- Select Prime members can get Kindle Unlimited for 3 months at no cost - here's how
- Modernization means putting developers in the driver’s seat
- Get a free iPhone 16 Pro for free from T-Mobile, no trade in required - here's how
- The LG C4 OLED for $800 off is one of the best Prime Day TV deals right now
- Prime members can save $10 on any $20 or more Grubhub+ order for a limited time - here's how
Enforcing Multi-Cloud Security Compliance
Managing security risk in the cloud can be overwhelming. The velocity of new threats is unprecedented. Rewards for bad actors have never been higher, or the barriers to entry lower. Unlimited resources of nation states and organized crime mean more targeted and more sophisticated attacks. Protecting your organization from threats can often seem futile.
Security professionals must, therefore, take a pragmatic approach to risk management. As in many areas of life, a Stoic approach can help make the unmanageable manageable.
I recently moderated a lively discussion between CISOs at an industry event. The prevailing sentiment was that the most effective risk mitigation ensures the basics are in place to strengthen the foundation. External threats are not keeping these professionals awake at night, but missing something within their control (that can result in exposure) is.
“Is this something that is, or is not, in my control?” Epictetus
Where do I start?
 Here again, ancient philosophy has us covered. “No need to reinvent the wheel”. The Center for Internet Security (CIS) maintains a comprehensive, prioritized list of controls to help protect your organization and data from threats:
Here again, ancient philosophy has us covered. “No need to reinvent the wheel”. The Center for Internet Security (CIS) maintains a comprehensive, prioritized list of controls to help protect your organization and data from threats:
- CIS Controls identify 18 areas that are critical to an organizations security posture.
- CIS Benchmarks provide a granular, actionable list of configuration updates to support these controls.
The benefits of benchmarks
CIS Controls are comprehensive (and proven) enough that many compliance frameworks map to them for their own compensating controls. For example, PCI DSS , HIPAA, and ISO 27001.
CIS Benchmarks provide practical configuration details for hardening operating systems and cloud environments, grouped across 3 levels:
- Level One (base recommendations)
- Level Two (defense-in-depth)
- STIG (Defense Information Systems Agency Security Technical Implementation Guides)
Therefore, the implementation of CIS Benchmarks can provide organizations with a strong security foundation and help meet the requirements of industry specific compliance framework(s).
The reality of benchmarks
Yet while CIS controls have been available since 2009, benchmark implementation has been spotty. Consisting of hundreds of pages of manual configuration recommendations, achieving compliance is iterative and time consuming. And while full compliance undoubtably results in more secure systems, are they even functional?
The reality is that benchmarks are valuable technical assets, but with a couple of caveats:
- They must be customizable
- They must provide on-going evaluation and automated remediation
Without those capabilities, benchmark assessments simply become another noise generator, increasing the friction between security and operations teams.
Effective Compliance across Clouds
The use of benchmarks and compliance frameworks requires an on-going approach to assessment and remediation, one that includes your traditional on-prem workloads as well as new constructs as you adopt additional cloud services. This makes continuous compliance impossible to manage manually, no matter how many resources you throw at it.
VMware Cloud Management takes a comprehensive, holistic approach with programmatic solutions to help organizations comply with industry standard benchmarks and frameworks or to create their own.

CloudHealth Secure State
CloudHealth Secure State continually assesses cloud workloads against security rules mapped to industry standard (CIS, GDPR, HIPAA, ISO 27001, MITRE ATT&CK Cloud, NIST, PCI, & SOC 2) and custom created frameworks.
Assessment against a framework is as simple as “publishing” that framework. Frameworks map to control groups, which map to control settings. CloudHealth Secure State provides granular control at each level to help improve compliance according to your organizations unique security and regulatory needs. An intelligent risk scoring algorithm makes it easy to identify critical findings, and exception and suppression capabilities help to reduce false positives.
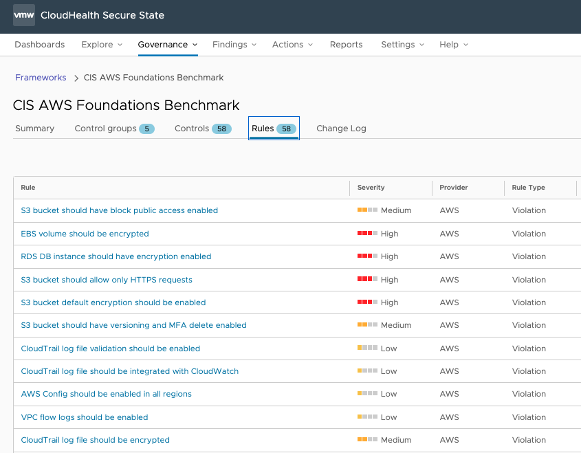
CloudHealth Secure State takes a unique approach to automated remediation, using a worker (docker image) to trigger the change, therefore maintaining read-only access (least privilege) for your cloud accounts within the service. And we open sourced the worker code so that customers can customize, create, and share their remediation jobs.
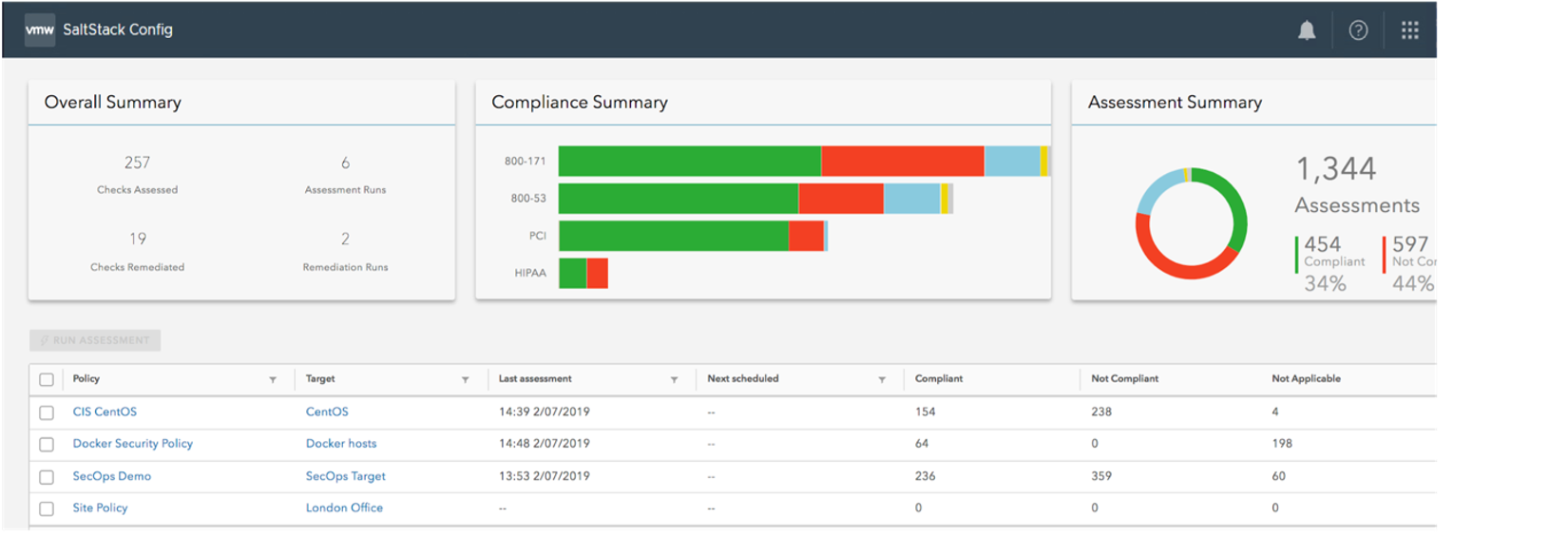
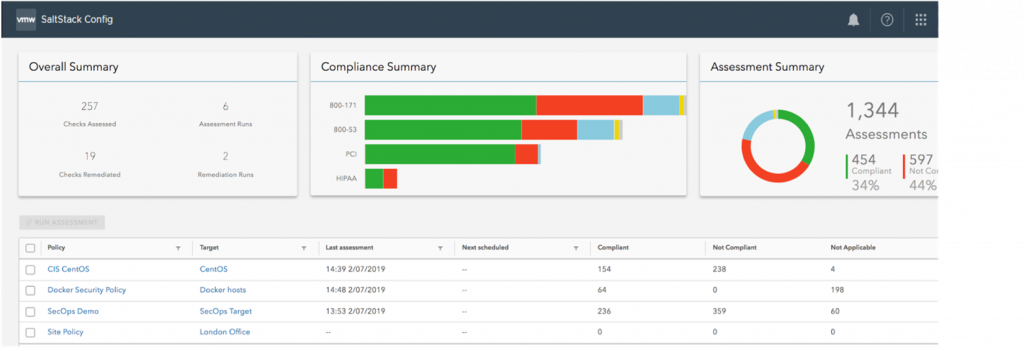
SaltStack SecOps
vRealize Automation SaltStack SecOps ensures compliance at the Operating System (OS) level, providing a live database of certified content for CIS and DISA STIGs.
Here again, compliance policies can be customized to meet the unique needs of your organization. Automated enforcement is achieved through the underlying vRealize Automation SaltStack configuration management framework, preventing configuration drift and ensuring that compliance is consistent and not a once-a-year activity.
Conclusion
Keeping your organizations workloads and data secure can be a moving target. Adherence to consistent, proven security fundamentals helps to mitigate security risk by reducing the exposed attack surface. Compliance against CIS benchmarks provide an effective way to enforce security controls and provide a strong foundation to many industry standard frameworks. Effective multi-cloud compliance requires a programmatic approach that supports multiple cloud providers, allows for framework customization, and delivers continuous, automated configuration remediation.
The VMware Cloud Management platform delivers these capabilities and more, enabling security professionals to effectively utilize benchmarks and frameworks to strengthen their cloud and OS security posture wherever their workloads reside.

