- If we want a passwordless future, let's get our passkey story straight
- This Week in Scams: $16.6 Billion Lost, Deepfakes Rise, and Google Email Scams Emerge | McAfee Blog
- Proof-of-concept bypass shows weakness in Linux security tools, claims Israeli vendor
- SAP NetWeaver customers urged to deploy patch for critical zero-day vulnerability
- Lenovo targets AI workloads with massive storage update
ENISA Launches First State of EU Cybersecurity Report

European institutions are likely to experience disruptions due to cyber-attacks in the near future, according to a report by the EU’s Cybersecurity Agency (ENISA).
In its first-ever Report on the State of Cybersecurity in the Union, published on December 3, ENISA said the cyber threat level to the EU between July 2023 and June 2024 was substantial.
This means that EU entities were likely directly targeted by threat actors during the reported period or could be exposed to breaches via recently discovered vulnerabilities.
There was a notable escalation in cyber-attacks during the reported periods according the ENISA, setting new benchmarks in the variety and number of incidents and their consequences.
Additionally, severe disruptions of essential and vital entities or EU institutions, bodies, and agencies (EUIBA) due to future cyber-attacks are considered a realistic possibility.
“As geopolitical and economic tensions grow, cyber warfare escalates with espionage, sabotage, and disinformation campaigns becoming key tools for nations to manipulate events and secure a strategic advantage,” the report read.
DDoS and Ransomware, Top Threats
Denial-of-service (DoS) and ransomware attacks were the most reported forms of attack and accounted for more than half of the events observed, followed by threats against data.
“Hacktivist activity is increasing and becoming more unpredictable. They use common tactics, such as DDoS attacks and website defacements, but also ‘Fear, Uncertainty, and Doubt’ (FUD) to amplify the impact of their operations. A notable trend is the overlap between state-nexus actors and supposed hacktivists.,” the report highlighted.
Meanwhile, ENISA noted that ransomware remains the most impactful threat for EU member states, with three major trends at play:
- A shift from encryption to data exfiltration
- Small and medium-sized enterprises are now a more attractive target for cybercriminals
- Double extortion becoming the norm for well-established ransomware groups
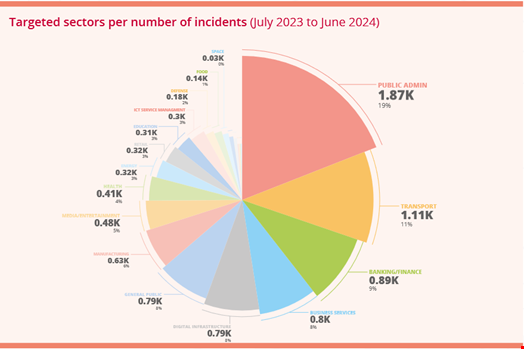
Public administration was the top targeted sector, with 1870 cyber-incidents recorded over the reported period, accounting for 19% of the overall number. Transport and finance came second and third, with 1110 and 890 incidents, respectively.
July 2023 was the busiest month for cyber-attacks observed by ENISA, with 800 single incidents reported that month only. December 2023 was the least busy, with fewer than 300 reported incidents.
Cyber Espionage, Disinformation and Hacker-For-Hire Accelerate
According to ENISA’s analysis of cybersecurity incidents and cyber threats, cyber espionage campaigns targeting EU member-states and EUIBAs are continuous and remain a persistent and severe threat despite limited public reporting.
These originate primarily from Russia-nexus groups, with a focus on EU institutions in order to advance their intelligence on Ukraine and other targets of Russian interests, and China-nexus groups.
The European Parliamentary elections were seen to be a target with information operations aligned with Russian and Chinese interests aimed at influencing the civilian population but did not include any notable or disruptive cyber-attacks.
However, ENISA observed active information manipulation campaigns between December 2022 and the end of November 2023, with EU-based organizations as common targets.
Finally, ENISA described the rise of hacker-for-hire services as “a concerning trend that has gained momentum in recent years.” Hacker-for-hire services contribute to the professionalization of the cybercrime market but also fuel state-nexus actors.
ENISA’s Cyber Policy Recommendations
The report identified four priority areas that EU and EU member-states cyber policymakers should address:
- Policy implementation
- Cyber crisis management
- Supply chain
- Cyber skills
ENISA also outlined six policy recommendations covering the four priority areas above. They are the following:
- Strengthening the technical and financial support given to EUIBAs and national competent authorities and to entities falling within the scope of the NIS2 Directive to ensure a harmonized, comprehensive, timely and coherent implementation of the evolving EU cybersecurity policy framework using already existing structures at EU level such as the NIS Cooperation Group, CSIRTs Network and EU Agencies
- Revising the EU Blueprint for coordinated response to large-scale cyber incidents while considering all the latest EU cybersecurity policy developments
- Strengthening the EU cyber workforce by implementing the Cybersecurity Skills Academy and establishing a common EU approach to cybersecurity training, identifying future skills needs, developing a coordinated EU approach to stakeholders’ involvement to address the skills gap and setting up a European attestation scheme for cybersecurity skills
- Addressing supply chain security in the EU by stepping up EU-wide coordinated risk assessments and the development of an EU horizontal policy framework for supply chain security aimed at addressing the cybersecurity challenges faced both by the public and the private sectors
- Enhancing the understanding of sectorial specificities and needs, improving the level of cybersecurity maturity of sectors covered by the NIS2 Directive and using the future Cybersecurity Emergency Mechanism to be established under the Cyber Solidarity Act for sectorial preparedness and resilience with a focus on weak or sensitive sectors and risks identified through EU-wide risk assessments
- Promoting a unified approach by building on existing policy initiatives and by harmonizing national efforts to achieve a common high-level of cybersecurity awareness and cyber hygiene among professionals and citizens, irrespective of demographic characteristics
ENISA is required by Article 18 of NIS2 to produce a similar report twice a year.
In a public statement, Juhan Lepassaar, the Agency’s Executive Director, commented: “Amidst growing cybersecurity threats, technological advancements, and a complex geopolitical landscape, it is vital to assess our capabilities. Through this process, we can effectively evaluate our maturity levels and strategically plan our next steps.”
Read now: How the New EU Regulatory Landscape Will Impact Software Security

