FIN7 threat actor updated its ransomware activity

Researchers from PRODAFT reveal that the infamous FIN7 threat actor updated its ransomware activities and provide a unique view into the structure of the group. Learn how to protect against it.
FIN7 is a threat actor that mostly focuses on stealing financial information, but it also sells sensitive information stolen from companies. This organized group, known as the Carbanak threat actor, presumably started its activities in 2013 and specializes in banking fraud and stealing credit card information using point-of-sale malware. It also compromised ATMs and used malicious scripts on them to get money. The group is known for being technically advanced and highly effective.
To compromise systems, FIN7 uses a variety of methods, such as running phishing campaigns via email or exploiting common vulnerabilities such as ProxyLogon/ProxyShell to penetrate targeted infrastructures. It might also buy stolen credentials in the underground markets, which it tests with tools it developed before using it to access targets’ environments.
FIN7 also makes use of the BadUSB attack, which consists of USB sticks with active payloads simulating a keyboard and being run as soon as the USB device is connected to a computer. FIN7 sent such devices by postal mail as “gifts” to employees in the hospitality or sales business, along with fake BestBuy gift cards to entice the user to use the USB device.
Jump to:
FIN7’s ransomware activity
FIN7 started using ransomware in 2020, being affiliates of a few of the most active ransomware groups: Sodinokibi, REvil, LockBit and DarkSide. It seems the threat actor decided its operations on POS devices were not profitable enough compared to ransomware attacks.
To operate ransomware, FIN7 chooses its target according to public information about companies and their revenues. It aims for companies with high revenue, which might pay ransom quicker than smaller ones. The target’s revenue is also used to calculate the ransom value.
Once the initial access is gained on the target’s network, FIN7 spreads inside the network and steals files before encrypting them via the ransomware code.
SEE: Password breach: Why pop culture and passwords don’t mix (free PDF) (TechRepublic)
Conversation leaks as exposed by PRODAFT researchers indicate that when a ransom is paid, 25% goes to the ransomware developers, and 20% goes to the people responsible for accessing the network and running the technical part of the operation. The highest amount of the rest of the money goes to the head of the team who deals with ransom. The money left after this distribution is spread amongst the group members.
FIN7 can also retarget a company that has already paid a ransom. Conversation leaks between members show that it might come back to the system, if the same vulnerabilities have not been patched, with a different ransomware, therefore pretending it is just another ransomware actor and trying to get a second ransom.
FIN7’s massive and organized structure
Researchers from PRODAFT exposed part of the FIN7 organizational structure, which reveals the main entities of the group: the team lead, the developers, the penetration testers and the affiliates.
The team leaders are masterminds of computer intrusion and ransomware attacks on corporations with a lot of experience. The developers are experienced, too, and they are responsible for the custom tools and malware used by the group.
Affiliates of FIN7 sometimes work for multiple ransomware threat actors. Additionally, they sell credit card information they can steal during their operations.
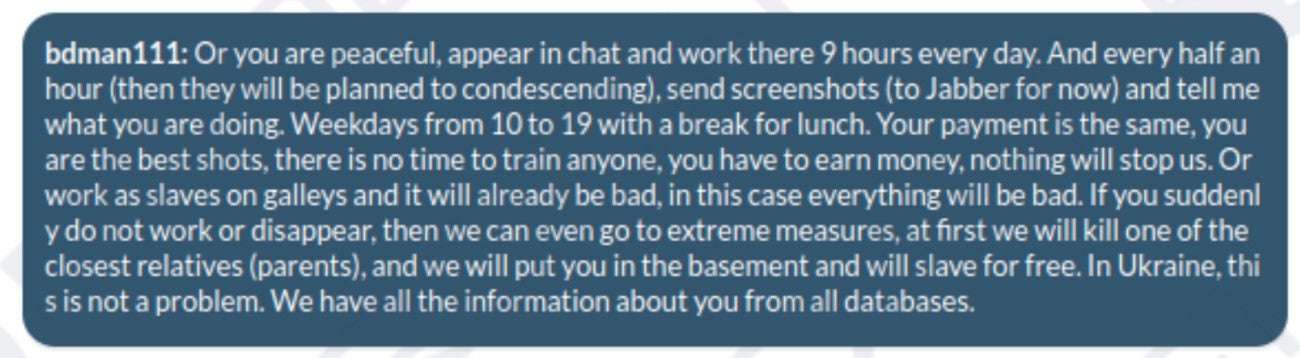
On a more surprising note, it seems the leadership of FIN7 is sometimes using threatening language with its members who do not appear to work enough. It might be as severe as threatening people’s families if a worker wants to resign or escape from responsibilities (Figure A).
Figure A
FIN7’s targets
FIN7 has hit 8,147 targets around the world, with 16,74% of it being in the U.S. (Figure B).
Figure B

Russia is also highly targeted, though the country never appears in later stages of the attack cycle; therefore, this heat map should be considered as a good indicator of large campaigns hitting companies at the first stage, but a lot of those are then not considered worth the effort for the FIN7 threat actor for different reasons. Only a small portion of the more than 8,000 targets are actually attacked and asked for ransom.
How to protect your organization from this cybersecurity threat
All operating systems and their software should always be up to date and patched, since FIN7 sometimes uses common vulnerabilities to hit its target and gain an initial foothold in the company’s corporate networks. Security solutions should also be deployed to monitor endpoint and server behavior and detect fraudulent access attempts.
In addition, multi-factor authentication needs to be deployed wherever possible and especially on any internet-facing system or service. As FIN7 is used to buy valid credentials for companies, MFA might stop them from logging remotely to those systems.
Finally, it is advised to deploy device management software that enables users to control and monitor devices connected via USB, as FIN7 sometimes uses BadUSB attacks.
Security prevention is easier with these TechRepublic Premium downloads: Patch management policy and System update policy.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.

