- I replaced my Ring with this outdoor security camera - and it has no subscription
- This handy USB meter tells you what's actually going on with your ports - and it's only $20
- This budget Lenovo ThinkPad has no business being this good - especially for hybrid workers
- Déjà Vu: What Cloud Adoption Can Teach Us About AI in Cybersecurity
- Motorola to outfit first responders with new AI-enabled body cameras
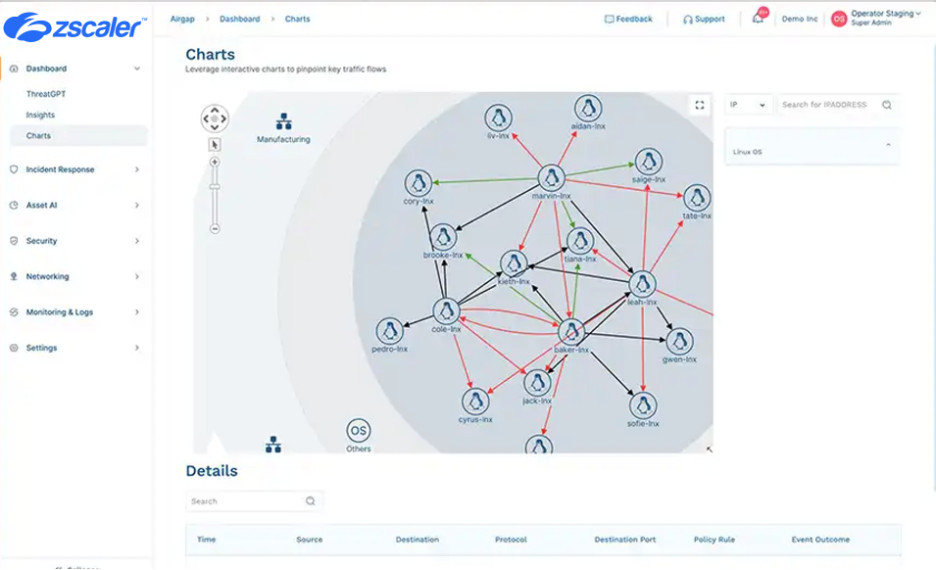
Eliminating Lateral Threat Movement INSIDE factory, branch, and campus networks

For network engineers and security leaders tasked with securing modern enterprise environments, the challenge of preventing lateral threat movement is critical. Inside factory, branch, and campus networks, traditional approaches to segmentation often struggle to keep up with the complexities introduced by IoT, operational technology (OT), and the growing demand IT/OT convergence and modernization. Zscaler’s Zero Trust Device Segmentation aims to solve these challenges by providing a scalable, automated solution that significantly reduces the risk of lateral threat movement without the complexity of traditional network segmentation.
Understanding Lateral Threat Movement
Lateral threat movement refers to the capability of an attacker, once they gain a foothold within a network, to move between devices and resources in search of valuable data or systems to compromise. Traditional segmentation methods, such as VLANs and access control lists (ACLs), provide some level of containment, but their static nature and manual configurations make them difficult to adapt to today’s dynamic networks. Moreover, these approaches often fall short in environments like factories, branches, and campuses, where devices are diverse, legacy machines are common, and security demands are high.
The emergence of IoT and OT devices, which are frequently deployed in factory and branch networks, has further complicated the issue. These devices typically lack robust built-in security, can’t accept agents, and can be highly vulnerable to compromise. Once breached, an attacker can use them as a launchpad to move laterally throughout the network, potentially accessing sensitive information, disrupting critical operations, or even causing injury or death. This risk underscores the importance of implementing a robust strategy that can stop lateral movement before significant damage is done.
OT security risks and ThreatLabz insights
According to Zscaler ThreatLabz research, OT security risks are pervasive in large operating environments. Often more than 50% of OT devices depend on legacy, end-of-life operating systems that have known vulnerabilities. High-risk legacy protocols and services, such as Server Message Block (SMB), Windows Management Instrumentation (WMI), Telnet, Network Basic Input/Output System (NetBIOS), and Remote Desktop Protocol (RDP), frequently make up more than 20% of internal East-West network connections. These legacy systems and services present significant risks, providing potential entry points for attackers to move laterally within a network.
Furthermore, IoT malware attacks have been on the rise. ThreatLabz reported a 45% increase in IoT malware attacks over the past year, with a 12% increase in payload delivery attempts to IoT devices. The manufacturing sector experienced the highest volume of IoT malware attacks, accounting for 36% of all observed blocks. The transportation and food & beverage sectors also remained prime targets due to their extensive reliance on IoT devices, which are often vulnerable to cyberattacks.
Manufacturing networks are increasingly experiencing nearly equal levels of internal (east-west) and external (internet-facing) network traffic, underscoring the complexity of their environments. However, many enterprises struggle with gaining visibility into east-west traffic and effectively segmenting it, making these internal communications vulnerable to lateral movement by attackers.
Current solutions are struggling with East-West
Current approaches of segmenting inside the factory/campus fails to isolate large numbers of endpoints since many devices can’t accept agents, such as legacy machines, headless devices, and IoT.
This yields an Inconsistent segmentation approach across campus and IoT/OT environments and inconsistent, exploitable security. Compromised endpoint attacks and lateral movement often lead to critical infrastructure shutdown, with significant reputational and revenue loss.
East-West Firewalls or NAC solutions are very expensive, and many solutions force costly upgrades and require expensive downtime to deploy. “Segmentation projects that never finish” is a well know phenomenon in the networking world. The resulting solution sprawl has resulted in a lack of consistent east-west visibility, making centralized policy management impossible inside enterprise networks.
Zscaler’s approach to device segmentation
Zscaler’s Zero Trust Device Segmentation addresses the limitations of traditional network segmentation by applying the principles of zero trust to all communications between devices. At its core, zero trust assumes that no device—regardless of its network location—should be trusted by default. This mindset drives Zscaler’s approach to securing device communication within factory, branch, and campus networks.
Zscaler Zero Trust Device Segmentation eliminates lateral threat movement inside branches, factories, and campuses by isolating every endpoint into a secure “network of one.”
Zscaler even automatically discovers and classifies every asset in your critical infrastructure. Zscaler fully isolates every connected endpoint and provides east-west visibility and control over all communication between endpoints in the same or different segments in the campus, branch, and factory.
Zscaler agentless technology deploys in hours without forced upgrades or VLAN re-addressing, and easily isolates legacy controllers, IoT devices, and headless machines. This allows for a unified and consistent segmentation approach, instead of the sprawl of agent-based microsegmentation, NAC and Firewall ACLs.
Zscaler
Key features for network engineers
There are three primary use cases for Zscaler Zero Trust Device Segmentation:
1) OT/IoT device microsegmentation for devices in critical infrastructure that can’t accept agents and might require expensive upgrades or replacement costs. Zscaler shrinks the attack surface by segmenting every IP endpoint into a network of “1”. Our unique agentless architecture protects headless machines. legacy systems and IoT devices which can’t accept agents or be brought offline.
2) East-West Macro-Segmentation and vendor consolidation by removing Firewalls and ACLs that are expensive and hard to maintain. Zscaler deploys in hours and works seamlessly with existing infrastructure – no hardware upgrades or VLAN re-addressing required. Easily macro-segment IT from OT and major production lines and networks.
3). Asset Discovery and Classification, auto applying relevant policies to reduce operational overhead in ever changing environments. Zscaler provides accurate, real-time inventory of 100% of IP devices with full east-west visibility.
Zscaler
Securing factory, branch, and campus environments
In factory settings, operational technology often includes a wide array of legacy and specialized devices that are critical to operations but may not have been designed with security in mind. A compromise in such environments could lead to severe disruptions or safety risks. By segmenting each device individually and enforcing strict communication policies, Zscaler reduces the risk that a compromised IoT or OT device could impact broader operations.
In branch environments, such as retail or office locations, a zero trust approach to device segmentation helps secure communication between different types of devices, such as point-of-sale systems, employee workstations, and connected sensors. Ensuring that only authorized devices can communicate with each other reduces the risk of data breaches and other security incidents that could arise from compromised systems.
On campus networks, which often support a mix of user devices, IoT, and critical infrastructure, Zscaler’s solution provides the visibility and control needed to manage the varied security requirements of different device types. By implementing zero trust segmentation, network engineers can maintain a high level of security across all devices while minimizing the administrative overhead associated with manually configuring and maintaining segmentation policies.
The end of lateral movement
By adopting Zscaler’s Zero Trust Device Segmentation, organizations can effectively put an end to lateral threat movement within their networks. This means that even if an attacker compromises one device, they are unable to move freely within the network to exploit other devices or access sensitive data. Instead, each device remains isolated, and communications are strictly controlled based on dynamic policies that consider device identity, health, and context.
This approach not only stops attacks in their tracks but also simplifies the workload of network engineers. Instead of manually configuring complex segmentation rules and managing countless ACLs, they can rely on Zscaler’s automated platform to maintain secure, isolated environments across diverse network types.
Conclusion
Zscaler Zero Trust Device Segmentation delivers network engineers a fast, powerful way to achieve true zero trust segmentation. Key benefits include:
- Single solution for IT, OT, and IoT
- Shrinks attack surface by segmenting every IP endpoint into a network of “1”
- Agentless architecture to protect headless machines. legacy systems and IoT devices which can’t accept agents
- Deploys in hours and works seamlessly with existing infrastructure – no hardware upgrades or VLAN re-addressing required
- Auto-add new devices with autonomous policy groups for easy Day 2
- Rapid application troubleshooting (IT and OT) based on gathered telemetry
- Accurate, real-time inventory of 100% of IP devices with full east-west visibility
- Lower trouble ticket burden on networking team (OT team can address issues locally)
- Instantly block lateral communication to or from any endpoint when under attack
- Eliminate NAC, east-west firewalls, ACLs, manual VLAN segmentation
The ability to prevent lateral threat movement is critical in today’s increasingly interconnected enterprise environments. Zscaler’s Zero Trust Device Segmentation offers a powerful, automated solution that meets the demands of modern factory, branch, and campus networks without the complexities of traditional segmentation methods. By focusing on granular isolation, rapid deployment, and minimizing manual configurations, this solution helps network engineers secure devices against the ever-present threat of lateral attacks.
To learn more, please register for our upcoming Zero Trust For Branch and Cloud launch event, and hear from Jay Chaudry, CEO of Zscaler on how you can end lateral threat movement inside your enterprise: https://www.zscaler.com/innovations-launch/zero-trust-segmentation

