- Former CISA and NCSC Heads Warn Against Glamorizing Threat Actor Names
- Some apps are battery vampires - how to root them out and shut them down
- Your Android phone just got a major feature upgrade for free - including these Pixel models
- I found a Linux distro that combines the best parts of other operating systems (and it works)
- Why I'm leaving Firefox for good - here's the browser I'm using now instead
Microsoft Defender for Cloud Gets More Multicloud

Almost 90% of enterprises use more than one public cloud provider, according to Flexera’s 2023 State of the Cloud survey. For enterprise cloud users, managing their multicloud workloads is the second biggest challenge after managing cloud costs. Microsoft Defender for Cloud aims to help with that.
Businesses can already use Microsoft Defender for Cloud to monitor security settings on AWS and Google Cloud Platform as well as Azure. Beginning August 15, 2023, businesses will also be able to identify security risks and attack paths, scan for secrets and discover sensitive data stored in Google Cloud. These cloud security posture management features were previously only available for AWS and Azure and now will apply to all three main clouds. Microsoft Defender for Cloud can even turn on best practices from several key standards for AWS, Azure and now GCP automatically.
Jump to:
Get a baseline using the Microsoft cloud security benchmark
“A lot of our customers are not single cloud – it’s really rare,” Microsoft VP of strategy for SIEM and XDR Raviv Tamir told TechRepublic. “Most customers go multicloud because they want to divide the risk. But then the problem is applying policy across (those clouds) in a consistent way.”
To help with that, Microsoft turned its Azure Security Benchmark into a cross-platform tool, renaming it the Microsoft cloud security benchmark. The MCSB combines relevant recommendations from the Center for Internet Security, the National Institute of Standards and Technology and the Payment Card Industry Data Security Standard or PCI-DSS, Tamir explained.
“It’s a baseline that tries to align across these three standards and take all the technical parts of it and then tell you sort of: How do you measure up vs Azure, and how do you measure up vs AWS? With the new GCP connector, we can align that also to GCP so you can get all your three hyperscale clouds in one go.”
While GCP benchmark coverage is in public preview, you can add your GCP environment to Microsoft Defender for Cloud and get free resource monitoring with those best practices automatically enabled.
“We do the central baseline, because you can have a policy, but even translating that into those controls is complex, because what does it mean (for each cloud)? So we try to take that load off you, and we are doing the policy centrally.”
Find vulnerabilities and predict attacks with a graph database
Microsoft has long maintained that defenders think in terms of the lists of their assets, while attackers think in graphs of how systems are connected so they can jump from the initial breach into more valuable services.
With the GCP connector, Microsoft Defender for Cloud can build a graph database of everything you have in the cloud across AWS, Azure and Google Cloud. Then, you can explore that to understand what data you have and where you can be attacked. Tamir calls this a “data aware security posture” that can find and protect sensitive data.
He added, “We’re taking all the data that we can scrape off your GCP buckets, and aligning them onto the assets in the graph. All your assets, inventory, vulnerabilities and configurations are now hooked on the assets in the graph and connected.”
The data is scanned for sensitive data (e.g., credit card details, social security numbers and any custom information types you’ve defined in Microsoft Purview) that you wouldn’t want to see lost in a data breach. “We’re using the data tagging that comes from the DLP (data loss prevention) side of the house so you can tag using the same policies,” he explained. “As we go through this data, we also scan and tag everything we see. And yet again, that’s another great layer that gets added to the graph.”
Your cloud servers and Defender Vulnerability Management containers, if you have them, (Figure A) are also scanned for secrets (i.e., credentials such as SSH private keys, access keys and SQL connection strings) that you shouldn’t store in the cloud, as well as known vulnerabilities. That won’t affect the performance of those workloads. “To make that graph complete, we also do agentless scanning because we need to analyze all the logs and all the data that comes in to enrich the graph,” Tamir explained.
Figure A
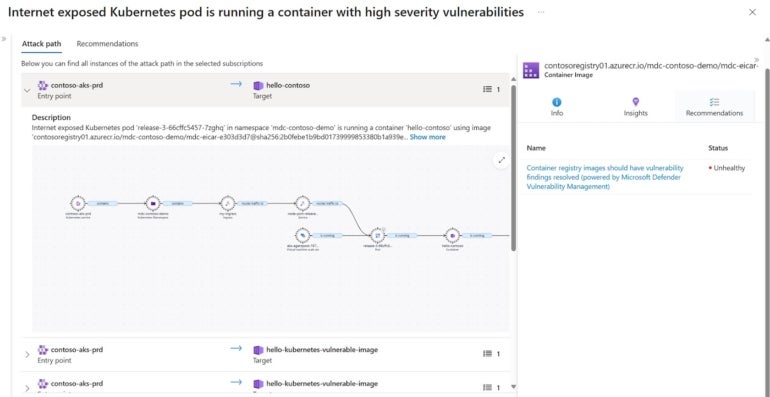
He added, “That all goes into a database, and you can query that database. We’re giving you the nice interconnected view of everything that you have.”
Putting the different pieces of information together like this helps you assess how serious a problem is. If you have a vulnerability in a virtual machine that has access to a service like Azure Key Vault, you’ll want to prioritize fixing that. Similarly, if the vulnerability is in a system that doesn’t have access to credentials but does have sensitive data, you should also care about it.
Attack path analysis
Exploring the graph as a defender lets you see all your resources the way an attacker would, but not everyone knows what to look for, so Microsoft is building tools to help security teams prioritize what needs fixing — the first is attack path analysis (Figure B).
Figure B
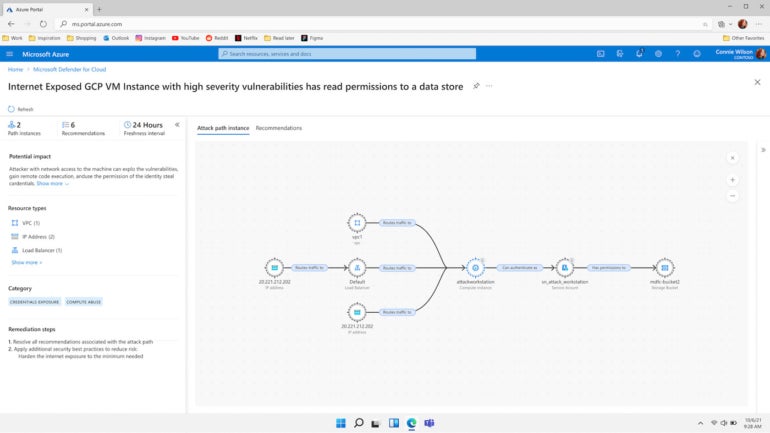
“Without doing any probing and just based on all the data that we accumulate in the graph, this is telling you the sets of possible attacks, and then we show you what would be the impact of this attack because you have a vulnerable set of VMs that have access to, say, key storage. “We can tell you what the potential outcome is, which helps you focus on the more important things,” Tamir pointed out. “And in the future, this will be a basis for us being able to tell where the attack is going, not just where it is right now.”
Protect cloud storage with new malware scanning
You don’t just want to stop attackers getting into your cloud storage — you also want to stop them from sneaking malware into your storage.
Traditionally, storage at rest doesn’t get scanned for malware because the assumption is the malware can’t execute when it’s sitting in a storage bucket – and if it does end up on an endpoint where it can be run, the defenses there will catch it. Microsoft Defender for Cloud can protect a wide range of devices, but that’s not enough to keep you safe, Tamir warned.
One customer allows their users to upload information for support agents to look at to help them. Tamir noted: “That information is immediately viewed by an agent, so the time that spends in the bucket storage before it actually gets consumed is really short, and the malware authors use it as a way of distributing malware. And in this case, it was ransomware.”
Other organizations have compliance rules like NIST and SWIFT for their data governance that mean they have to scan all data, but they don’t do it in real time. Tamir said, “They’ve been lazy scanning, and they have to set up all sorts of their own infrastructure and pull the data into like a VM and then scan it and then try to put it back. We can do that for them: We can do it quicker, we can do it without the hit of performance, and we can actually do it on upload.”
The new Malware Scanning in Defender for Storage is for Azure Blob storage only and will be available from September 1 as an optional extra for Defender for Storage, costing $0.15 per GB of data scanned.
Tamir said, “It’s not just file scanning, it’s not just hash, it’s not just IOCs (Indicators of Compromises); we’re actually doing polymorphic scanning.” And while the malware scanning is automated and delivered as a service rather than infrastructure you have to manage, you can still choose what happens when malware is detected. He added, “You can decide whether you just want us to tell you that it’s bad, or you want us to actually take an action, or you want to take the action somewhere else.”
Where Microsoft Defender for Cloud goes next
Defender for Storage
The next step for malware scanning in Defender for Storage will be scanning files more frequently, not just when they’re uploaded, to look for malware identified since then. Tamir suggested, “There are more polymorphic chains of malware that we discover every day.” The scale of cloud storage makes that a challenge. “These are really huge buckets; (if you’re) scanning them periodically, you will never get to the end, so we need to find a smart way of scanning them, whether it’s on access or some other trigger.”
How AI and automation could help
There are also a lot more opportunities to use the information in the graph that Defender for Cloud builds to protect customers, making it easier to avoid mistakes in the security and configuration settings that protect you, and do more.
“In general, in Microsoft (products) we have a lot of places where you set policies and not enough coordination between them,” Tamir noted. “If I set DLP policies, I want to set them centrally in one place – maybe it’s Microsoft Purview. And then I want that to move across all of my assets, and every enforcement point that I have should yield to that policy rather than me having to go and set those policies individually.”
Not only does he want applying those policies to take a lot less work, but instead of manually checking and applying the right security baseline, automation and AI could do more of the work of setting the right policies in the first place, he suggested.
Tamir added, “With cloud, people started the right way, saying instead of dealing with things post breach, let’s set the configurations right to begin with – and then we found out that the configuration problem is just as big!”
“This whole notion of shift left that everybody’s talking about; we still have a lot of manual steps in it – a lot of reasoning people need to do,” Tamir said. “I think there’s a revolution that must come in two parts. One, there needs to be more automation controlled stuff than human controlled stuff; automation will be really critical here because the information density is impossible.” The second step will be to add AI to automation. Tamir stated, “I think it will be a really good challenge for things like generative AI, for reasoning over things that are complex in the sense that they seem the same, but they’re not necessarily the same.”
Tamir concluded, “When people ask me, can I take my sets of compliance that are overlapping, and then tell me what the common denominator is for all of them, and what should I do to do that? I think that’s a problem that is primed well for tools like generative AI.”

