- I ditched my daily driver Bose headphones for the XM6 - and I'm hesitant to go back
- This Lenovo ThinkPad is my top pick for remote work - and it's nearly 50% off now
- I invested in this 3-in-1 robot vacuum, and it's paying off for my home
- I've tested the Meta Ray-Bans for months, and these 5 features still amaze me
- My new favorite iPhone portable charger has a magnetic superpower - and it's cheap
Daily Malicious Files Soar 3% in 2023, Kaspersky Finds

Cybercriminals unleashed an average of 411,000 malicious files every day in 2023, representing a 3% increase from the previous year, according to Kaspersky.
The firm’s Security Bulletin: Statistics of the Year Report, published on December 14, 2023, showed that particular types of threats also escalated.
One example is the use of malicious desktop files (Microsoft Office, PDF…) to spread malware. Out of the 125 million files detected by Kaspersky in 2023, 24,000 were such documents – representing a 53% increase from 2022.
“The growth may be linked to a rise in attacks utilizing phishing PDF files, designed to pilfer data from potential victims,” the report reads.
Uptick in Backdoor Use
Microsoft Windows remained the primary target for cyber-attacks, accounting for 88% of all malware-filled data detected daily. However, the firm observed a few interesting samples of macOS malware, especially in France, China and Italy.
Many of the malicious files targeting macOS systems were disguised as adware.
The most widespread type of malware continues to be Trojans, with a notable uptick in the use of backdoors, registering a growth from 15,000 detected files per day in 2022 to 40,000 in 2023.
“Backdoors stand out as one of the most hazardous types of Trojans, providing attackers with remote control over a victim’s system to carry out tasks such as sending, receiving, executing, and deleting files, as well as harvesting confidential data and logging computer activity,” Kaspersky researchers wrote.
Magniber, WannaCry and Stop/Djvu were among the ten Trojan families most detected by Kaspersky.
Bangladesh, Yemen, and Taiwan were the top three countries most targeted by ransomware Trojans.
Microsoft Office Vulnerabilities Favored
Cybercriminals particularly favored Microsoft Office services’ vulnerabilities. They represented 69.10% of all exploited vulnerabilities.
“The reporting period was remembered for a number of dangerous vulnerabilities in business applications, like CVE-2023-34362, CVE-2023-35036 and CVE-2023-35708 in MOVEit Transfer or CVE-2023-23397 in Microsoft Outlook,” noted the researchers.
Read more: MOVEit Exploitation Fallout Drives Record Ransomware Attacks
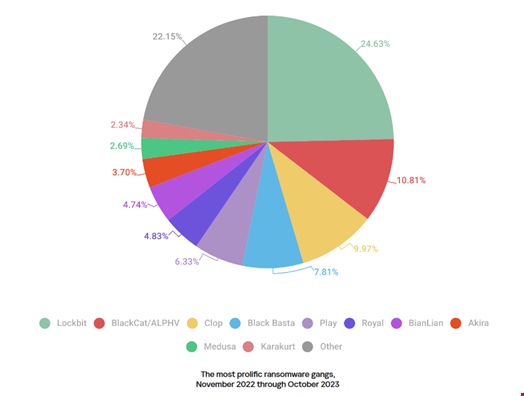
LockBit, BlackCat and Clop Most Prolific
According to Kaspersky’s telemetry, the most prolific ransomware group was LockBit, which claimed a 24.63% share in the total number of victims published on all the groups’ data leak sites.
LockBit was followed by ALPHV/BlackCat (10.81%) and Clop (9.97%).
Read more: ALPHV Second Most Prominent Ransomware Strain Before Reported Downtime
Vladimir Kuskov, Head of Anti-Malware Research at Kaspersky, commented: “Adversaries continue to develop new malware, techniques and methods to attack organizations and individuals. The number of vulnerabilities reported is also growing annually, and threat actors, including ransomware gangs, use them without hesitating.”
“Furthermore, the entry barrier into cybercrime is now being lowered due to the proliferation of AI, which attackers use, for example, to create phishing messages with more convincing texts. In these times, it is essential both for large organizations and for every regular user to embrace reliable security solutions.”
All figures in the report, which covers the period from November 2022 through October 2023, come from the Kaspersky Security Network (KSN) global cloud service. Data was obtained from users who had consented to it being sent to KSN.


