- I've yet to find a retro stereo amp that delivers sound as accurately for various genres than this
- Use AI at work? You might be ruining your reputation, a new study finds
- Why Whoop's policy change has fans fuming
- Apple now sells refurbished iPhone 15 models at discounted prices (including the Pro Max)
- The best no-log VPNs of 2025: Expert tested and reviewed
Email Nightmare: 94% of Firms Hit by Phishing Attacks in 2023

Email security remained top of mind for cybersecurity professionals in 2023 as over nine in ten (94%) cyber decision-makers had to deal with a phishing attack, according to email security provider Egress.
This is up 2% from the previous year, Egress’ Email Security Risk Report 2024 found.
The top three phishing techniques used throughout 2023 were malicious URLs, malware or ransomware attachments and attacks sent from compromised accounts.
Additionally, phishing threat actors became more efficient, with 96% of targeted organizations negatively impacted by these attacks, compared with 86% during the previous year.
For instance, 58% of organizations suffered account takeovers in 2023, of which 79% came from credentials harvested through phishing.
Jack Chapman, VP of threat intelligence at Egress, commented: “Organizations continue to face vulnerabilities when it comes to advanced phishing attacks, human error, and data exfiltration, and analyzing emerging trends will be key to bolstering defenses.”
AI-Powered Email Threat Looms
The report also shows that cybersecurity leaders are aware that phishing is a serious concern for their businesses. A staggering 95% of them said they are stressed about email security.
They are also closely monitoring the use of new AI tools like large language models (LLMs) and deepfakes on phishing attacks, with 63% of respondents saying they are “being kept at night” by deepfakes and 61% by AI chatbots.
“Email security isn’t a case of ‘if it ain’t broke, don’t fix it’.”Jack Chapman, VP of threat intelligence, Egress
Moreover, many cybersecurity leaders question how efficient their cybersecurity defenses against email-based attacks are.
Of those who use a secure email gateway (SEG), 91% expressed frustration with it and 87% are considering replacing their SEG or have already done so.
Employees Still Pay the Price for Their Mistakes
This frustration is sometimes passed on to staff, with cybersecurity leaders taking a tough stance on employees.
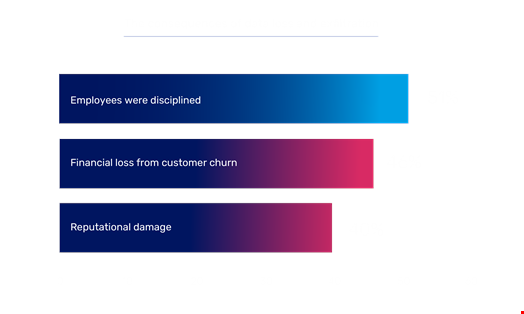
The study has found that among employees who fell for a phishing attack, 51% were disciplined, 39% were fired, and 27% voluntarily left their jobs.
This is despite a lack of efficient training provided to staff, the report highlighted. Overall, 91% of cybersecurity leaders have doubts about the effectiveness of traditional training.
Therefore, in most cases, training is not tailored to the workforce, with only 19% of organizations delivering security awareness training that reflects on the department or team that employees work in.
Instead, training is frequently seen as a checkbox exercise – for compliance purposes only in 88% of cases.
Egress’ Chapman warned: “This isn’t a case of ‘if it ain’t broke, don’t fix it’. Organizations urgently need to adapt their approach, or risk finding themselves in the same position next year.”
Read more: Is MFA Enough to Protect You Against Cyber-Attacks?
The survey data for this report was compiled from 500 cybersecurity leaders, including CISOs and CIOs, from the US, UK, and Australia, and working in the financial services, legal, healthcare, and government or charitable sectors.
All respondents used Microsoft 365 as their operating system and were responsible for email security. The survey data was supplemented by platform data generated by Egress Defend and Egress Prevent.

