- Why I recommend this OnePlus phone over the S25 Ultra - especially at this new low price
- I replaced my laptop with Microsoft's 12-inch Surface Pro for weeks - here's my buying advice now
- This palm recognition smart lock doubles as a video doorbell (and has no monthly fees)
- Samsung is giving these Galaxy phones a big One UI upgrade - here's which models qualify
- 7 MagSafe accessories that I recommend every iPhone user should have
Iranian state actor ‘Marcy’ used Facebook to spy on US military personnel
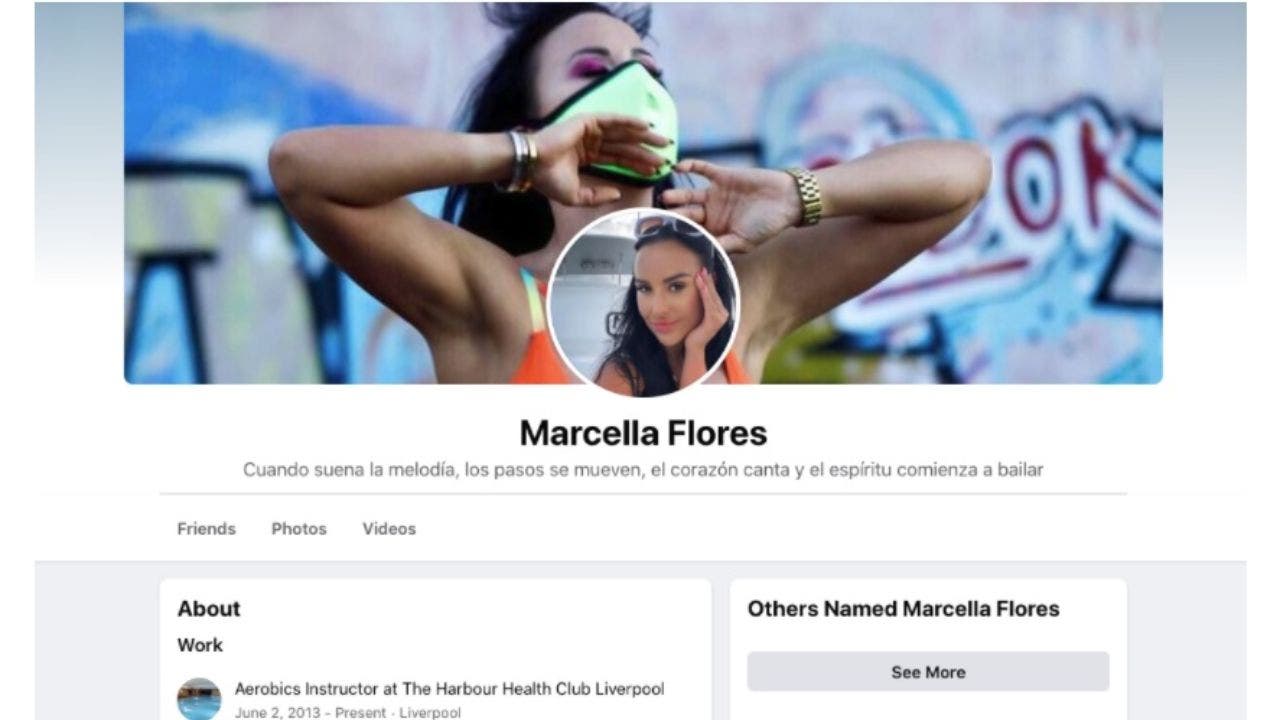
An Iranian state actor spent years pretending to be someone called “Marcella Flores” in an attempt to spy on a U.S. aerospace defense contractor.
A new report from cybersecurity company Proofpoint identified the actor as part of state-sponsored espionage against defense “industrial base” contractors doing work related to the Middle East.
Identified as TA456, the state actor first established a relationship with an employee at a subsidiary of the defense contractor. Then, in early June 2021, attempted to “capitalize on this relationship” by sending the employee malware as part of an “ongoing email communication chain,” according to Proofpoint.
An Iranian state actor spent years pretending to be someone called “Marcella Flores” in an attempt to spy on a U.S. aerospace defense contractor. (Proofpoint)
TA456 is also associated with espionage activity known as both Tortoiseshell and Imperial Kitten.
Over a period of at least eight months, TA456, going by the name of Marcy or Marcella, sent “benign email messages, photographs, and a video to establish her veracity and build rapport…At one time, TA456 attempted to send a benign, but flirtatious video via a OneDrive URL,” the report said.
IRAN’S KHAMENEI ACCUSES US OF BEING ‘MALICIOUS’ IN NUCLEAR TALKS
The objective was to infect the employee’s machine with malware dubbed LEMPO to perform reconnaissance and steal sensitive information, Proofpoint said. Once the malware is active, it saves the reconnaissance details to the host, sends sensitive information to a state actor-controlled email account, and then deletes files to cover its tracks, the report said.
Marcella gets friendly on Facebook
In addition to a Gmail account, Marcella maintained a now-suspended Facebook profile, the report said.
A Facebook profile photo was uploaded on May 30, 2018 and Marcella began interacting with the employee on social media in late 2019.
The profile is very similar to fictitious profiles previously used by Iranian state actors, the report said.
“The ‘Marcella’ profile appeared to be friends with multiple individuals who publicly identify as defense contractor employees and who are geographically dispersed from ‘Marcella’s’ alleged location in Liverpool, UK,” the report said.
CLICK HERE TO GET THE FOX NEWS APP
“While targeting defense contractors is not new for TA456, this campaign uniquely establishes the group as one of the most determined Iranian-aligned threat actors tracked by Proofpoint,” the report said, adding that targeting U.S. defense contractors connected to contracts in the Middle East “is consistent with historical Iranian cyber activity.”
Facebook addressed the broader campaign in a post earlier this month.
“In an apparent expansion of malicious activity to other regions and industries, our investigation found them targeting military personnel and companies in the defense and aerospace industries primarily in the U.S., and to a lesser extent in the UK and Europe,” the company said in a statement. “This group used various malicious tactics to identify its targets and infect their devices with malware to enable espionage.”

