- I recommend the Pixel 9 to most people looking to upgrade - especially while it's $250 off
- Google's viral research assistant just got its own app - here's how it can help you
- Sony will give you a free 55-inch 4K TV right now - but this is the last day to qualify
- I've used virtually every Linux distro, but this one has a fresh perspective
- The 7 gadgets I never travel without (and why they make such a big difference)
How your personal data may be exposed by misconfigured mobile apps

App developers are failing to properly set up and secure access to third-party services, putting user data at risk, says Check Point Research.
Image: Check Point
That mobile app you’ve been using could be exposing your personal data to the wrong people, not because of the way the app is designed but because of the way it taps into third-party services. As described in a report released on Thursday, cyber threat intelligence firm Check Point Research said it found that poorly configured access to third-party services in mobile apps can expose usernames, email address and even passwords to malicious actors.
SEE: Top Android security tips (free PDF) (TechRepublic)
The challenge is that today’s mobile apps increasingly rely on third-party data and services. Many apps access cloud-based storage, online databases, analytics and other external content as part of their normal operation. And though developers may be diligent about their own code, they might overlook the right security and configuration needed for third-party services.
In its report, Check Point said that it discovered over the past few months many app developers putting user data at risk by not following best practices for integrating third-party services. And the problem isn’t just limited to user data. In many cases, the data and internal resources of the developers were also placed at risk.
Though the firm’s research team focused on Android apps in Google Play, Check Point mobile research manager Aviran Hazum said the company found iOS apps also at risk. The issue is centered around the development of an app and is unrelated to the operating system on the device.
Looking at Google Play apps that access publicly available databases in real time, Check Point said it uncovered the exposure of certain sensitive data such as email addresses, passwords, private chats, device location and user identifiers. Any hacker who gains access to such data could commit fraud or identity theft.
“Mobile application developers often make use of cloud-hosted databases and data storage, such as AWS S3, to store content for mobile clients,” said Salt Security technical evangelist Michael Isbitski. “Such cloud services provide essentially unlimited storage that is accessible from anywhere, and that is perfect for the world of mobile connectivity. For the Android apps Check Point investigated, they uncovered data stored in the cloud that did not require authentication and was accessible to anyone.”
SEE: Hiring kit: Android developer (TechRepublic Premium)
To illustrate its claims, Check Point cited some specific apps on Google Play where the researchers were able to access personal user data.
An astrology and horoscope app called Astro Guru with more than 10 million downloads prompted users to enter their names, dates of birth, genders, locations, email addresses and payment details. Much of that information was exposed as Check Point was able to find it via an accessible online database. On the plus side, Hazum said Check Point sent its findings to the developers of Astro Guru, who then fixed the issue.
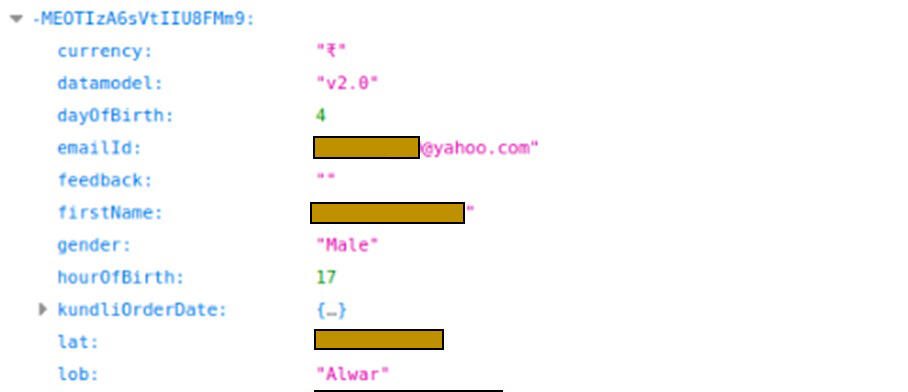
Location, email address and personal file shared on Astro Guru.
Image: Check Point
A tax app called T’Leva with more than 50,000 installs asked users to provide certain personal information. All of it was captured in a real-time database, allowing Check Point to access chat messages between drivers and passengers and retrieve full names, phone numbers and locations of the users.
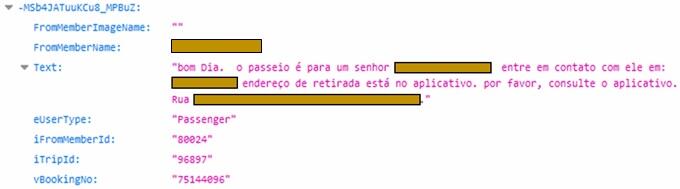
A private chat between a taxi driver and passenger on T’Leva.
Image: Check Point
An app named Screen Recorder records the device’s screen and stores those recordings on a cloud-based service. The flaw here is that the developers were embedding the secret access keys to the service, paving the way for Check Point to recover those keys and gain access to each recording.
Another app called iFax with 50,000 users embedded the cloud access keys and also stored all fax transmissions. After analyzing the app, Check Point said it found that a hacker could access all the faxed documents sent by the users.
“For some of the Android apps that Check Point examined, developers were embedding connection keys for backend cloud storage directly into the mobile application code,” Isbitski said. “It’s a bad practice to hardcode and store static access keys into an app, which the app in turn uses to connect to an organization’s own backend APIs and third-party, [cloud-based] APIs. Compiled code within mobile app binaries is much more readable than many developers realize. Decompilers and disassemblers are plentiful, and such connection keys are easily harvested by attackers.”
Many developers realize that storing cloud access keys in their app is a bad practice, according to Check Point. But in some cases, the developers tried to “cover up” the problem with coding tricks that didn’t actually fix it.
Even when coding an app using best practices, security issues can creep in. To help developers look for such issues, Check Point advises them to use a Mobile App Reputation Service during the development process. Available from different security vendors, this type of service scans and ranks the security and privacy of a mobile app.
Isbitski offered additional recommendations.
“If you opt to use cloud storage as a developer, you need to ensure any key material necessary to connect to such storage is kept secure, and you must also leverage the cloud provider’s access control and encryption mechanisms to keep the data protected,” Isbitski said. “Mobile app developers should make use of the Android Keystore and Keychain mechanisms that are backed by the hardware security module of the mobile device. Developers should also make use of the Android encryption mechanisms when storing other sensitive data client-side.”
Mobile app users, however, face a tougher time protecting themselves, according to Hazum. Even a mobile security product capable of checking an app’s infrastructure components won’t prevent data from being uploaded and exposed or else the app wouldn’t work properly.
Hazum said that Check Point contacted Google to report its findings but received no reply. The firm also contacted several app developers, but the creators behind Astro Guru were the only ones to respond.


