- I tested a Pixel Tablet without any Google apps, and it's more private than even my iPad
- My search for the best MacBook docking station is over. This one can power it all
- This $500 Motorola proves you don't need to spend more on flagship phones
- Finally, budget wireless earbuds that I wouldn't mind putting my AirPods away for
- I replaced my Linux system with this $200 Windows mini PC - and it left me impressed
Exploring Winrar Vulnerability (CVE-2023-38831) | McAfee Blog

Authored by Neil Tyagi
On 23 August 2023, NIST disclosed a critical RCE vulnerability CVE-2023-38831. It is related to an RCE vulnerability in WinRAR before version 6.23. The issue occurs because a ZIP archive may include a benign file (such as an ordinary .JPG file) and also a folder that has the same name as the harmless file, and the contents of the folder (which may include executable content) are processed during an attempt to access only the benign file.
Our intelligence shows that this vulnerability is being exploited as early as April 2023. Let’s look at a sample exploiting this vulnerability (Hash: bc15b0264244339c002f83e639c328367efb1d7de1b3b7c483a2e2558b115eaa)
- The image below shows that the archive is named trading_system, which hints that it is used to target traders
- We can also see that the threat actor can craft the archive so that folder and file names are the same.
- This is interesting as Windows doesn’t allow files and folders to have the same name in the same path.
- This shows that it was weaponized after creating a regular zip by changing the bytes to make the file and folder name the same.
- Also, note there is a trailing space at the end of the file and folder name (in yellow).
- When we look inside the folder, we see many files, but the most important file is highlighted, which is a bat file containing a malicious script.
- The bat file also has the same name as the benign file outside the folder.
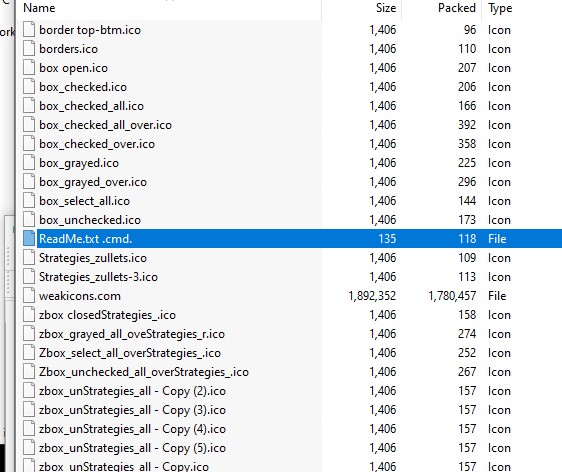
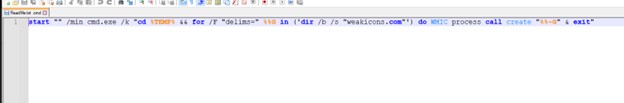
- When we check the script, we see it launches cmd in the minimized state, then goes to the temp folder where WinRAR will extract the files, then tries to find the weakicons.com file, which is present inside the folder and executes it using wmic and then exits.
- Checking weakicons.com we find that it is a CAB SFX file.
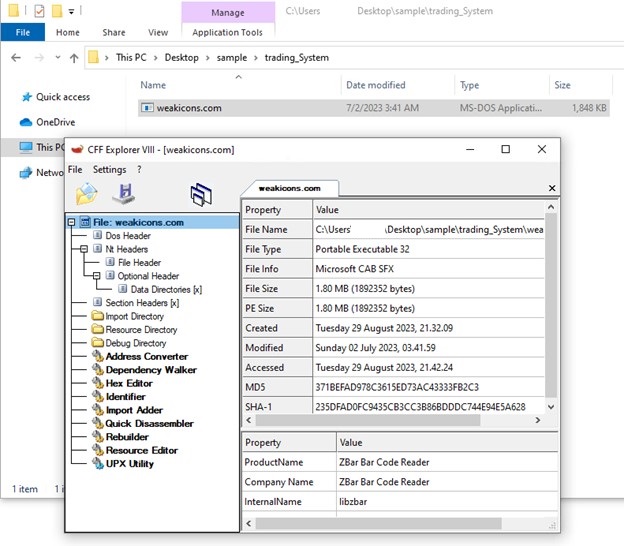
- We extract it to check what is inside.
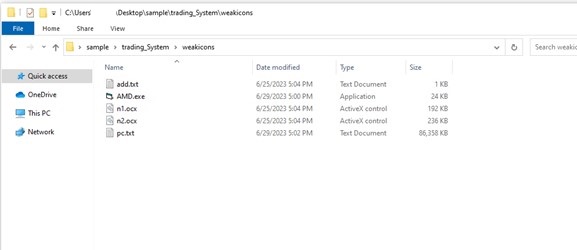
- We found a PE file, some ActiveX control objects, and two text files.
- AMD.exe is a visual basic compiled file whose main job is to extract the dll hidden in a blob of data inside pc.txt and execute the ActiveX controls.
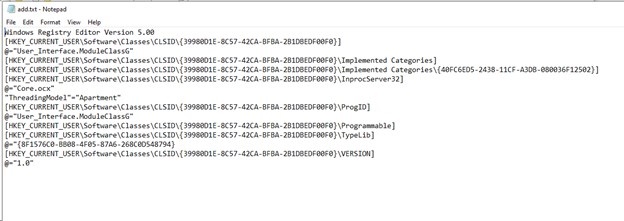
- Inside add.txt, we find the registry keys it will try to manipulate
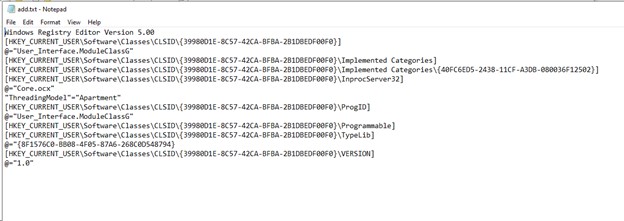
- The first control is responsible for registering a COM object in Windows. During registration, registry keys are imported from the “add.txt” file. As a result, a specific COM object with a unique CLSID is registered in the infected system. The default value of the InprocServer32 key is populated with the path to a malicious DLL named “Core.ocx”.

- Wmic process executes weakicons.com

- AMD.exe extracts the encrypted dll file inside pc.txt and writes it in the romaingnvidia folder.
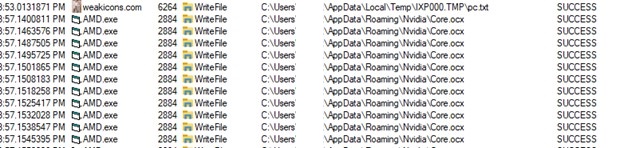
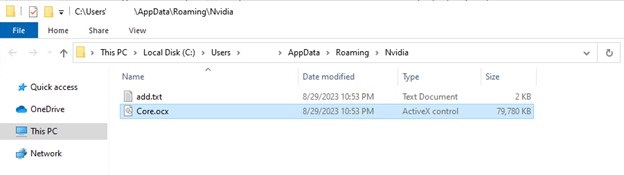
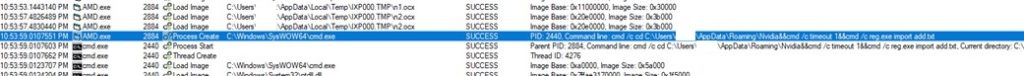
- Here, we observe AMD.exe calls reg.exe on registry keys inside add.txt
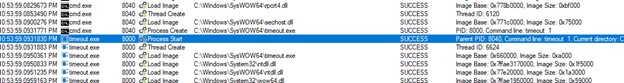
- Timeout is also called to slow down the activities of the infection chain.
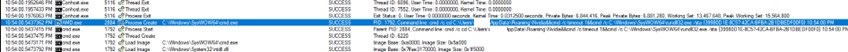
- AMD.exe Calls rundll32 on the clsid that is registered in the registry
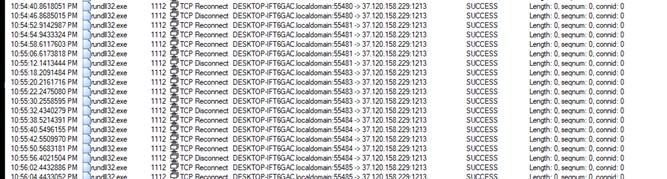
- We can see successful tcp connection to threat actors C2.( ip 37[.]120[.]158[.]229)
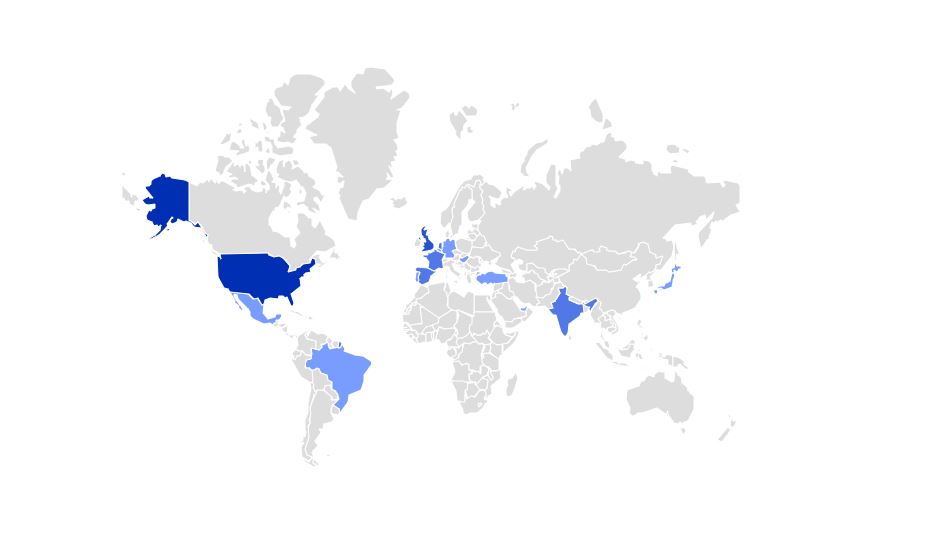
Global Heatmap where this vulnerability is being seen in the wild(based on McAfee telemetry data)
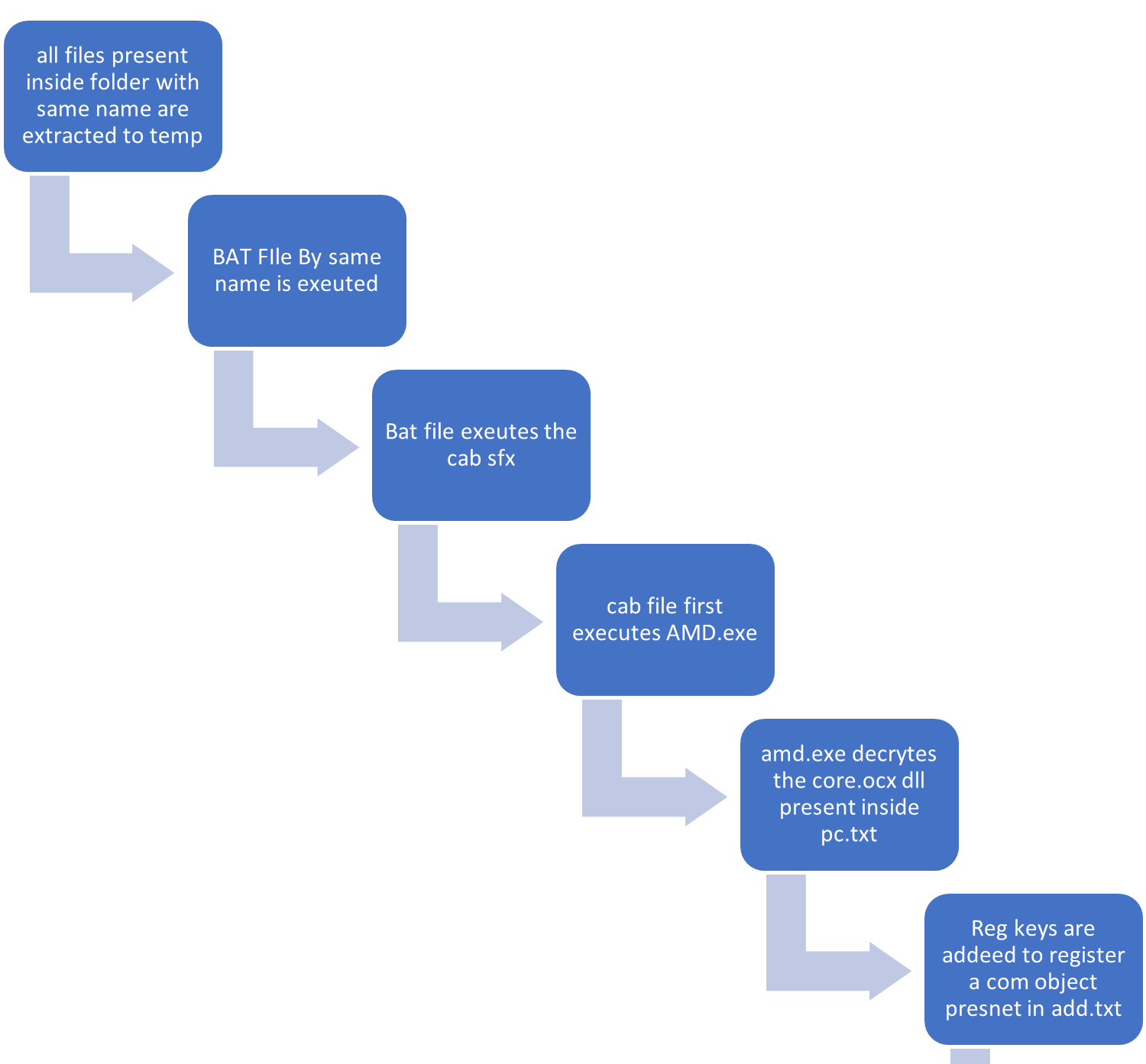
Infection chain
How does the vulnerability work?
- Here, we will analyze the issue causing WinRAR to execute the script instead of opening the image.
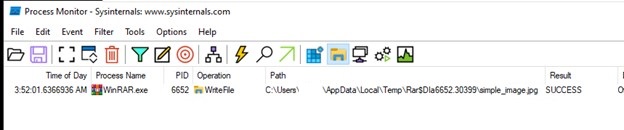
- We will compare how WinRAR behaves when we execute an image file from a weaponized zip vs. a normal zip. So we fire up ProcMon First.
Normal.zip
Weaponized.zip
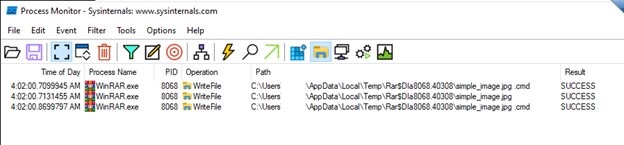
- The above image shows that the first logical bug is how WinRAR is extracting files in the temp folder before executing them. In the case of a regular zip, only the clean image file is extracted to the temp folder, whereas in the case of a weaponized zip, even the files present inside the folder are extracted to the temp folder along with the clean image file. This is due to the same file names we have given, which makes WinRAR extract those in temp.
- Verifying the same in the temp folder
Normal Zip
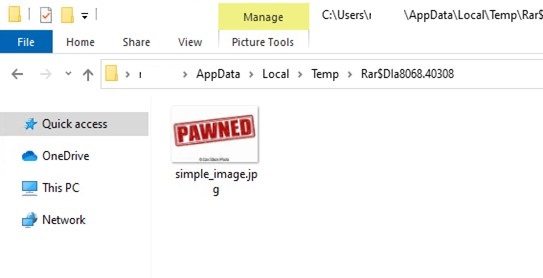
Weaponized Zip
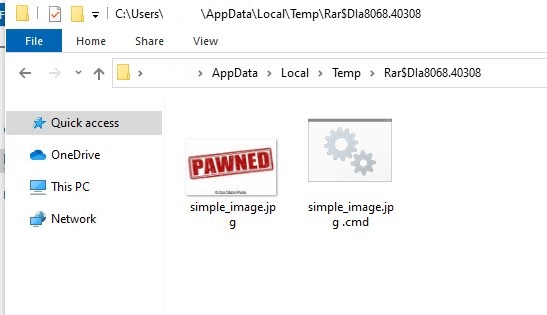
- In Logs, when we dig deep, we can see Winrar searches for our filename with an *, which causes it to iterate over our bat file as it has the same name, which in turn gets executed.
![]()
![]()
![]()
- To see what’s happening under the hood, we hook a debugger and launch WinRAR by manipulating the “image file Execution options” registry key.
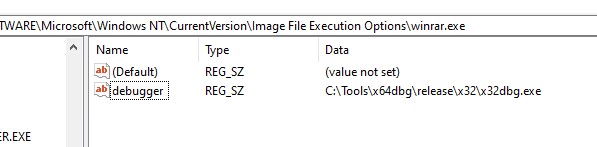
- When we execute the rar file, we see the debugger getting attached to the winrar process so that we can do just-in-time debugging.
- We put a breakpoint on the ShellExecuteExW function to see what parameters are passed to it just after clicking the jpeg file.
- When we double-click on the image file, we can see the debugger is opened, and after a few clicks, we hit our breakpoint.
Normal zip

- In this case, the correct parameter is passed to the ShellExecuteExW function as the file exists at this exact path.
Weaponized zip

- In this case, an incorrect parameter is passed to the ShellExecuteExW function as the parameter contains a trailing space, and such a file does not exist on the disk.
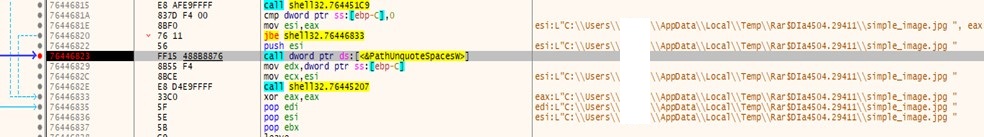
- When we dig deep, we find that later, it calls PathUnquoteSpacesA API call, as per MSDN. It “Removes quotes from the beginning and end of a path.”
- As quotes are removed from the end of the path, ShellExecuteExW executes “simple_image.jpg .cmd” instead of “simple_image.jpg.”
IOC’s
| Sha256 | Detection |
| bc15b0264244339c002f83e639c328367efb1d7de1b3b7c483a2e2558b115eaa | Trojan:Archive/2023_38831.NEAA
|
- .( ip 37[.]120[.]158[.]229)
- REG keys
%APPDATA%NvidiaCore.ocx
Recommendations
- WinRAR users should immediately update to the latest version. WinRAR archiver, a powerful tool to process RAR and ZIP files (rarlab.com)
- Use a licensed and updated McAfee+ subscription to stay protected.
- Stay informed about common cyber threats and tactics used by cybercriminals. This knowledge can help you recognize potential risks and avoid scams.
- Be very cautious when dealing with attachments from unknown sources. Only run attachments that come from trusted sources.
- Protect your accounts by using multi-factor authentication.


