- 바이두, AI 개발 박차··· ‘어니 터보’ 모델로 글로벌 추격 본격화
- 7 Linux distros you should avoid until you've mastered the command line
- 5 ways to use the Linux terminal on your Android phone - including my favorite
- A few secretive AI companies could crush free society, researchers warn
- Key Cybersecurity Considerations for 2025
Lookout Discovers New Spyware Deployed by Russia and China

Three new mobile-only surveillance tools developed and used by state-sponsored organizations have been discovered by mobile security provider Lookout.
These new tools include BoneSpy and PlainGnome which are Android surveillance tools developed by Gamaredon (aka Primitive Bear, Shuckworm), an advanced persistent threat (APT) group associated with the Russian Federal Security Service (FSB).
Additionally, a Chinese software development company has created EagleMsgSpy, a lawful surveillance tool used by many government agencies in mainland China to collect extensive information from mobile devices.
Kyle Schmittle and Alemdar Islamoglu, both Senior Security Intelligence Researchers at Lookout, presented their findings at Black Hat Europe in London on December 11.
Russia’s BoneSpy and PlainGnome, Mobile Spyware Implants
Spyware Overview
BoneSpy and PlainGnome are the first known mobile families to be attributed to Gamaredon, an ATP group known for its cyber espionage campaigns targeting desktop devices, that the Security Service of Ukraine (SSU) attributed to the FSB in 2021.
BoneSpy has been in use since at least 2021 and is derived from the Russian open-source DroidWatcher, a surveillance app developed between 2013 and 2014.
PlainGnome first appeared in 2024 but shares similar theming and command-and-control (C2) server properties with BoneSpy.
Both families are still active and primarily used to target Russian-speaking individuals in former Soviet countries, such as Uzbekistan, Kazakhstan, Tajikistan and Kyrgyzstan.
“While Gamaredon has historically targeted Ukraine, the targeting of Central Asian countries like Uzbekistan likely resulted from worsening relations between these countries and Russia since the start of the Russian invasion of Ukraine in 2022,” the two researchers and their colleague Kristina Balaam wrote in a report published on December 11.
Spyware Features
Both spyware tools have broad surveillance capabilities, including:
- Attempting to gain root access to the device
- Anti-analysis checks
- Location tracking
- Getting information about the device
- Getting sensitive user data such as SMS messages, ambient audio and call recordings, notifications, browser history, contacts, call logs, photos from the camera, screenshots and cell service provider information
PlainGnome acts as a dropper for a surveillance payload, stored within the dropper package, while BoneSpy is deployed as a standalone application.
Before discovering BoneSpy and PlainGnome, Lookout’s Schmittle said that his team was only aware of two Russian-made spyware families. First, Monokle, developed by St. Petersburg-based company Special Technology Center (STC) in 2019 and likely used by Turla. The other is Infamous Chisel, used by Sandworm against Ukraine military entities since at least 2023.
Read more on Turla: Palo Alto Reveals New Features in Russian APT Turla’s Kazuar Backdoor
China’s EagleMsgSpy, A Lawful Surveillance Tool
Spyware Overview
EagleMsgSpy is a lawful surveillance tool that has been operating since at least 2017 and is used by several Chinese public security bureaus to collect extensive information from mobile devices in Mainland China.
The Lookout researchers assessed that EagleMsgSpy is primarily used to target what is sometimes called the ‘Five Poison’ communities:
- Practitioners of Falun Gong
- Uyghurs
- Tibetans
- Taiwanese people
- Hong Kong pro-democracy advocates
Lookout also identified two IP addresses associated with EagleMsgSpy, which have previously been linked to other China-based surveillance tools, including CarbonSteal, known for its role in past campaigns targeting the Tibetan and Uyghur communities.
Made in China, By the Private Sector
While the tool’s origin remains uncertain, the IP address of one of the C2 servers encountered during Lookout’s investigation had previously been pointed to by several subdomains associated with a private Chinese technology company, Wuhan Chinasoft Token Information Technology Co., Ltd.
“The root domain, tzsafe[.]com, was encountered in promotional materials found during an open source intelligence (OSINT) investigation into this Wuhan-based technology company,” said another Lookout report published on December 11.
Additionally, the EagleMsgSpy admin user manual includes a screenshot displaying locations of what Lookout believes to be test devices that show two sets of coordinates located approximately 1.5 km from the registered official business address of Wuhan Chinasoft Token Information Technology Co., Ltd.
This led Lookout to assess with “high confidence” that EagleMsgSpy has been developed by Wuhan Chinasoft Token Information Technology.
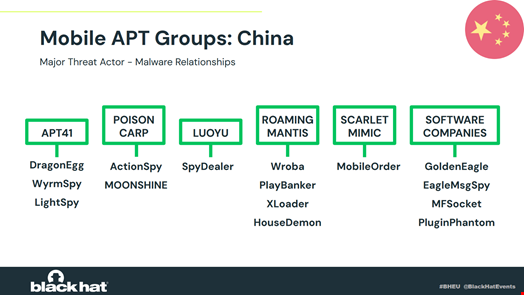
EagleMsgSpy has been identified by Lookout as one of at least four different surveillance tools used by the state, which were made by the private sector, with GoldenEagle, MFSocket and PluginPhantom.
Many other tools originate from state-affiliated APT groups, such as APT41, PoisonCarp, or Roaming Mantis.
Spyware Features
The spyware is placed on victims’ Android devices and configured through access to the unlocked victim device. Once installed, the headless payload runs in the background, hiding its activities from the device user and collecting extensive data.
The surveillance payload collects an extensive amount of data about the victim device including, but not limited to, screenshots, call logs, SMS messages and GPS coordinates.
Audio recordings of the device while in use are also gathered.
It also collects all messages from QQ, Telegram, Viber, WhatsApp and WeChat.
After data is collected, it is stored in a staging area in a hidden directory of the device’s file system for eventual exfiltration. The data files are then compressed and password-protected before being sent to the C2 server.
While EagleMsgSpy only targets Android devices at present, internal documents retrieved from open directories on the attacker’s infrastructure suggest the presence of an undiscovered iOS component.

