- The 13 best early Prime Day 2025 deals under $25
- Are Amazon Basics tools any good? I bought a bunch to find out, and you'd be surprised
- VMware Product Release Tracker (vTracker)
- Cisco Live 2025: Collaboration Reimagined for the Agentic AI Era
- How Reddit's new AI ad tools help brands join the conversation
How to better combat malware delivered through email

A majority of security pros said they’re most concerned about malicious payloads sent to employees via file attachments, according to a survey from GreatHorn.
Image: iStock/Igor Kutyaev
Phishing emails are one of the most common and successful ways to infect an organization with malware. Employees who’ve been instructed not to click on file attachments and links in unexpected emails still can’t seem to resist the temptation. Once triggered, a single malicious payload can lead to data breaches, ransomware and other devastating threats. A report released Wednesday by security firm GreatHorn looks at the risks of email attachments and suggests ways to defend your organization against such malicious payloads.
Based on a survey of 256 cybersecurity professionals conducted in the U.S. in late March, the report found that 52% of them are most concerned with malicious payloads being delivered via email, while 47% are most worried about such payloads being delivered by a hyperlink within an email.
SEE: Identity theft protection policy (TechRepublic Premium)
For many, ransomware was one severe side effect of a malicious payload. Among the respondents, 54% said their organizations were targeted by ransomware over the past 12 months. Of those that were targeted, 66% actually paid the ransom, with some shelling out as much as $1 million and more.
Some 71% of those surveyed said they’re most concerned about email as the gateway toward ransomware, 75% said that ransomware has increased over the past year, and 62% expect ransomware to continue to increase even after the COVID-19 pandemic ends.
In one example cited by GreatHorn, a Trojan named Troj/Phish-HUP released in February 2021 targeted Microsoft Windows systems, primarily in finance departments. The culprits deployed the Trojan through spearphishing emails masquerading as normal messages in which the recipients expect to download a file. The emails were inspected by Microsoft 365 or Google Workspace. Because such products take time to detect and isolate known malware, the attacks were able to sneak through, according to GreatHorn.
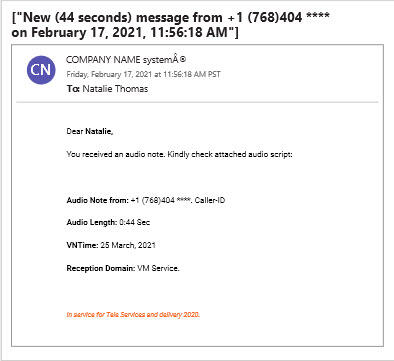
Image: GreatHorn
To protect your organization and employees against malicious email attachments and links, GreatHorn offers the following three tips:
- Attachment inspection. Use security technology that can inspect file attachments in emails. The product should be able to scan content, filenames and attachment types of incoming messages. It should also be able to quarantine all malicious payloads upon delivery to prevent the threat from affecting your organization.
- URL inspection. Use a tool that can detect malicious URLs in an email. Such URLs are a key entry for phishing attacks as attackers can easily tweak them so that no two appear the same. Your email security should inspect all URLs to identify links to malicious websites. It should also use time-of-click analysis to protect against links to websites that appear to be safe on delivery, but are later weaponized with malware.
- Behavioral analytics. Your security defenses also need to leverage behavioral analytics. The tool should take advantage of machine learning algorithms to analyze all communication between senders and recipients. Adaptive threat analytics can learn specific types of email attributes and behaviors and then detect any anomalous signs that may indicate suspicious or malicious content.


