- ‘데이터브릭스 데이터+AI 서밋 2025’ 데이터 전문가를 위한 5가지 핵심 사항
- AI 아바타 시장 2032년까지 33.1% 성장 전망···마켓앤마켓, 개인화된 고객 경험 증가가 성장 견인
- Kali Linux gets a UI refresh, new tools, and an updated car hacking toolset
- How the Sandwich Generation Can Fight Back Against Scams | McAfee Blog
- Buy a Samsung Galaxy Watch 7 on sale and get a free SmartTag2 Bluetooth tracker - here's how
CVE-2020-1472: Microsoft Finalizes Patch for Zerologon to Enable Enforcement Mode by Default

Zerologon has quickly become valuable to nation-state threat actors and ransomware gangs, making it imperative for organizations to apply these patches immediately if they have not yet done so.
Background
On February 9, as part of its February 2021 Patch Tuesday release, Microsoft released an additional patch for Zerologon to enable a security setting by default to protect vulnerable systems.
CVE-2020-1472, also known as “Zerologon,” is a critical elevation of privilege vulnerability in Microsoft’s Netlogon Remote Protocol. It was initially patched in Microsoft’s August 2020 Patch Tuesday. The vulnerability received a CVSSv3 score of 10.0, the maximum possible score, and a Vulnerability Priority Rating (VPR) score of 10, underscoring its severity.
Additional details shared by researchers including fully working proof-of-concept
On September 11, 2020, researchers at Secura, who were credited with discovering the vulnerability, published a blog post and whitepaper providing more details about the severe flaw. Three days later, security researcher Dirk-jan Mollema published a proof-of-concept (POC) exploit script to GitHub.
Since there are already public POCs out there now, here is mine: https://t.co/ykiCYNiSHM
Requires latest impacket version from GitHub!
— Dirk-jan (@_dirkjan) September 14, 2020
The severity wasn’t lost on the U.S. government, which issued Emergency Directive 20-04 on September 18, 2020, instructing federal agencies to apply the patch for Zerologon within a matter of a few days. The directive was prescient, as researchers at Microsoft tweeted on September 23, 2020 that they had observed Zerologon being “incorporated into attacker playbooks.”
Microsoft is actively tracking threat actor activity using exploits for the CVE-2020-1472 Netlogon EoP vulnerability, dubbed Zerologon. We have observed attacks where public exploits have been incorporated into attacker playbooks.
— Microsoft Security Intelligence (@MsftSecIntel) September 24, 2020
On October 9, the Cybersecurity and Infrastructure Security Agency (CISA) published a joint advisory (AA20-283A) with the Federal Bureau of Investigation (FBI) related to Zerologon. CISA and the FBI observed that advanced persistent threat (APT) actors were exploiting Zerologon as part of a vulnerability chain with other unpatched vulnerabilities to target federal and state, local, tribal, and territorial (SLTT) governments.
Nine days later, a blog post from The DFIR Report detailed how Ryuk, one of the most nefarious ransomware gangs in operation, incorporated Zerologon into its playbook, leveraging it to perform a takeover of a domain controller (DC).
Factoring in all of these developments and recognizing the sheer severity of the flaw, the Tenable Security Response Team crowned Zerologon the number one vulnerability in our 2020 Threat Landscape Retrospective.
Analysis
As part of its initial patch for Zerologon, Microsoft indicated the vulnerability would be addressed “in a phased two-part rollout.” The first phase addressed the underlying vulnerability on two fronts. Firstly, patched DCs will block both Windows-based domain members and non-Windows DCs that are configured to explicitly disable signing/encryption. Secondly, the patch also changes the Netlogon protocol for clients unable to use the required signing/encryption. This change mathematically strengthens the defense against Zerologon, making it exponentially more difficult to exploit.
The second phase of Microsoft’s two-part patch rollout relates to a settings change to handle insecure connections from third-party / non-Windows devices that don’t or can’t use the required signing/encryption. The restrictions enforced on Windows-based devices with the August 2020 patch will be enforced on non-Windows devices with the February 2021 patch.
Microsoft originally outlined a series of action items to address Zerologon, which includes:
- Update: Apply the patch for CVE-2020-1472 for DCs and read-only DCs.
- Find: Check event logs to identify which of your devices are maintaining vulnerable connections to your systems (Microsoft has provided a script for this).
- Address: Review logs to identify systems still using a vulnerable secure channel for Netlogon.
- Enable: Modify the Netlogon Parameters registry key and enable Enforcement mode by setting the FullSecureChannelProtection data value to 1.
The fourth step, enabling Enforcement Mode, was previously something users had to manually enable. However, with the update included in the February 2021 Patch Tuesday release, Microsoft has enabled this setting on Windows DCs by default, irrespective of whether or not users and organizations enabled it prior to this release.
The purpose of this setting is to ensure that DCs will not accept vulnerable Netlogon secure channel connections. This setting can be overridden by adding an account to the Create Vulnerable Connections list. However, please note that usage of this allowlist should only serve as a stopgap measure and not a permanent fix.
Proof of concept
At the time this blog post was published, there were 51 repositories on GitHub hosting PoC code, including exploit scripts for Zerologon.
Solution
As promised, Microsoft completed its two-phase rollout to address Zerologon in the February 2021 Patch Tuesday release. For organizations that have not applied any Patch Tuesday updates since the August 2020 release, applying this month’s release will address both phases.
Considering how quickly Zerologon has become valuable to nation-state threat actors and ransomware gangs, it is imperative that organizations apply these patches immediately if they have not yet done so.
Identifying affected systems
A list of Tenable plugins to identify this vulnerability can be found here. Tenable released a remote check plugin for Zerologon that can be used against DCs to test whether or not they’re exploitable. Please note that this plugin requires disabling the “Only use credentials provided by the user” option under Assessment Settings.
To make things easier for our customers that wish to scan using the remote check plugin, we released a scan template policy for Tenable.io, Tenable.sc and Nessus that configures the necessary settings for the scan to run successfully.
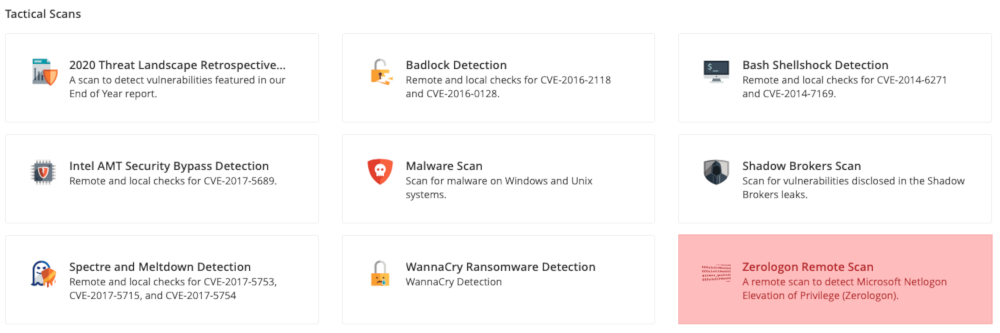
A list of tactical scans available to customers under the scan template settings
Please be advised that the safest way to test whether or not your DC is vulnerable is to leverage the scan template policy or plugin as part of a single target scan, as the configuration change to the “Only use credentials provided by the user” setting will apply to all plugins, which could overwhelm other targeted assets on your network.
Get more information
Join Tenable’s Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.


