- T-Mobile's data breach settlement payments finally rolling out this month - after April delay
- Cisco unveils prototype quantum networking chip
- What’s Next for MCP Security? | Docker
- Zero Trust: Begin your journey with these first steps
- Ready to ditch Windows for good? This is the Linux distro I recommend for beginners
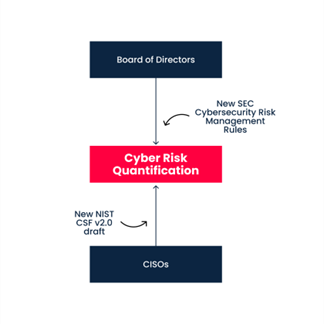
How Cyber Risk Quantification can Help Align CISOs with the Board.
By Lior Bar-Lev, VP Strategy & BizOps, CYE
Recently, the American National Institute for Standards and Technology (NIST) released a draft version 2.0 of its “notorious CSF”—the Cybersecurity Framework. The new version, which is open for public comments and remarks until November 4th, includes major changes. Among them is that we were introduced to a new, capitalized version of its colloquial name, “The Cybersecurity Framework,” instead of the modest “Framework for Improving Critical Infrastructure Cybersecurity.” This change represents not only maturing self-confidence, but also a conceptual shift in its scope: Now the framework refers to all organizations, regardless of industry, size, or location. These organizations receive not only recognition in the new CSF version, but also brand new, expanded guidance on implementing the CSF.
Among additional updates, perhaps the biggest change that demonstrates not only a quantitative expansion in the topics covered by the framework, but a qualitative conceptual shift of it, is the addition of “Govern.” This is the sixth function to join the previously known pentagon of “Identify; Protect; Detect; Respond; and Recover.”
The addition of the Govern function emphasizes, as the National Institute stated, “that cybersecurity is a major source of enterprise risk, ranking alongside legal and financial risks as considerations for senior leadership.” By officially acknowledging cyber risk as an incremental part of organizational risk, the NIST experts have contributed a milestone brick to the never-ending bridge-building journey between CISOs and management, which aims at solving one of cybersecurity’s biggest problems.
The Disconnect between Boardrooms and CISOs
So what’s the problem? Cybersecurity is technical; therefore, it tends to be disconnected from the business.
In a recent study that was published in the Harvard Business Review, 600 board members were surveyed about their attitudes and activities around cybersecurity, revealing alarming insights into the disconnect between companies’ boardrooms and their CISOs. According to Lucia Milică and Dr. Keri Pearlson’s study, only 67% of board members believe human error is their biggest cyber vulnerability, although findings of the World Economic Forum indicate that human error accounts for 95% of cybersecurity incidents. This might be an indicator that some boards do not understand the organizational risk they face.
Further, half of survey participants value CISO cybersecurity expertise the most, followed by technical expertise (44%) and risk management (38%). This suggests that even though cybersecurity topics may have made it onto the agenda, the board still sees them as technical issues. We get a better glimpse of this “dialogue of the deaf” with the finding that while 65% of board members think their organization is at risk of a material cyberattack, only 48% of CISOs share that view, and yet 76% of board members believe they have made adequate investments in cyber protection.
When cybersecurity is regarded solely as a technical matter by boards, it transforms into an operational concern that might not receive adequate focus during their meetings. Due to the time constraints within board meetings, it becomes challenging to get into the depth required for effective supervision. Directors might refrain from posing tough questions, as they might feel insufficiently skilled to formulate comprehensive queries or grasp the responses entirely. However, perceiving cybersecurity as an organizational concern shifts the conversation from being technical to being a managerial obstacle. As cybersecurity is embraced as a strategic necessity for the organization, it gains relevance for discussions at the board level.
Bringing Cyber Risk Management to the Board
And how can this be accomplished? As with every good compromise, the answer is somewhere in the middle of the road. Recently, the U.S. Securities and Exchange Commission (The SEC) officially adopted new rules on cybersecurity risk management, strategy, governance, and incident disclosure by public companies. During the review process of the suggested amendments, one specific rule “garnered significant comment”—the rule suggested to require disclosure about the cybersecurity expertise, if any, of a registrant’s board members. After considering the comments, the SEC decided not to adopt the amendment, as they were “persuaded that effective cybersecurity processes are designed and administered largely at the management level, and that directors with broad-based skills in risk management and strategy often effectively oversee management’s efforts without specific subject matter expertise, as they do with other sophisticated technical matters.”
While this doesn’t sound like a compromise, it is admittedly difficult to ensure that every board of every American public company includes a cybersecurity expert; there are simply not enough of them. But the main issue here is not about the SEC telling boards they don’t have to understand cybersecurity. The issue is about the SEC instructing the management teams, and specifically the CISOs, to talk risk management with the board.
Answering the “How” Question
From the other end, the new NIST CSF v2.0, with the addition of the Govern function, emphasizes the CISO’s responsibility to “[e]stablish and monitor the organization’s cybersecurity risk management strategy, expectations, and policy.” In this advanced approach, it is as if NIST experts are saying to the CISOs, “Your decision-making must be aligned with the organization’s management (that you’re hopefully a part of).” The skillset and scope of responsibility of the CISOs are no longer just about memorizing 108 controls that answer the question of WHAT to do, but also about answering the HOW question: “How can the organization achieve and prioritize the outcomes of the other five Functions in the context of its mission and stakeholder expectations?”
Governance activities are critical for incorporating cybersecurity into an organization’s broader enterprise risk management strategy. They require an understanding of organizational context; the establishment of cybersecurity strategy and cybersecurity supply chain risk management; roles, responsibilities, and authorities; policies, processes, and procedures; and the oversight of cybersecurity strategy.
The combination of the two—regulators instructing boards of disclosure of a registrant’s risk management, strategy, and governance regarding cybersecurity risks, and a standardized cybersecurity framework that instructs CISOs to think, plan, and act in a broader organizational context of risk management strategy—may not be a revolution in the way we navigate cybersecurity. However, it is definitely the evolution of both CISO and BoD roles that we’ve been waiting for.
The Role of Cyber Risk Quantification
If “The Answer” is indeed in the middle of the road, what is that middle? Well, the fusion between cybersecurity expertise and business-oriented risk management is cyber risk quantification. This is the only way both CISOs and board members can talk the same language, as the numbers they receive in the end are the result of deep knowledge from both ends:
From the cybersecurity perspective: You have to know exactly what the threats are to your organization. “Threats” are not endless lists of vulnerabilities, hopefully ordered by generic CVSS criticality, coming from automatic scans. “Threats” are high-quality data on existing gaps, real potential attack routes coming from cybersecurity assessments conducted by independent red teams, with probability and likelihood evaluations of every step.
From the organizational risk perspective: You have to properly identify the organization’s business critical assets, then have a deep understanding of the potential financial impact in case of a breach to any of these assets.
This information is then combined with the likelihood of all possible attack routes to the organization, providing the board and the CISO with a full understanding of the organization’s cybersecurity posture. Only then can real strategic conversations begin, allowing for stakeholders to approve budgets and initiate projects. Only then can cybersecurity become scalable.
Want to learn more about how cyber risk quantification can help you communicate with the board? Contact us.
About the Author
 Lior Bar- Lev, VP Strategy & BizOps
Lior Bar- Lev, VP Strategy & BizOps
Lior leads the Strategy and Business Operations department at CYE, which orchestrates business functions through the company’s rapid growth. In his previous position, Lior had a key role in CYE’s Customer Operations department where he guided a diverse portfolio of clients, helping them navigate across all aspects of resilience enhancement. Prior to joining CYE, Lior had an eleven-year career in the IDF. In his last role as Major (res.), he led the Defense Policy & Governance in the IDF Cyber Defense Division. Lior holds a B.A. in political science, a B.A in Middle-Eastern history, an M.A. in Security studies, and a CISO diploma.
Lior can be reached online at https://www.linkedin.com/in/liorbarlev/ and at our company website https://cyesec.com

