- I recommend the Pixel 9 to most people looking to upgrade - especially while it's $250 off
- Google's viral research assistant just got its own app - here's how it can help you
- Sony will give you a free 55-inch 4K TV right now - but this is the last day to qualify
- I've used virtually every Linux distro, but this one has a fresh perspective
- The 7 gadgets I never travel without (and why they make such a big difference)
How to Identify Compromised Microsoft Exchange Server Assets Using Tenable

As organizations continue to respond to a flurry of attacks by HAFNIUM and other threat actors leveraging Proxylogon (CVE-2021-26855) and related vulnerabilities (CVE-2021-26857, CVE-2021-26858, CVE-2021-27065), Tenable has released a plugin to help you identify potentially compromised assets.
Background
Microsoft published an out-of-band advisory for four zero-day vulnerabilities in Microsoft Exchange Server on March 2 in response to in-the-wild exploitation of these flaws by a nation-state threat actor known as HAFNIUM as well as several other threat actors. Initial reports suggested that over 30,000 organizations may have been compromised as a result, but that number has since been revised to over 60,000.
On March 9, Microsoft found more than 100,000 publicly accessible Exchange servers were still vulnerable. On March 12, Microsoft said that number had decreased to 82,000, which shows that while efforts to patch have been successful, there are still many Exchange servers exposed, leaving them vulnerable to attacks.
On March 11, Michael Gillespie, founder of the ID Ransomware service, discovered a new ransomware family called DearCry targeting vulnerable Exchange servers. This was subsequently confirmed by Microsoft Security Intelligence.
We have detected and are now blocking a new family of ransomware being used after an initial compromise of unpatched on-premises Exchange Servers. Microsoft protects against this threat known as Ransom:Win32/DoejoCrypt.A, and also as DearCry.
— Microsoft Security Intelligence (@MsftSecIntel) March 12, 2021
As more and more organizations focus their efforts on patching these flaws, it is increasingly important for them to take the time to look for signs of existing compromise in the process.
Exchange Server Plugins
Tenable released four plugins since the March 2 out-of-band advisory, including two version check plugins, a direct check plugin and an indicator of compromise (IOC) plugin.
The IOC plugin, identified as plugin ID 147193, can be used by organizations scanning for vulnerable Exchange servers in their environment to collect IOCs. The results from this plugin can aid defenders in determining if attackers successfully compromised their systems.
Examining the output from the IOC plugin
The IOC plugin will flag files in select Exchange Server directories where attackers are known to have implanted webshells. These details can be seen in the output section of the scan results:
In the example above, three files were discovered in these selected directories.
Comparing files from the plugin output against known IOCs
Knowing which files are in these directories is just the first step. The next step is to compare these results against publicly available indicators of compromise associated with these attacks. Fortunately, Microsoft has published a list of IOCs in both CSV and JSON format that list files known to be malicious.
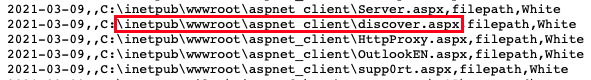
The image above is a section within Microsoft’s list of IOCs. When comparing this list with the output for the IOC plugin, we see that one file, discover.aspx, is a direct match, including the path. This is a strong indication that the attackers implanted a webshell on a vulnerable Exchange Server.
In addition to Microsoft’s list of IOCs, the FBI and the U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued a joint cybersecurity advisory about the Exchange Server attacks and included a list of File Path Indicators to examine for potential compromise.
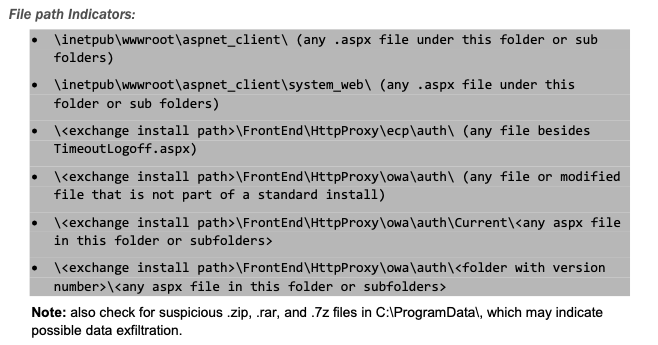
For example, the FBI/CISA advisory calls out the presence of files within the inetpubwwwrootaspnet_clientsystem_web path as well as any file or modified file not part of the standard Exchange Server Install for a number of file paths, including
When we review the output from our IOC plugin, we see there is an aspx file under the system_web path called 1302992a.aspx, as well as a file, HttpProxy.aspx, under the
It is important to note that with more and more threat actors targeting vulnerable Exchange servers, the list of known bad filenames and hashes will continue to grow. We highly recommend reviewing all files within the paths provided by the FBI/CISA and Microsoft.
Solution
Webshells give attackers an effective way to maintain persistent access to a victim’s systems. Once webshells associated with these Exchange Server vulnerabilities have been identified in your environment, it is important to immediately activate incident response processes to remove the webshells and determine the scope of these attacks. Removing the webshells is not just a step to prevent the threat actors who implanted them from maintaining persistence, but to prevent other threat actors from “piggybacking” by scanning for and using them as well, as was recently confirmed by security researcher Marcus Hutchins.
Confirmed my suspicious that someone is scanning for Exchange web shells left behind by Hafnium and trying to piggyback them. Once you patch, make sure to find and remove any web shells left behind.
— MalwareTech (@MalwareTechBlog) March 10, 2021
Frequently Asked Questions
Q: Why didn’t the IOC plugin trigger for all of my Exchange servers?
A: The IOC plugin will only trigger on Exchange Servers where potential IOCs have been found within the identified Exchange Server paths.
Q: How do I know the IOC plugin ran?
A: When reviewing the output for plugin ID 147193, there are two expected results:
| Status | Expected Output Results |
|---|---|
| Potential Compromise Detected | The following .aspx files have been found in directories linked to the Hafnium attack: – |
| Potential Compromise Not Detected | The remote host is not affected as no potential IOCs were found. Note that this does not mean the target is not vulnerable to the Hafnium CVEs. See vendor advisory |
If the plugin runs successfully, you will see one of the two expected outputs above. If you do not see these results after completing a scan, you can refer to this troubleshooting article.
Q: I patched my Exchange servers but the IOC plugin is still triggering?
A: Patching Exchange Servers addresses the underlying vulnerabilities. It does not remediate potential web shells that may have been implanted on those servers through the exploitation of these flaws, which is why the IOC plugin will still trigger even after patches have been applied. If potential compromise is detected, it is important to follow our recommendations to remediate by activating incident response processes to remove any web shells and investigate for further compromise.
Get more information
Join Tenable’s Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.


