- Apple Intelligence hasn't lived up to my expectations, but these 3 upgrades could win me back
- Samsung launches One UI 8 beta - what's new and how to join
- I invested in a subscription-less smart ring, and it beat my Oura in several ways
- HPE Aruba unveils raft of new switches for data center, campus modernization
- I tested the $17 multitool that everyone's buying on Amazon - here's my verdict after a week
Iranian state-aligned threat actor targets new victims in cyberespionage and kinetic campaigns
TA435 is now employing more aggressive tactics, including the use of real email accounts, malware and confrontational lures to gain access to key accounts. The threat actor targets high-profile and high-security accounts for cyberespionage purposes.
Jump to:
Who is TA453?
TA453 is a state-sponsored Iranian cyberespionage threat actor. TA453 has been known for almost always targeting academics, researchers, diplomats, dissidents, journalists and human right workers, all with expertise in the Middle-East, according to Proofpoint.
TA453 overlaps with cyberespionage groups Charming Kitten, Phosphorus and APT42.
Their favorite method to approach and attack their targets consists of using web beacons in emails before eventually attempting to harvest the target’s credentials. They also leverage multi-persona impersonation, which is a social engineering trick using two impersonated accounts controlled by the attackers to talk in a single email thread with the victim. The multiple personas attempt to convince the target of the legitimacy of the operation.
Proofpoint currently tracks six subgroups of TA453, which are classified by victimology, infrastructure and tactics, techniques and procedures.
The researchers assess that TA453 generally operates for the Iranian Islamic Revolutionary Guard Corps, Intelligence Operation, as based on research from PwC and the Justice Department in a 2018 indictment in addition to an analysis of TA453 targeting compared to reported IRGC-IO activities.
“The more aggressive activity could represent collaboration with another branch of the Iranian state, including the IRGC Quds Force,” Proofpoint said.
A shift in TA453’s methods
Email accounts used to reach the targets
The use of email accounts created by the attacker is sometimes dropped by threat actors in favor of using real compromised accounts. This has the effect of making their content look more legitimate, as it comes from a known email address rather than an unknown one.
SEE: Password breach: Why pop culture and passwords don’t mix (free PDF) (TechRepublic)
This method is used by a subgroup of the TA453 threat actor and combined with the use of unusual URL shorteners like bnt2[.]live or nco2[.]live. Proofpoint indicates that in 2021, a U.S. press secretary was reached by TA453 using the email address of a local reporter.
Use of malware
The GhostEcho malware, a lightweight PowerShell backdoor under development that’s able to execute additional modules and communicate with an attacker-controlled C2 server, was used to target a variety of diplomatic missions across Tehran in 2021 to target women’s rights advocates in the country. The payload was not available to the researchers when discovered.
Confrontational lures
Samantha Wolf is a persona created by TA453 used in confrontational social engineering lures. The goal is to raise the target’s fear and uncertainty so that they respond to the emails sent by the attackers.
Samantha Wolf used general complaints and car accidents amongst other themes, targeting U.S. and European politicians and governmental entities (Figure A).
Figure A
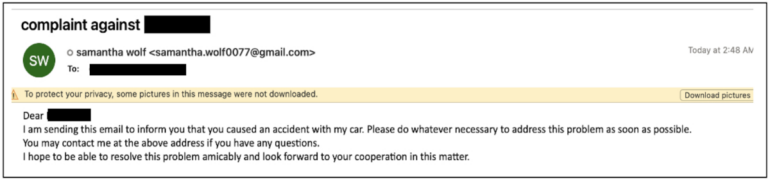
Documents sent by Samantha Wolf contained remote template injection to download malicious files, resulting in a GhostEcho infection. The method used by the attackers consisted of replacing the user’s previous default Microsoft Word template.
Even more aggressive activity
In May 2022, Proofpoint discovered an attack targeting a high-ranking military official with multiple compromised email accounts. The targeted individual was a former member of the Israeli military. As mentioned earlier, the use of multiple compromised email accounts for such an attack is unusual for TA453.
The aggressive message was written in Hebrew (Figure B) and used the first name of the person in the filename.
Figure B

The text roughly translates: “I’m sure you remember when I told you every email you get from your friends may be me and not the person it claims to be. We follow you like your shadow — in Tel Aviv, in [redacted university], in Dubai, in Bahrain. Take care of yourself.”
According to Proofpoint, this intimidation tactic also indicates a collaboration between TA453 and hostile Iranian state-aligned operations.
An overlap in the infrastructure linking this case and another one also adds legitimacy to the research’s conclusion. In May 2022, an Israeli researcher received an email coming from a spoofed email address of a reputed academic to invite the target to a conference in order to kidnap them.
TA453s outlier operations have shown a constant state of evolution in its TTP, with possible support for hostile or even kinetic operations.
TA435’s previously known modus operandi
TA453 generally approaches its targets with email accounts they create and begins establishing contact with their targets through benign conversation, although some of its subgroups may directly hit the target with a credential harvesting link. No matter the length of the exchange, the goal is always to get access to the email of the target via a phishing link.
SEE: Mobile device security policy (TechRepublic Premium)
This technique suggests that the attacker’s main interest resides in reading the email content of the target, rather than trying to infect their computer with malware to get access to files and folders. This is also stealthier, as it does not generally raise alarms from security productions — the phishing pages hosted on the infrastructure are never widely spread and therefore hardly reported.
How to protect yourself from this threat
Users need to be careful when opening email content, even when it comes from a verified and trusted email address, which might be compromised.
The content of the email should raise alarm for the reader: Watch out for forms not previously used by the writer, spelling mistakes, changes in language or diction, and other indications that the email is fake. When in doubt, users should verify the legitimacy of the email by reaching out to the sender via another channel.
Users should also always double-check invitations to conferences and reach out directly to the organizers through their official website. Users should never click on any suspicious links. Instead, report the link to the IT department or CERT/SOC teams for investigation, as it may be a phishing attempt.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.

