- 팔로알토 네트웍스, 프로텍트 AI 인수··· ‘AI 보안 강화'
- 정철환 칼럼 | 뜬금없는 지브리 열풍
- I'd pick this midrange OnePlus phone over most budget options - especially at $70 off
- The OnePlus 12 still competes with today's flagship phones - and it's on sale for $150 off
- You can run Arch Linux in Windows now - here's how
Cyber-Attacks on Ukraine Surge 123%, But Success Rates Plummet

Russian cyber-attacks against Ukraine skyrocketed in the first half of 2023, with 762 incidents observed by Ukraine’s State Service of Special Communications and Information Protection (SSSCIP).
This represents a 123% surge compared with the second half of 2022.
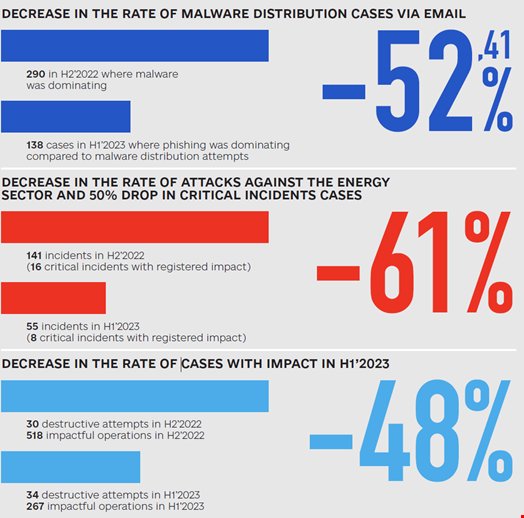
However, the SSSCIP also found that these attacks were significantly less successful than in the past, with critical incidents dropping by 81% and the number of what the agency tracks as “incidents with impact” falling by 48% in H1 2023 compared with H2 2022.
How Russian Cyber Tactics Are Changing
These changes can be attributed to a shift in tactics used by the attackers from sophisticated tactics and tools like wiper malware to employing a simpler ‘spray and pray’ approach with a growing use of ‘living off the land’ techniques.
For instance, malware distribution has decreased by 52.41%, largely replaced by less sophisticated phishing attacks and leveraging open source email systems with known vulnerabilities.
How Russia’s Cyber Strategy Had to Adapt Ukraine’s Defenses
Ukraine’s defense of its infrastructure has markedly improved compared to six months ago, the SSSCIP added in the report.
A good example is the effort the CERT-UA and its partners deployed to improve their incident detection & response and threat intelligence capabilities. This forced Russian threat actors to act faster once they infiltrated a network.
“It prompted them to place even greater emphasis on a particular tactic: dumping documents, sometimes as many as 21,000 office documents in certain cases, along with browser credentials. They execute this tactic within the first 30 minutes of successfully infiltrating a compromised system,” reads the report.
Read more: Mandiant Unveils Russian GRU’s Cyber Playbook Against Ukraine
Law Enforcement and Media Top Targets of Russian Cyber Aggression
During the observed period, Russia-backed threat actors have also shifted their targeting away from the energy sector – attacks against Ukrainian energy organizations have dropped by 61% – to focus heavily on law enforcement agencies and the media industry.
“During this period, we encountered espionage operations conducted by military [advanced persistent threat groups] (APTs) aimed at gaining access to and extracting data from various law enforcement units in Ukraine. Their primary objectives were to identify which evidence of Russian war crimes and exercise control over potential ground-deployed spies have our law enforcement teams,” wrote the SSSCIP.
Some of these espionage campaigns also targeted Ukraine’s private sector to gain information about the outcomes of Russia’s kinetic operations, including missile and drone attacks, in the case of potential targets of the Russian army.
Finally, the SSSCIP noticed that state-sponsored hackers tended to revisit previous victims who handle and maintain the critical data needed by the Russian military during the observed period.
“This approach grants attackers the ability to strategize future actions and anticipate our responses,” the SSSCIP wrote.

