- Why Whoop's policy change has fans fuming
- Apple now sells refurbished iPhone 15 models at discounted prices (including the Pro Max)
- The best no-log VPNs of 2025: Expert tested and reviewed
- Trump administration to rescind, modify AI chip export curbs
- CTA warns of tariff-fueled price hikes on consumer tech - but it's not all bad news
HardBit 2.0 Wants to Know Victims’ Insurance Coverage
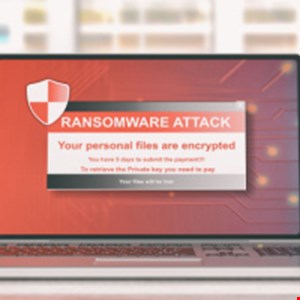
A ransomware group is asking insured victims for details about their policy, claiming it will ultimately lower their risk exposure.
Introduced in November 2022, HardBit 2.0 claims to steal data before encrypting the victim organization’s data, but unusually for such a group it has no leak site and does not use “double extortion” as a tactic, according to Varonis.
Instead, the group apparently threatens further attacks if its demands aren’t met.
“Rather than specifying an amount of bitcoin requested within this ransom note, the group seeks to negotiate with victims to reach a settlement,” Varonis explained in a blog post.
“Notably, as part of these negotiations, victims with cyber-insurance policies are also encouraged to share details with HardBit so that their demands can be adjusted to fall within the policy.”
In this part of the ransom note, the group seeks to portray the victim’s insurer as the enemy, claiming that they will always try to negotiate down on price, even if the policy stipulates much higher coverage. The inference is that this approach could result in the group leaking stolen data or refusing to offer a decryption key.
“Since the sneaky insurance agent purposely negotiates so as not to pay for the insurance claim, only the insurance company wins in this situation,” the ransom note reads.
“To avoid all this and get the money on the insurance, be sure to inform us anonymously about the availability and terms of insurance coverage. It benefits both you and us, but it does not benefit the insurance company. Poor millionaire insurers will not starve…”
HardBit victims should be aware that most policies specifically prohibit the sharing of this kind of information with ransomware actors.
The malware itself appears to be fairly standard, performing various pre-encryption steps to expose the victim network, such as deleting the Windows backup utility catalog and the Volume Shadow Copy Service (VSS). It also disables various Windows Defender features, and terminates scores of services linked to data backup/recovery tools and endpoint security solutions, Varonis said.

