- Learn with Cisco at Cisco Live 2025 in San Diego
- This Eufy robot vacuum has a built-in handheld vac - and just hit its lowest price
- I highly recommend this Lenovo laptop, and it's nearly 50% off
- Disney+ and Hulu now offer prizes, freebies, and other perks to keep you subscribed
- This new YouTube Shorts feature lets you circle to search videos more easily
How to Enhance Application Security Posture with Docker Scout Policies | Docker

With the proliferation of open source components, integrity and reliability within the software supply chain are paramount. This article explores how Docker Scout policies serve as a catalyst, fostering collaboration between development and security teams to define and achieve an ideal application security posture for organizations. Let’s dive into the capabilities that make Docker Scout an indispensable asset in the pursuit of improved security.
Step 1: Use Docker Scout policies for SecOps efficiency
Docker Scout dashboards become a security team’s trusted companion, providing a seamless and intuitive interface to utilize out-of-the-box policies. These policies offer a rapid comparison between the ideal and current states of application security, effectively highlighting areas requiring attention. To give security teams a head start, these out-of-the-box policies come with default configurations that can be updated to reflect internal requirements and standards.
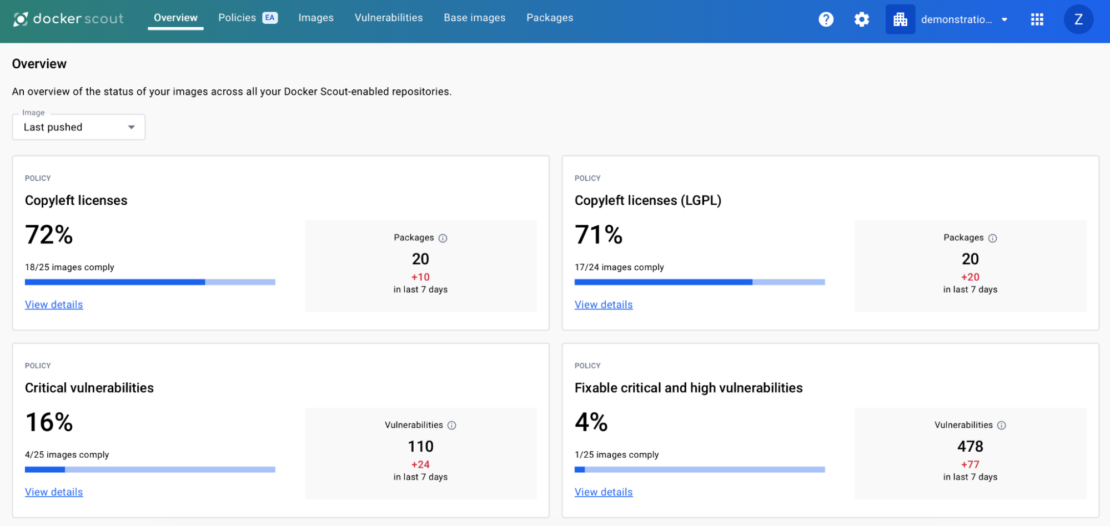
Step 2: Gauge the impact of security policies
Docker Scout dashboards are more than visual aids; they are powerful tools for understanding an organization’s current application security posture. Offering an overall summary and compliance status checks against defined standards enables security teams to gauge the impact of security policies. For example, the critical CVE policy showcases the percentage of images with no critical CVEs (Figure 1).
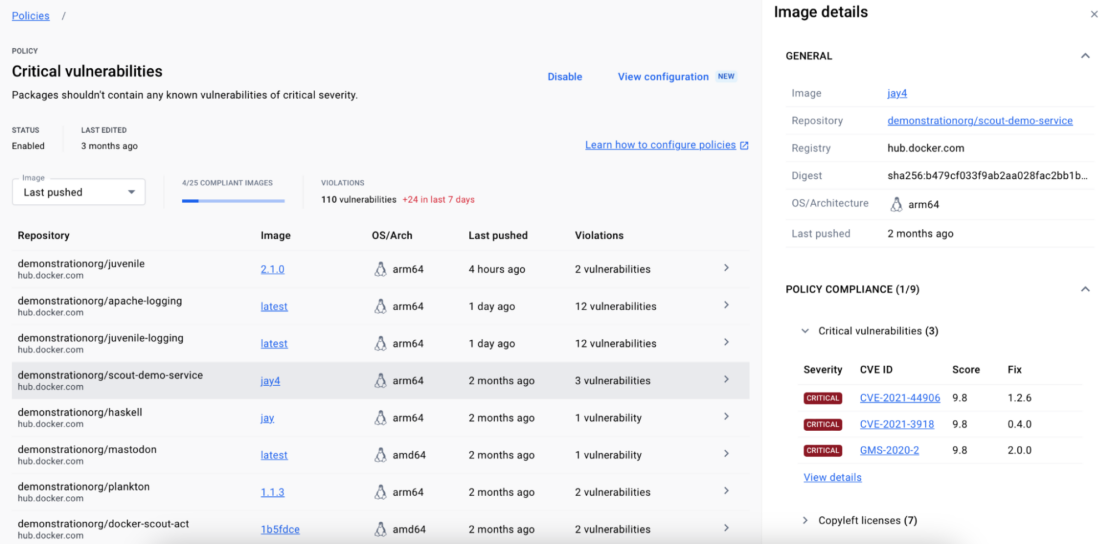
Step 3: Drill down for actionable insights
Docker Scout dashboards offer an intuitive approach to analyzing information and gaining deeper insights. For example, selecting View details on any of the policies provides comprehensive information about nonconforming images. Moreover, it precisely indicates the location of vulnerabilities within an image. This user-friendly feature ensures that teams can identify problematic images with just a few clicks and understand the right next steps to initiate effective remediation (Figure 2).
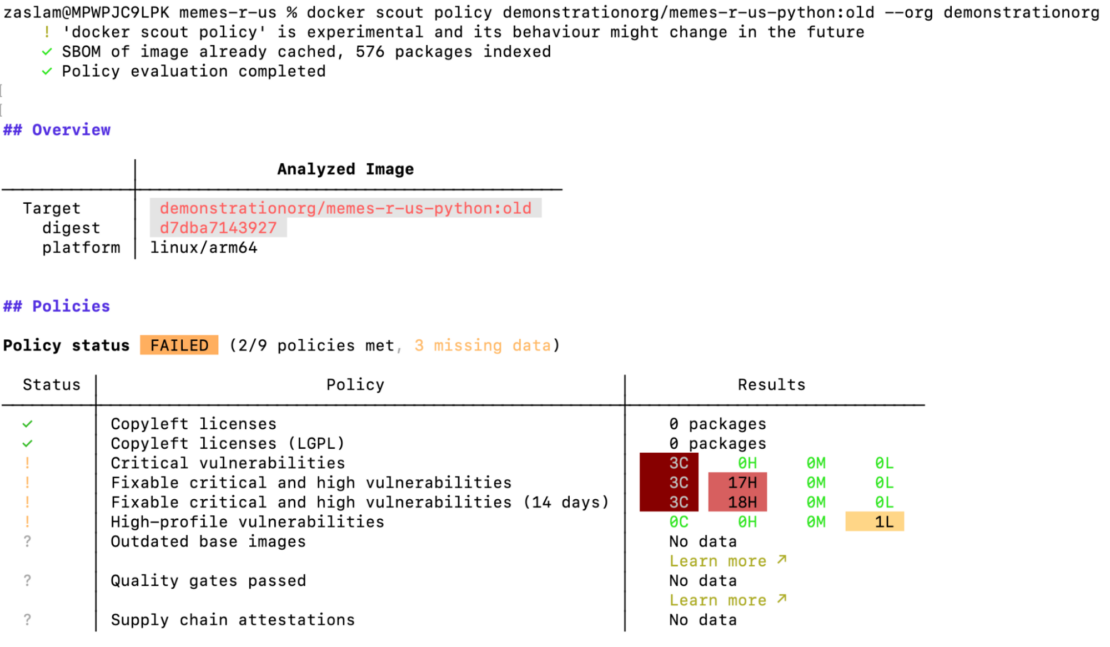
Step 4: Use Docker Scout CLI at the point of development for quick feedback
Docker Scout becomes an integral part of developers’ workflows, allowing them to work seamlessly with their preferred tools, such as the CLI. For example, developers can run a simple docker scout policy command in the CLI to receive instant feedback on image compliance with company policies. This integration significantly reduces feedback loops, saving valuable time and boosting developer productivity (Figure 3).
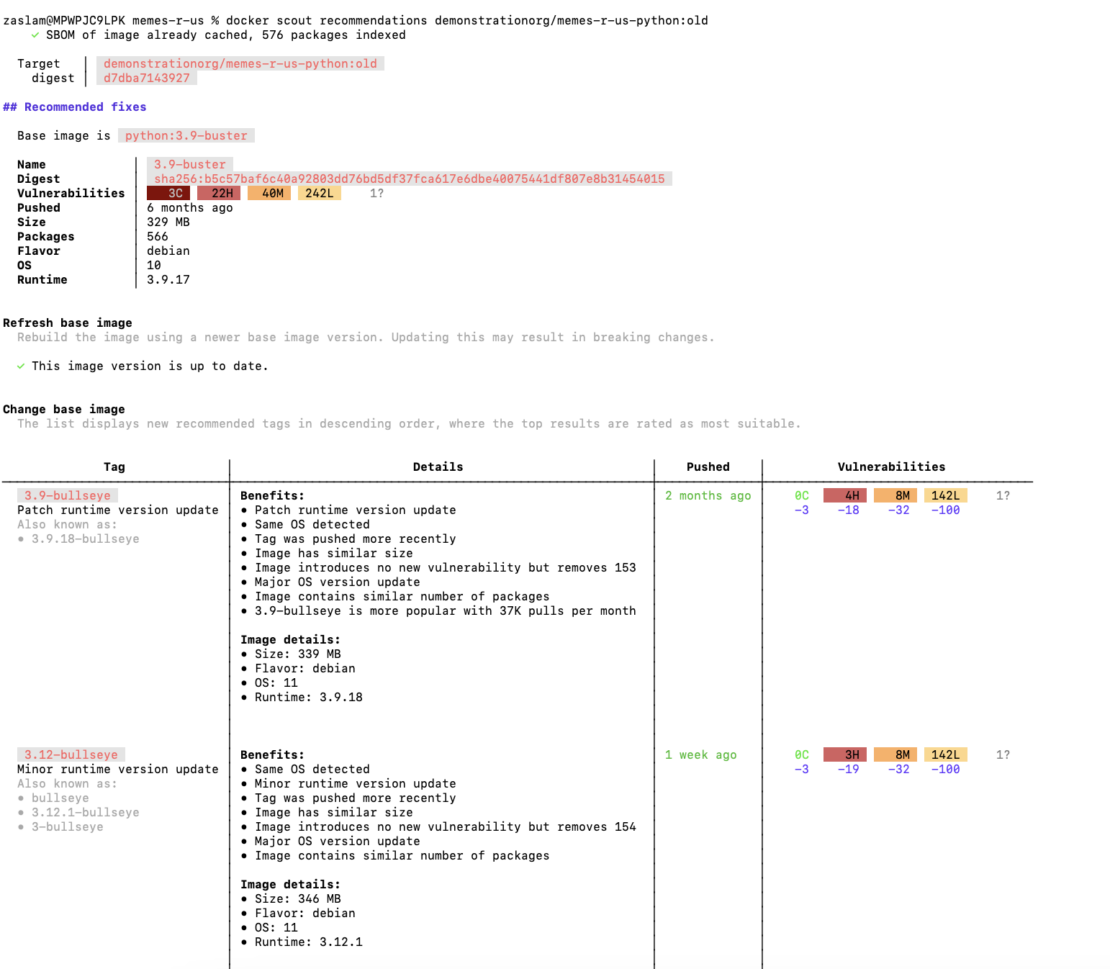
Step 5: Get recommendations for seamless issue resolution
Docker Scout goes beyond merely identifying issues; it provides actionable recommendations for developers. For example, running the docker scout recommendations command offers easy-to-understand next steps (Figure 4). Developers can now swiftly address issues, such as updating a base image, without needing to scour the web for solutions. Docker Scout simplifies the process, allowing developers to jump into their preferred workflows with confidence.
Conclusion
Docker Scout is more than a security product — it’s a business enabler. Docker Scout’s integrated solutions enhance developer productivity and empower cross-functional teams to confidently deliver secure applications to production faster. By seamlessly bringing together the development and security teams, Docker Scout policies become a driving force in achieving a secure and streamlined software development lifecycle. Elevate your security efforts with Docker Scout policies and unlock collaborative efficiency.

