- I recommend the Pixel 9 to most people looking to upgrade - especially while it's $250 off
- Google's viral research assistant just got its own app - here's how it can help you
- Sony will give you a free 55-inch 4K TV right now - but this is the last day to qualify
- I've used virtually every Linux distro, but this one has a fresh perspective
- The 7 gadgets I never travel without (and why they make such a big difference)
Hackers Use Evilnum Malware to Target Cryptocurrency and Commodities Platforms

The advanced persistent threat (APT) actor tracked as Evilnum is once again exhibiting signs of renewed activity aimed at European financial and investment entities.
“Evilnum is a backdoor that can be used for data theft or to load additional payloads,” enterprise security firm Proofpoint said in a report shared with The Hacker News. “The malware includes multiple interesting components to evade detection and modify infection paths based on identified antivirus software.”
Targets include organizations with operations supporting foreign exchanges, cryptocurrency, and decentralized finance (DeFi). The latest spate of attacks are said to have commenced in late 2021.
The findings also dovetail with a report from Zscaler last month that detailed low-volume targeted attack campaigns launched against companies in Europe and the U.K.
Active since 2018, Evilnum is tracked by the wider cybersecurity community using the names TA4563 and DeathStalker, with infection chains culminating in the deployment of the eponymous backdoor that’s capable of reconnaissance, data theft, or fetching additional payloads.
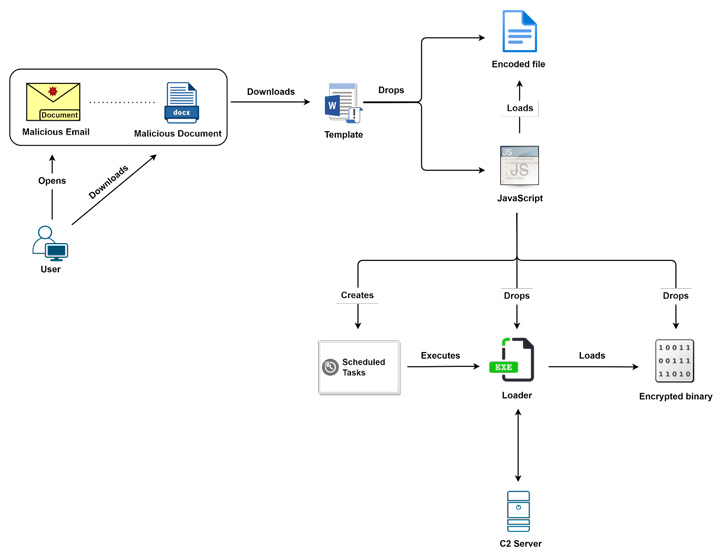
The latest set of activities flagged by Proofpoint incorporate updated tactics, techniques, and procedures (TTPs), relying on a mix of Microsoft Word, ISO, and Windows Shortcut (LNK) files sent as email attachments in spear-phishing emails to the victims.
Other variants of the campaign spotted in early 2022 have made use of financial lures to entice recipients into opening .LNK files within malicious ZIP archive attachments or clicking on OneDrive URLs containing either an ISO or LNK file.
In yet another instance, the actor switched up the modus operandi to deliver macro-laden Microsoft Word documents that drop obfuscated JavaScript code designed to launch the backdoor binary.
This methodology was once again changed in mid-2022 to distribute Word documents, which attempt to retrieve a remote template and connect to an attacker-controlled domain. Regardless of the distribution vector employed, the attacks lead to the execution of the Evilnum backdoor.
Although no next-stage malware executables were identified, the backdoor is known to act as a conduit to deliver payloads from the malware-as-a-service (MaaS) provider Golden Chickens.
“Financial organizations, especially those operating in Europe and with cryptocurrency interests, should be aware of TA4563 activity,” Sherrod DeGrippo, vice President of threat research and detection at Proofpoint, said in a statement. “The group’s malware known as Evilnum is under active development.”
//e&&!t&&(jQuery.ajax({url:”https://thehackernews.com/feeds/posts/default?alt=json&max-results=4″,type:”get”,cache:!1,dataType:”jsonp”,success:function(e){for(var t=””,s=””,r=0;r<e.feed.entry.length;r++){for(var a,l=0;l<e.feed.entry[r].link.length;l++)if("alternate"==e.feed.entry[r].link[l].rel){t=e.feed.entry[r].link[l].href;break}100<(a=(a="content"in e.feed.entry[r]?e.feed.entry[r].content.$t:"summary"in e.feed.entry[r]?e.feed.entry[r].summary.$t:"").replace(/]*>/g,””)).length&&(a=a.substring(0,90));var n=(n=e.feed.entry[r].title.$t).substring(0,50),o=(o=e.feed.entry[r].media$thumbnail.url.replace(//s72-c-e100/,”/s260-e100″));s+=’
“}s+=””,document.getElementById(“result”).innerHTML=s}}),t=!0)})});
//]]>