- The Significance of Cybersecurity within AI Governance
- The Evolution of SOC: Harnessing Data, AI and Automation
- How to disable ACR on your TV (and stop companies from spying on you)
- I expected this cheap multitool to be a waste of money, but it's my new a toolbox essential
- Have The Last Word Against Ransomware with Immutable Backup
Malware is proliferating, but defenses are stronger: Mandiant

Threat groups are on the rise, and Google Cloud’s cyberdefense unit Mandiant is tracking 3,500 of them, with 900 added last year, including 265 first identified during Mandiant’s investigations in 2022.
Mandiant’s M-Trends 2023 report on the global cybersecurity landscape found organizations faced intrusions by advanced groups including government-sponsored entities from China and Russia, financially motivated threat groups and 335 uncategorized threat groups.
The largest proportion of groups — nearly half of those followed by Mandian — sought financial gain, according to the report.
Jump to:
‘Dwell time’ plummets worldwide
Dwell time, the number of days an adversary lurks in a target network before detection, dropped last year. According to the M-Trends report, the global median dwell time was 16 days, the shortest such time for all reporting periods since the M-Trends report launched 14 years ago, and down from 21 days in 2021.
External notifications of incidents rise
The firm noted an increase in proactive notification efforts by security partners. The report said organizations in the Americas were notified by an external entity in 55% of incidents, compared to 40% of incidents in 2021, the highest percentage of external notifications the Americas have seen over the past six years.
Organizations in Europe, the Middle East and Africa (EMEA) were alerted of an intrusion by an external entity in 74% of investigations in 2022 compared to 62% in 2021. In the Asia Pacific region, organizations were alerted by external partners in 33% of investigations.
The study, based on Mandiant Consulting investigations of targeted attack activity between Jan. 1 and Dec. 31, 2022, found an increasing number of new malware families.
Ransomware attacks drop
The report confirms earlier research by TechRepublic noting drops in ransomware attacks: In 2022, 18% of Mandiant’s global investigations involved ransomware compared to 23% in 2021. This represents the smallest percentage of Mandiant investigations related to ransomware prior to 2020, according to the company.
“While we don’t have data that suggests there is a single cause for the slight drop in ransomware-related attacks that we observed, there have been multiple shifts in the operating environment that have likely contributed to these lower figures,” said Sandra Joyce, VP, Mandiant Intelligence at Google Cloud, in a statement.
She said disruption of ransomware attacks by government and law enforcement forced actors to retool or develop new partnerships.
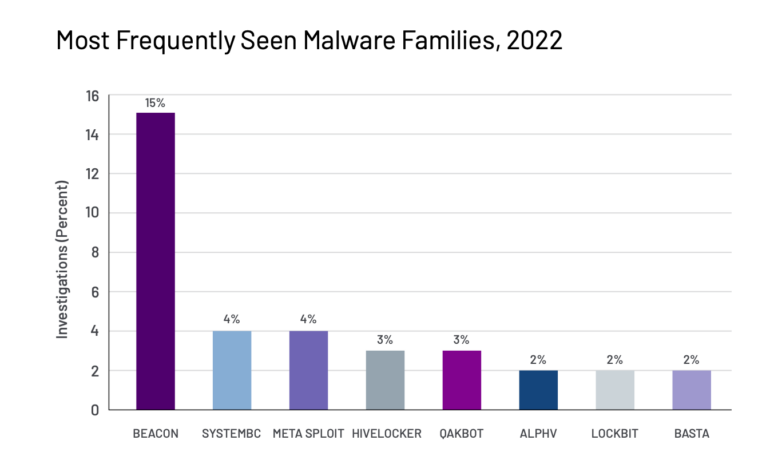
BEACON prevails among malware strains
The most common malware family identified by Mandiant in investigations last year was BEACON, identified in 15% of all intrusions investigated by Mandiant, which said the malware has been deployed by groups aligned with China, Russia and Iran; financial threat groups; and over 700 UNCs. Others were SystemBC, Metasploit, Hivelocker, Qakbot, Alphv, LockBit and Basta (Figure A).
Figure A
The report said that of the 588 new malware families Mandiant tracked last year:
- Thirty-four percent were backdoors.
- Fourteen percent were downloaders.
- Eleven percent were droppers.
- Seven percent were ransomware.
- Five percent were launchers (Figure B).
Figure B

“Mandiant has investigated several intrusions carried out by newer adversaries that are becoming increasingly savvy and effective,” said Charles Carmakal, CTO Mandiant Consulting at Google Cloud, adding that the actors use data from underground cybercrime markets to run social engineering campaigns aimed at moving laterally into enterprise networks.
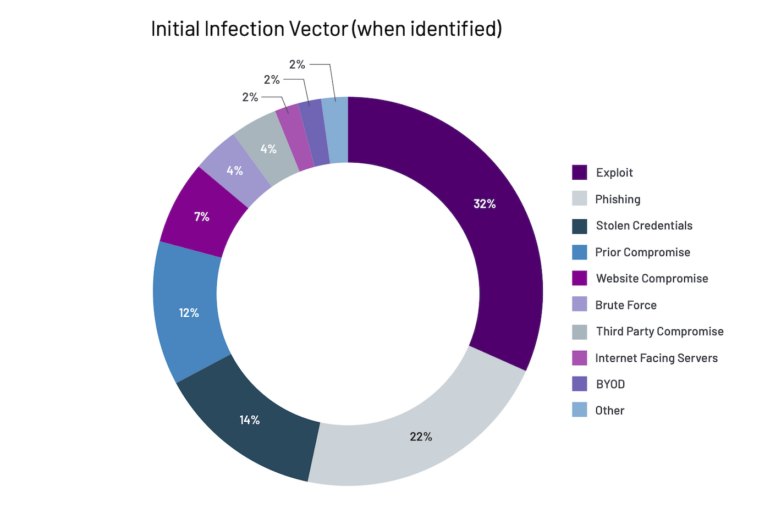
Software exploits lead attack vectors
According to the Mandiant report, for the third year in a row, exploits, such as SQL injection or cross-site scripting were the most common attack vector, used by 32% of attackers, down from 37% such intrusions in 2021. Phishing at second place, represented 22% of intrusions compared to 12% in 2021.
Mandiant reported that in its investigations it saw evidence that in attacks involving at least one exploit against a vulnerability, they were successful in 36% of investigations in 2022 compared to 30% of investigations from 2021. It also reports that perimeter devices exposed to the wild of the internet such as firewalls, virtualization solutions and Virtual Private Network devices are desirable targets for attackers.
Notable vulnerabilities were Log4j1, which represented 16% of investigations, while the second and third most notable vulnerabilities identified were related to F5 Big-IP2 and VMware Workspace ONE Access and Identity Manager.
Poor digital hygiene fuels credential theft
Mandiant also reported an increase in credential theft and purchasing last year, with an increase in incidents in which credentials were stolen outside of the organization’s environment and then used against the organization, potentially due to reused passwords or use of personal accounts on corporate devices.
Threat actors used stolen credentials in 14% of attacks last year versus 9% in 2021 in investigations where the initial infection vector was identified.
The firm also reported that 40% of intrusions in 2022 involved data exfiltration, an increase in the use of the technique from recent years.
Mandiant investigations uncovered an increased prevalence in both the use of widespread information stealer malware and credential purchasing in 2022 when compared to previous years. In many cases, investigations identified that credentials were likely stolen outside of the organization’s environment and then used against the organization, potentially due to reused passwords or use of personal accounts on corporate devices (Figure C).
Figure C
Phishing is 2nd most common vector
Last year, phishing represented 22% of intrusions where the initial infection vector was identified making it the second most utilized vector, and an increase from 12% of intrusions in 2021.
Microsoft most attacked
Windows malware was by far the most common newly tracked and observed exploit, with 92% of newly identified malware families and 93% of observed malware able to run on Windows, according to the report. Other findings follow:
- Malware families effective on one or more operating systems were more prevalent than malware designed to focus on only one operating system.
- Malware effective on only one operating system was most likely to target Windows OS.
- Malware effective on Linux decreased from 18% in 2021 to 15%
- Malware designed to exploit the VMWare created operating system VMkernel was reported for the first time.
On the last item, Mandiant noted that while the volume is small, defenders should pay attention because VMWare is widely used.
“These types of operating systems don’t have significant capability for Endpoint Detection and Response tool monitoring. As a result, monitoring and investigations into the platform can be challenging for defenders,” noted the report.
New cybercriminals use common methods to great effect
Among groups targeting major corporations with high-profile attacks were Lapsus, which Mandiant tracks as UNC3661, and another Mandiant labeled UNC3944. Both uncharacterized groups, or UNCs, are noteworthy because, while lacking in the sophistication of nation-aligned actors, they were nonetheless highly effective.
“These incidents underscored the threat posed to organizations by persistent adversaries willing to eschew the unspoken rules of engagement,” said Mandiant, which noted that the actors used data garnered from underground cybercrime markets, clever social engineering schemes and even bribes. They also had no qualms about bullying and threatening their targets, according to the firm.
UNC3661 started with South American targets, then went global, apparently bent on damaging reputations by stealing source code and intellectual property.
“Their actions during intrusions spoke broadly to a desire for notoriety, rather than being optimized to increase profits,” the firm said, adding that the group, after demanding IP as source code, would conduct polls in Telegram chats to determine which organization to target next.
SEE: Telegram popular bazaar for dark web threat ecosystem
Mandiant reported that, unlike Lapsus, UNC3944, which appeared last May, is a financially motivated threat cluster that gains access using stolen credentials obtained from SMS phishing operations.
Of note: Neither group relies on zero-day vulnerabilities, custom malware, or new tools. “It is important organizations understand the potential ramifications of this new, more outspoken threat and adjust both protections and expectations accordingly,” said the report.

