- My top 3 distraction-free writing apps that helped me write dozens of novels
- Every iPhone model compatible with Apple's iOS 26 (and which ones aren't)
- What CIOs need to know about using AI agents for business transformation
- Google Gemini will let you schedule recurring tasks now, like ChatGPT - here's how
- iOS 26 isn't just about a rebrand and Solarium - here's what else is coming
How ransomware is evolving as a threat to organizations
Cybercriminals know they can make money with ransomware and keep getting bolder with their demands, says Palo Alto Networks’ Unit 42.
Image: Getty Images/iStockphoto
Ransomware has emerged as one of the most pernicious security threats to organizations and one that has proved to be lucrative for the criminals who practice it. Many victims simply choose to pay the ransom to get up and running again, especially if they lack any feasible way to recover their data. But ransomware operators are getting savvier and more daring, leading to increasingly costly incidents for compromised organizations.
SEE: Ransomware: What IT pros need to know (free PDF) (TechRepublic)
A report released Wednesday by Unit 42, the threat intelligence team at Palo Alto Networks, looks at how ransomware has evolved and provides advice on how to protect your organization. To create its “2021 Ransomware Threat Report,” Unit 42 worked with Palo Alto Networks’ Crypsis incident response team to analyze ransomware based on their collective data across the U.S., Canada and Europe.
The state of ransomware
First and foremost, Unit 42 found a surge in ransomware demands affecting organizations throughout the world. In 2020, the average ransomware demand hit $312,493, almost triple the amount of $115,123 in 2019. The highest demand reached $30 million last year, up from $15 million over the previous few years. Further, the highest amount paid by a victim shot up to $10 million in 2020 from $5 million in 2019.
The coronavirus pandemic paved the way for audacious attacks against hospitals and healthcare facilities, which was the most targeted sector last year. Cybercriminals attacked these types of organizations knowing that they couldn’t afford to lose access to critical data as they sought to conduct research into COVID-19 and help patients afflicted with the virus.
The double-extortion tactic also gained more traction in 2020. In this type of attack, the criminals threaten to leak the encrypted data publicly unless the ransom is paid. As such, even victimized organizations that have backups of the stolen data may be more willing to pay the ransom to avoid exposure. At least 16 different ransomware variants are now using the double-extortion plot, according to Unit 42.
Many attackers have shifted their campaigns from high-volume “spray-and-pray” models to more focused “stay-and-play” approaches. With the latter, hackers take more time to learn about their victims and networks following the initial breach.
Ransomware operators continue to breach networks through the usual methods. Those include phishing campaigns, using weak or compromised Remote Desktop Protocol credentials and exploiting software vulnerabilities. For the initial access, many rely on commodity malware such as Dridex, Emotet and Trickbot. After breaking into a network, attackers often use built-in tools such as PSExec and PowerShell to move laterally.
Some of the top ransomware families observed by Unit 41 include Ryuk, Maze (ChaCha), Defray777, WastedLocker, GandCrab + REvil, NetWalker, DoppelPaymer, Dharma, Phobos and Zeppelin. Each group has its own set of tactics and specialties. For example, Ryuk uses spray-and-pray campaigns to hit government agencies, healthcare facilities and high tech organizations. Maze engages in more targeted attacks against the finance, transportation and logistics, telecom and communications sectors.
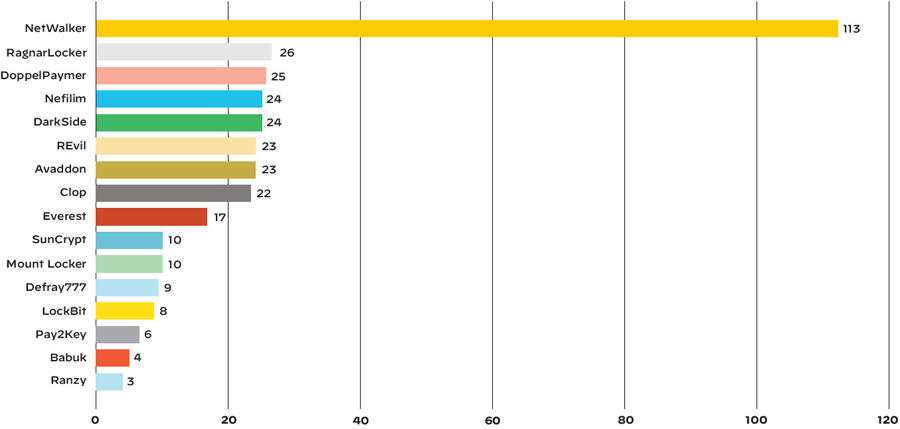
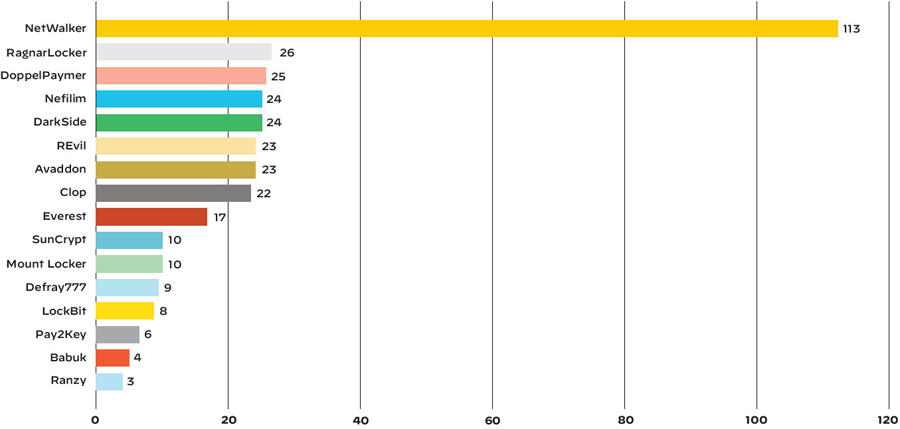
The number of victimized organizations hit by each ransomware family with their data publicly leaked in 2020.
Image: Unit 42
The future of ransomware
Looking at the future of ransomware, Unit 42 anticipates a few ongoing and ever increasing trends. The ransomware-as-a-service model, in which people contract out a ransomware job to criminals for hire, is likely to expand. More attackers are expected to capitalize on the double-extortion strategy. New and updated ransomware variants will continue to be created and deployed. And as long as attackers keep getting paid, ransomware demands will keep rising.
Recommendations
To help your organization protect itself against ransomware, Palo Alto Networks offers the following advice:
- Combat initial access. Organizations should maintain user awareness and training for email security as well as consider ways to identify and remediate malicious email as soon as it enters an employee’s inbox. Organizations should also conduct proper patch management and review which services may be exposed to the internet. Remote desktop services should be correctly configured and secured, using the principle of least privilege wherever possible, with a policy in place to detect patterns associated with brute-force attacks.
- Have an effective backup and recovery process. Organizations should continue to back up their data and keep an appropriate recovery process in place. Ransomware operators will target on-site backups for encryption, so organizations should ensure that all backups are maintained securely offline. Recovery processes must be implemented and rehearsed with critical stakeholders to minimize downtime and costs to the organization in the event of a ransomware attack.
- Employ the right security controls. The most effective forms of protection from ransomware are endpoint security, URL filtering or web protection, advanced threat prevention (unknown threats/sandboxing) and anti-phishing solutions deployed to all enterprise environments and devices. While these will not guarantee prevention, they will drastically reduce the risk of infection from common variants and provide stopgap measures, allowing one technology to offer a line of enforcement where another may not be effective.


