- How to uninstall the iOS 26 beta on your iPhone (and why you might want to)
- AI agents will be ambient, but not autonomous - what that means for us
- I replaced my premium headphones with this classic Bose pair - and didn't regret it
- A year after testing, these Nothing earbuds are still my all-time favorites
- All Pixel Watch 3s are on sale at Best Buy - save $70 on the LTE model
Defend Against Cyber Espionage Attacks

Risk Management
Explore Trend Micro’s latest research into Void Balaur, a prolific cybermercenary group, to learn how to defend against attacks launched by this growing group of threat actors.
Read time: ( words)
We recently discussed the rise of cybercriminal groups such as ransomware-as-a-service. While these cybercrime syndicates are based on specific motivations, another group, dubbed “cybermercenaries”, has developed to provide cyberattack services, tools, and even training to anyone willing to pay. Trend Micro Research took a deep look into the group’s activities, offerings, targets, and connections, enabling security decision makers to strengthen their defense strategies.
Who is Void Balaur?
Void Balaur (aka Rockethack), active since 2015, is a threat actor that primarily hacks into the mailboxes of email providers and social media accounts using highly specialized malware such as Z*Stealer and DroidWatcher. They also dabble in cyberespionage and data theft, selling valuable information to whoever’s willing to pay. During our investigation, we determined that Void Balaur had targeted over 3,500 victims, some of which were hit persistently and repeatedly. They tend to target organizations and individuals with large amounts of sensitive data, such as mobile and core telco companies, ATM machines and point-of-sale vendors, and FinTech companies and banks.
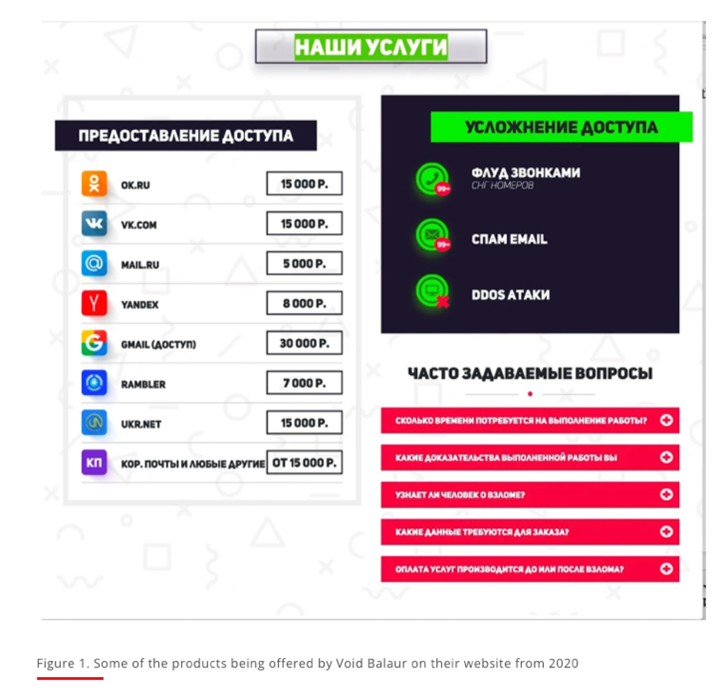
Defending against cybermercenary attacks
By following and learning from the patterns and behaviour of Void Balaur, we can curtail future cybermercenary attacks. These groups have access to a large number of tools and infrastructure, allowing them to launch attacks against prominent targets. However, just because they have a lot of tools, doesn’t mean you need a complicated defense strategy. It’s like using an alarm system to defend your home—it’s effective whether someone tries to break in through a window or a door. The following best security practices can help you thwart cybermercenary attacks:
- Choose a reputable email service that is known to have robust security and high privacy standards
- Use two-factor authentication (2FA) apps instead of relying on SMS
- Use end-to-end encryption for all communication
- Regularly delete older messages to minimize the chance of sensitive data ending up in the wrong hands. You can utilize mobile features that automatically delete chats after a certain period of time.
For more insights into Void Balaur, cybermercenaries, and best security practices, read Void Balaur: Tracking a Cybermercenary’s Actitivites.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

