Fraud Campaign Targets Russians with Fake Olympics Tickets

A broad network of 708 fraudulent web domains is being used to sell fake sporting and musical events tickets, primarily to a Russian-speaking audience, according to threat intelligence provider QuoIntelligence.
Two of these domains, ‘ticket-paris24[.]com’ and ‘tickets-paris24[.]com’, host convincing websites that seemingly allow users to purchase tickets for their preferred events during the upcoming Summer Olympic Games and choose accommodation in Paris.
Researchers at threat intelligence provider QuoIntelligence detected the operation, dubbed Ticket Heist, when scanning for specific keywords associated with the Olympics in late 2023.
Convincing Olympics Ticketing Platforms, Overpriced Tickets
In December 2023, a team at QuoIntelligence started investigating potential fraud schemes aimed at luring people interested in buying tickets for the Paris 2024 Summer Olympic Games, which will start on July 26.
The two Olympics ticketing portals they found had a similar user interface (UI) to legitimate sites, despite minor spelling and grammar mistakes the threat intelligence firm said were likely due to direct translation from Russian to English.
However, one detail caught the researchers’ attention: the displayed ticket prices are inflated compared to those offered by legitimate ticketing sites.
“For example, a random event and seat location on the official website could cost less than €100, whereas the same tickets and locations on the fraudulent websites were priced at a minimum of €300, often reaching €1000,” the report reads.
Based on the domain registrars used and the website content, QuoIntelligence estimated that these websites primarily target Russian individuals worldwide, potentially exploiting their need to bypass sanctions to access certain events.
“The sophistication observed in these fraudulent websites was unexpected, suggesting a high level of motivation and meticulous attention to detail by the attackers behind this campaign. This indicates their intent to maximize the success of their fraudulent activities targeting fans,” added the researchers.
New York-Registered Company, Tbilisi-Based Operators
After trying to buy tickets on the fraudulent websites, the QuoIntelligence researchers found that payments are running via Stripe, a legitimate payment processing platform, and that transactions are permitted only when the victim’s card has sufficient funds.
This suggests that the motivation behind Ticket Heist is to steal money rather than collect bank and credit card information.
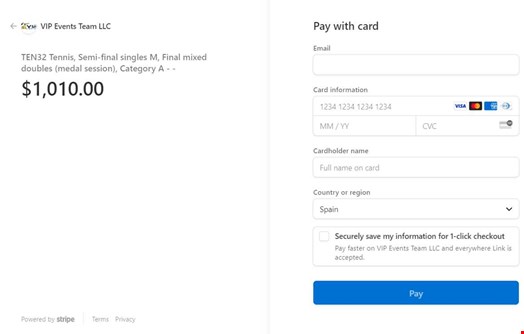
The attempted purchase also led the researchers to find information about the company associated with the fraudulent websites.
The company is called VIP Events Team LLC and was legally formed in New York on November 26, 2021.
However, it does not have a website, and the researchers could not find related information on Google, social media, TrustPilot, or any other available open source intelligence (OSINT) sources.
Although VIP Events Team LLC is likely based in the US, the ‘Contact Us’ page of the ticket-paris24[.]com website lists the company behind the fraudulent site as being located in the country Georgia.
Fake Ticketing Websites Tied to Single IP Address
QuoIntelligence also found other fake ticketing websites leveraging other events, including:
- UEFA Euro 2024 in Germany
- Various concerts and festivals featuring famous musicians and bands (Twenty One Pilots, Iron Maiden, Bruno Mars, Ludovico Einaudi, Metallica and Rammstein)
Some of these domains seem to have a broader target range than the Russian-speaking victims the fake Olympics ticketing sites target.
All domains detected as part of the Ticket Heist campaign point to the same IP address: 179[.]43[.]166[.]54.
Read more: Ticketmaster Extortion Continues, Threat Actor Claims New Ticket Leak

