- I recommend the Pixel 9 to most people looking to upgrade - especially while it's $250 off
- Google's viral research assistant just got its own app - here's how it can help you
- Sony will give you a free 55-inch 4K TV right now - but this is the last day to qualify
- I've used virtually every Linux distro, but this one has a fresh perspective
- The 7 gadgets I never travel without (and why they make such a big difference)
How to manage the security challenges triggered by remote work
Remote employees have engaged in certain risky behaviors, such as storing sensitive data, using inappropriate admin access and failing to update software, says Tanium.
Image: iStock/simpson33
The coronavirus pandemic forced organizations to quickly and unexpectedly shift employees to a remote working environment. Though many IT teams have handled the transition as effectively as possible, such an abrupt change has still opened the door for increased security risks. A report released Monday by security provider Tanium examines some of the threats facing organizations with a remote work scenario and offers tips on how to manage them.
SEE: COVID-19 workplace policy (TechRepublic Premium)
Entitled “IT Leads the Way: How the Pandemic Empowered IT,” the new report is based on a survey of IT decision makers across 500 different enterprise companies. Conducted by research firm PSB Insights on behalf of Tanium, the survey elicited responses from a variety of sectors in the U.S. and the U.K., with more than half of the respondents C-level decision-makers.
In early 2020, 88% of those surveyed expressed some level of confidence in their ability to fully and securely support a remote workforce. Yet after the pandemic hit, 61% of the respondents admitted that they had difficulty switching to a work-from-home environment. As a result, 73% said they now face new IT security challenges, while 52% acknowledged that their security challenges have become more complex.
Most of the challenges stem from having to handle security matters in a perimeter-less environment. In the past, the company firewall used to be one of the major barriers between employees and external threats. But now with so many employees operating outside the firewall, each endpoint that connects to the network must be managed differently.
“Our distributed workforce means the end of the network perimeter as we know it and the rise of the endpoint,” Tanium Global CISO Chris Hodson said in a press release. “But managing and securing endpoints requires visibility and control. You can’t secure what you can’t see. As the research reveals, it is critical that IT teams continue to invest in solutions that break down data silos and enable automation to ensure manageability, security and insight for their endpoints.”
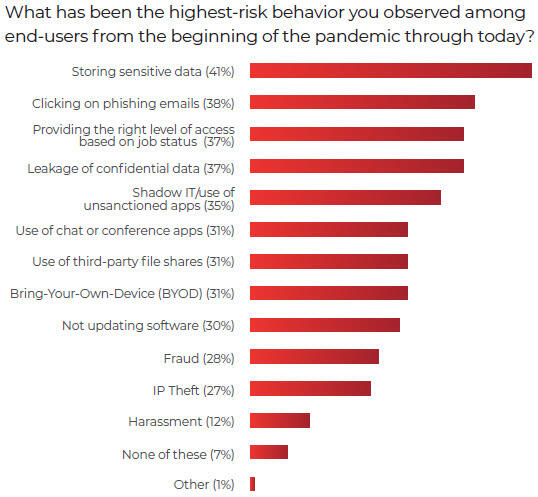
Among the types of risky behavior observed by respondents from remote workers, storing sensitive data was at the top of the list, cited by 41%. Clicking on phishing emails was listed by 38% of those surveyed, inappropriate administrator access by 37%, leaking confidential data by 37% and using shadow IT or unapproved apps by 35%. Other risky behaviors include the use of chat or conference apps, the use of third-party file sharing sites, the use of personal devices, and the failure to update software.
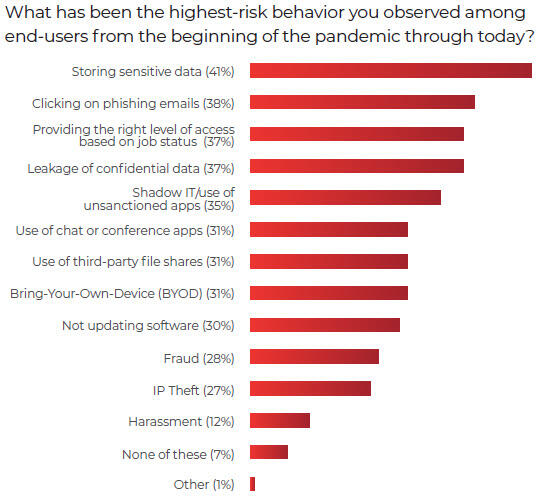
Image: Tanium
To help organizations better manage the challenges amid the new remote work environment, Tanium offers the following suggestions:
Expect the rapid pace of digital transformation to continue. Businesses have discovered they can move quickly. Opportunities await those businesses that maintain this pace, building on success they achieved in 2020.
Remote is the new normal, so focus on endpoints, not firewalls and on mobile users, not the office. The future is perimeter-less. The last shims holding traditional network perimeters in place have been discarded in last year’s WFH scramble. Plan for a Zero Trust future with endpoints, as well as applications or data needed for work from anywhere. Security, monitoring and control need to be available on any endpoint over any internet connection. You can’t count on VPN access for security. Employees must be able to work with whatever software they need, wherever it resides—locally, in an internal data center or in a public or private cloud. Manage users and endpoints, and you’re ready for employees to work flexibly and safely.
Prioritize investments that deliver visibility and control for end users as well as IT. Agility comes from three things: Readily available information about what can be done and how to do it, proven processes for executing decisions and teams primed for acting on the latest information and delivering results quickly and reliably. For IT security and operations, agility requires improved visibility into endpoints, networks and threats. IT platforms must help IT engineers act quickly. IT teams need a unifying platform to allow the organization to break down silos and work productively and securely.


