basic controls such as segmentation or intrusion detection.
The reason is that testing or deploying individual controls and policies leads to high costs, making most cybersecurity controls unaffordable for organizations. That’s why cybersecurity platforms are becoming the best strategy to deploy Zero Trust strategies and an economical differentiation factor for most cybersecurity programs over time.
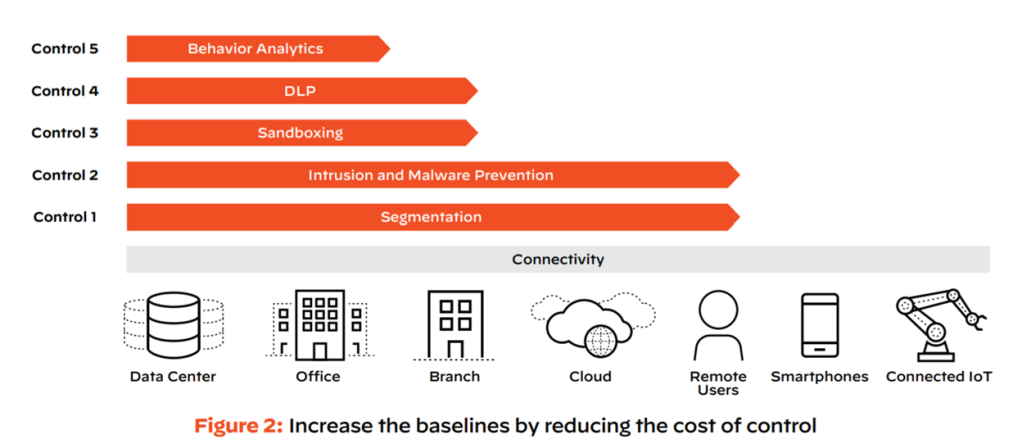
Palo Alto Networks
The cloud opportunity for Zero Trust
Replacing legacy connectivity or security stack is a big deal and requires—if not triggered by your cloud and remote workforce programs—sometimes a harsh (ransomware) push to make it happen, but there is a new chance for your Zero Trust program, which shouldn’t be overlooked and wasted! As organizations are increasingly moving workloads, applications, and users to the cloud, and adopting DevOps, now is the right time to architect your security right from the beginning and not post-mortem.
A systematic approach in this context requires you to consider, besides the security of your production environment, the security of your CI/CD pipeline and integration of security controls as early as possible in the pipeline. Let’s formulate a few questions in Zero Trust language, which should be in your Book of Work if you take security in the DevOps and cloud environments seriously:
- Do you trust your software engineer’s device not being compromised?
- Do you trust your code repository is not being compromised?
- Do you trust the code integrity along the development and deployment process?
- Do you trust your third-party infrastructure as code (IaC) template or docker container? Remember, on average, half of them have bad vulnerabilities associated with them.
- What about other software application dependencies used in your projects?
- Do you trust your identities being assigned to the right privilege rights?
- Do you trust your code being checked for security or misconfigurations such as hardcoded credentials, over privileged network settings, etc.?
- Do you trust your microservices orchestrator not being compromised, etc.?
There are many other questions to be addressed, but the point is that systematic risks increase in the DevOps environments in both vertical and horizontal directions. Vertically, there are many more risks to be considered compared to more traditional environments. Horizontally, an impact of a single poisoned package can be massive, as seen with many cases such as SolarWinds, etc. Don’t waste your opportunity to build Zero Trust at the beginning of your DevOps and cloud journey.
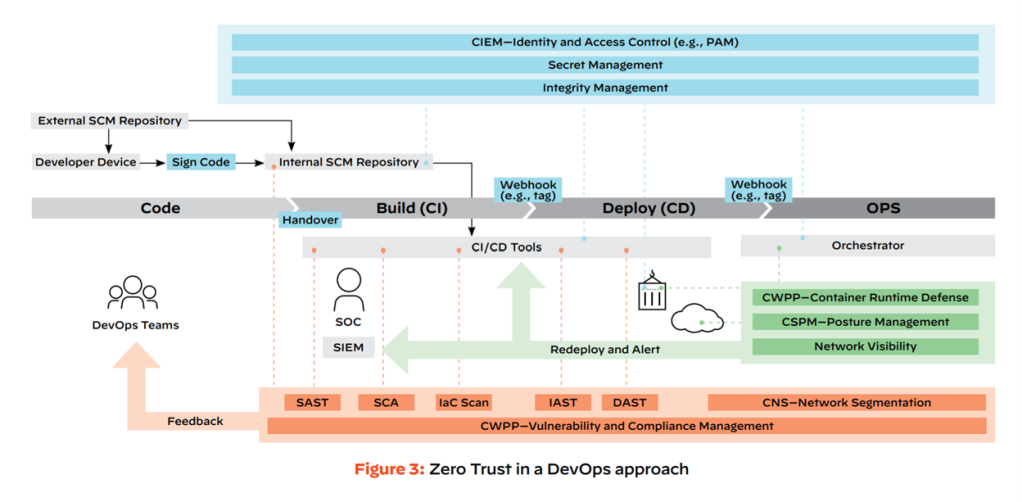
Palo Alto Networks
To learn more, visit us here.
About Sergej Epp

Sergej Epp, CSO Palo Alto Networks, Central Europe
Palo Alto
Sergej Epp is Chief Security Officer (CSO) at Palo Alto Networks in Central Europe. In this role, he develops regional cybersecurity strategy and is overseeing cybersecurity operations and threat intelligence across the region. His functional specialities include cyber defense operations, cyber risk management and transformation management. Prior to joining Palo Alto Networks, he spent eight years in a variety of roles at Deutsche Bank, with his last position leading groups focusing on Cyber Hygiene Operations and Cyber Forensics & Investigations. He also founded and led the first Group-wide Cyber Defense Center including Threat Intelligence, Active Defense, Red Teaming as well as Security Awareness and Security Big Data programs. Sergej regularly participates in forums, conferences and panels and provides advise on threat intelligence and cyber defense matters. Outside of the office, Sergej is a passionate advocate for cybersecurity and emerging technologies. He has particular interest in Cybercrime research, Blockchain and Financial Markets and also spends time in teaching those to graduates or professionals.

