- 5 ways you can plug the widening AI skills gap at your business
- Forget AirTag: This Bluetooth tracker is my top pick for both iPhone and Android users
- This midrange robot vacuum cleans as well as some flagship models - and it's 50% off
- You may qualify for Apple's $95 million Siri settlement - how to file a claim today
- This 3-in-1 robot vacuum kept my floors clean all season, and it's priced to compete
How Businesses Can Turn the Expanding Attack Surface into an Opportunity
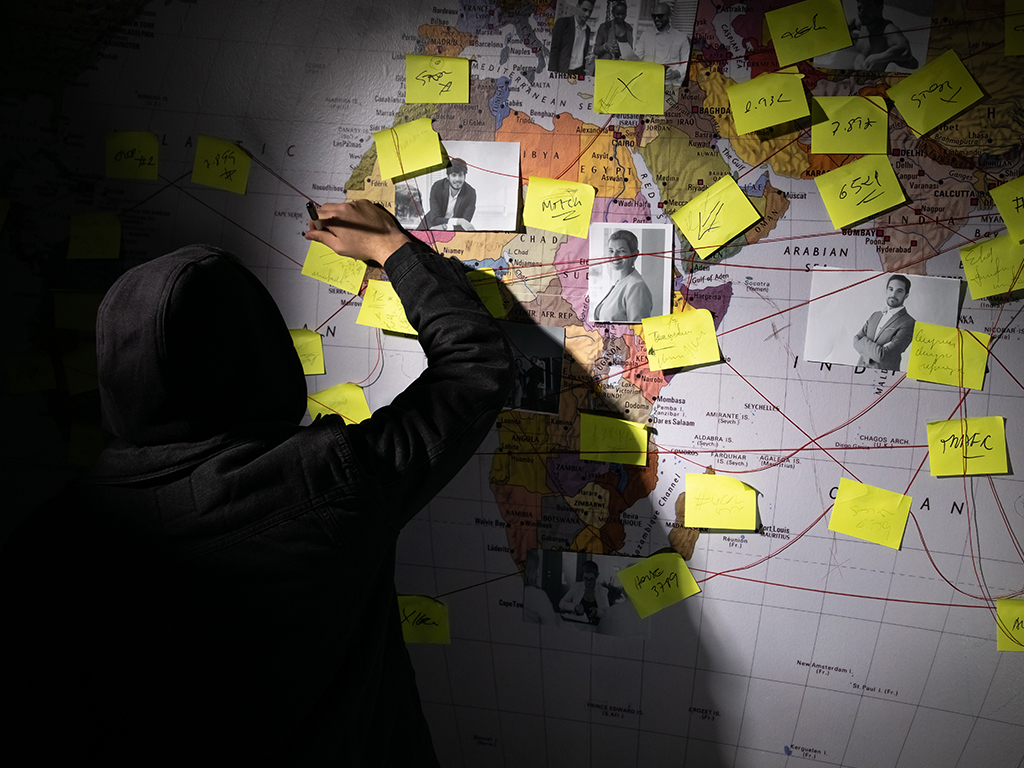
Only 42% of companies discover breaches through their own security teams. CISOs are often “blind” to third-party security practices and crucial data pipelines. This lack of transparency and reliance on their providers to keep their data safe invites an ongoing trade-off between security and accessibility. It works both ways. Service providers also want access to real-time information to heighten their security practices that organizations may deem too confidential to share. So where do CISOs and service providers draw the data-sharing line?
In a Gartner survey of 100 executive risk committee members, 84% said that third-party risk incidents resulted in disruption to operations. Financial loss, increased regulatory scrutiny, and reputational damage were all additional consequences. The cost of a third-party cyber breach is typically 40% more than remediating an internal security violation—which bumps up third-party risk management considerably high on CISOs’ priority lists.
Confidentiality, integrity, and availability are three focal points. Who has data access, is it valid, and how can authorized users access it? CISO leaders have to manage these three things internally and across their vendor community.
Cybersecurity firms can evaluate potential partners’ security posture without direct involvement, but organizations often struggle to identify which vendors have read or write permissions to sensitive information. Manual procedures and fragmented data frequently hinder efficient vendor assessments, making them complicated and time-intensive. In essence, it is difficult to understand context when monitoring entirely from the “outside-in”
Let’s take a closer look at the expanding attack surface, the blind spots to clear, and how to manage risks accordingly.
The Expanding Attack Surface
Malicious actors can exploit weaknesses in the third party’s systems or connections, often with less effort than attacking the primary target directly. Supply chain attacks, targeting third-party vendors, directly affected 134 organizations and indirectly impacted 657 more, exposing over 203 million individuals.
Since supply chain attacks occur through vulnerabilities in another element of the value chain, the compromised third party might already have trusted access or connections. The attackers can leverage these to gain unauthorized access to sensitive systems or data, bypassing many security measures.
Dynamic environments with multiple access points and shared resources, such as cloud environments and IoT contribute to the Third-Party Risk Management (TPRM) challenge. Businesses also need to be careful with remote workers, particularly if they handle sensitive data as employees may use personal devices or networks that are not adequately secured.
The Third-Party Risk Blind Spot
TPRM is often neglected or under-resourced. Common reasons include a lack of visibility into third-party security practices, overreliance on self-attestations as opposed to independent verification, and limited staff dedicated to TPRM.
More than 62% of respondents reported a lack of resources as the biggest obstacle to better safeguarding their organizations from third-party breaches. Almost two-fifths (37%) said they need to double their current staff dedicated to third-party security.
Not only are organizations relying on a mounting number of service providers, but these providers are also gaining customers, increasingly complicating the attack surface. Since not all parties have the same risk level, they will also have varying security measures. Failing to assess data security throughout the relationship lifecycle, including vendor’s data processing, transfer, storage, and disposal security measures, can create vulnerabilities.
Shadow data is a critical third-party risk blind spot. This unmanaged data resides in unknown locations, often with third parties, and was the source of 35% of breaches in 2024. These breaches are more expensive ($5.27M average), take longer to detect (26.2% longer), and more time to contain (20.2% longer, 291 days total). Because organizations lack visibility into shadow data, assessing accurate third-party risk in-house is increasingly tricky to achieve.
A Practical Framework for Effective TPRM
Risk management is no longer a “nice-to-have.” Nine in 10 respondents say their organization has directly invested in their TPRM program. However, a lack of strong program coordination is evident, as only 31% of respondents describe their program as highly coordinated. While 51% report some coordination, this suggests significant room for improvement.
Without proper coordination throughout the risk management lifecycle, they can end up wasting resources and creating new blind spots. The key principles to follow include:
- Identify and Classify: Organizations need a comprehensive inventory of all third-party relationships and must classify them based on risk level (data access, criticality of services, etc.). This must be updated every time a change (such as a new supplier, or a software update) happens to any party involved.
- Due Diligence: The essential elements of third-party due diligence include security questionnaires, on-site audits (for high-risk vendors), penetration testing, and vulnerability scanning. CISOs can leverage the Shared Assessments Standardized Information Gathering (SIG) questionnaire to help build, customize, analyze, and store vendor assessments for managing third-party risk.
- Continuous Monitoring: The most crucial—and laborious part—is the ongoing monitoring of third-party security posture. Cybersecurity software that can automate and streamline workflows within this process helps.
- Contractual Obligations: Get it right from the beginning with transparent, thorough security and data protection clauses in third-party contracts. However, don’t get too comfortable. These need to be checked and reworked overtime.
- Incident Response Planning: A joint incident response plan with key third parties will protect you with a contingency plan if (and when) an unexpected event occurs.
- Communication and Collaboration: The more up-to-date with each other you are, the better. Aim for open communication and collaboration with third parties on security matters.
With the scale and uses of third parties across an organization’s supply chain, CISOs must rethink their data lifecycle and how to protect it in all its states. They must think about securing data from theft and manipulation, and assess all access points across their third-party networks. Organizations can use data discovery and classification to detect sensitive data and ensure the correct access controls and encryptions are in place. By working with third-party security teams and centralizing TPRM, they can gain better visibility into shadow data, spot malicious drifts more quickly, and ensure proactive measures are in place to prevent data leakage.
About the Author
Norman Menz, CEO of cybersecurity SaaS platform Flare. He joined the company in 2021. Earlier in his career, Norman developed a number of information security and IT risk programs but decided to focus his attention on the biggest information security risk to organizations; which is the loss of data due to third-party relationships. Norman is a thought leader on third party and external information security risk and regularly speaks at industry events on the importance of understanding and mitigating risk associated with third parties. He is a Certified Third-Party Risk Professional (CTPRP) and a contributor to the Shared Assessment’s Risk Assessment Body of Knowledge.
Norman received his university degree in Business Management and has been pursuing entrepreneurial activities in technology since before becoming a Seton Hall University Pirate.
Norman can be reached on LinkedIn and at our company website https://flare.io/

