- Why I recommend this OnePlus phone over the S25 Ultra - especially at this new low price
- I replaced my laptop with Microsoft's 12-inch Surface Pro for weeks - here's my buying advice now
- This palm recognition smart lock doubles as a video doorbell (and has no monthly fees)
- Samsung is giving these Galaxy phones a big One UI upgrade - here's which models qualify
- 7 MagSafe accessories that I recommend every iPhone user should have
Invoice Phishing Alert: TA866 Deploys WasabiSeed & Screenshotter Malware

The threat actor tracked as TA866 has resurfaced after a nine-month hiatus with a new large-volume phishing campaign to deliver known malware families such as WasabiSeed and Screenshotter.
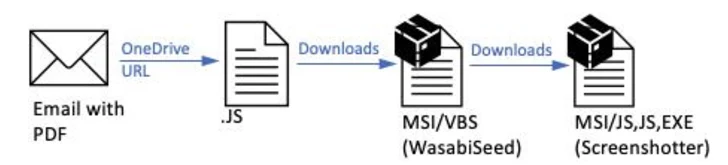
The campaign, observed earlier this month and blocked by Proofpoint on January 11, 2024, involved sending thousands of invoice-themed emails targeting North America bearing decoy PDF files.
“The PDFs contained OneDrive URLs that, if clicked, initiated a multi-step infection chain eventually leading to the malware payload, a variant of the WasabiSeed and Screenshotter custom toolset,” the enterprise security firm said.
TA866 was first documented by the company in February 2023, attributing it to a campaign named Screentime that distributed WasabiSeed, a Visual Basic script dropper that’s used to download Screenshotter, which is capable of taking screenshots of the victim’s desktop at regular intervals of time and exfiltrating that data to an actor-controlled domain.
There is evidence to suggest that the organized actor may be financially motivated owing to the fact that Screenshotter acts as a recon tool to identify high-value targets for post-exploitation, and deploy an AutoHotKey (AHK)-based bot to ultimately drop the Rhadamanthys information stealer.
Subsequent findings from Slovak cybersecurity firm ESET in June 2023 unearthed overlaps between Screentime and another intrusion set dubbed Asylum Ambuscade, a crimeware group active since at least 2020 that also engages in cyber espionage operations.
The latest attack chain remains virtually unchanged save for the switch from macro-enabled Publisher attachments to PDFs bearing a rogue OneDrive link, with the campaign relying on a spam service provided by TA571 to distribute the booby-trapped PDFs.
“TA571 is a spam distributor, and this actor sends high volume spam email campaigns to deliver and install a variety of malware for their cybercriminal customers,” Proofpoint researcher Axel F said.
This includes AsyncRAT, NetSupport RAT, IcedID, PikaBot, QakBot (aka Qbot), and DarkGate, the last of which allows attackers to perform various commands such as information theft, cryptocurrency mining, and execution of arbitrary programs.
Splunk, which detected multiple campaigns deploying a loader designed to initiate DarkGate on compromised endpoints, said malicious PDF files act as a carrier for an MSI installer that executes a cabinet (CAB) archive to trigger the execution of DarkGate via AutoIT loader script.
“DarkGate first appeared in 2017 and is sold only to a small number of attack groups in the form of Malware-as-a-Service through underground forums,” South Korean cybersecurity company S2W said in an analysis of the malware this week.
“DarkGate continues to update it by adding features and fixing bugs based on analysis results from security researchers and vendors,” highlighting continued efforts made by adversaries to implement anti-analysis techniques to bypass detection.
News of TA866’s resurgence comes as Cofense revealed that shipping-related phishing emails primarily single out the manufacturing sector to propagate malware like Agent Tesla and Formbook.
“Shipping-themed emails increase during the holiday seasons, albeit only slightly,” Cofense security researcher Nathaniel Raymond said.
“For the most part, the yearly trends suggest that these emails follow a particular trend throughout the year with varying degrees of volumes, with the most significant volumes being in June, October, and November.”
The development also follows the discovery of a novel evasion tactic that leverages the caching mechanism of security products to get around them by incorporating a Call To Action (CTA) URL that points to a trusted website in the phishing message sent to the targeted individual.
“Their strategy involves caching a seemingly benign version of the attack vector and subsequently altering it to deliver a malicious payload,” Trellix said, stating such attacks have disproportionately targeted financial services, manufacturing, retail, and insurance verticals in Italy, the U.S., France, Australia, and India.
When such a URL gets scanned by the security engine, it’s marked as safe, and the verdict is stored in its cache for a set time. This also means that if the URL is encountered again within that time period, the URL is not reprocessed, and instead, the cached result is served.
Trellix pointed out that attackers are taking advantage of this quirk by waiting until the security vendors process the CTA URL and cache their verdict, and then altering the link to redirect to the intended phishing page.
“With the verdict being benign, the email smoothly lands in the victim’s inbox,” security researchers Sushant Kumar Arya, Daksh Kapur, and Rohan Shah said. “Now, should the unsuspecting recipient decide to open the email and click on the link/button within the CTA URL, they would be redirected to the malicious page.”